[ad_1]

VMware has released security updates to address a critical severity vulnerability affecting ESXi, Workstation, Fusion, and Cloud Foundation, and a critical severity command injection flaw impacting vRealize Network Insight.
VMware ESXi Heap Out of Bounds Write Vulnerability is Tracked as CVE-2022-31705 and received a CVSS v3 severity rating of 9.3.
“A malicious actor with local administrative privileges on a virtual machine can exploit this issue to execute code as the virtual machine’s VMX process running on the host,” mentions the security consulting.
“On ESXi, the exploitation is contained in the VMX sandbox whereas, on Workstation and Fusion, it can lead to code execution on the machine where Workstation or Fusion is installed.”
The vulnerability affects the following products:
ESXi 8.0 (Fixed in ESXi 8.0a-20842819)
ESXi 7.0 (fixed in 7.0U3i-20842708)
Fusion 12.x (fixed in 12.2.5)
Workstation 16.x (Fixed in 16.2.5)
Cloud Foundation 4.x/3.x (Fixed in KB90336)
VMware Fusion 13.x and Workstation 17.x are not affected by the flaw.
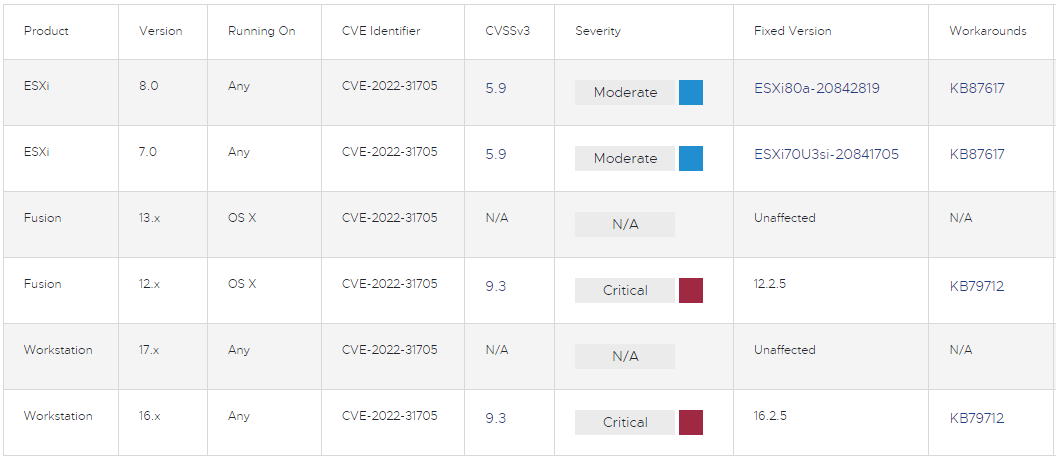
Since CVE-2022-31705 is in the USB 2.0 Controller (EHCI), the recommended workaround for those unable to apply the security update is to remove the USB Controller from their instances.
VMware released step by step instructions on how to apply the workaround on a VMware ESXi virtual machine, which also applies to the Cloud Foundation suite.
For VMware Workstation and VMware Fusion, follow these steps:
For Fusion:
- Select Window > Virtual Machine Library.
- Select a virtual machine in the Virtual Machine Library window and click Settings.
- Under Removable Devices in the Settings window, click USB and Bluetooth.
- Under Advanced USB Options, click Remove USB Controller.
- Click Delete in the confirmation dialog.
For workstation:
- Select a virtual machine in the Library pane and select VM > Settings.
- In the Virtual Machine Settings dialog, navigate to the Hardware tab.
- Select the USB Controller entry and click Remove.
On a separate security bulletinVMware provides details on CVE-2022-31702a critical severity vulnerability (CVSS v3: 9.8) that allows command injection into the vRNI REST API of vRealize Network Insight versions 6.2 through 6.7.
The same security advisory mentions a less severe directory traversal flaw (CVSS v3: 7.5), CVE-2022-31703, which could allow an attacker to read arbitrary files on the server. This flaw affects the same product versions mentioned above.
VMware vRealize Network Insight 6.8.0 is not affected by these vulnerabilities.
The software vendor has released security updates to address the issue for all affected versions, as listed in the table below.
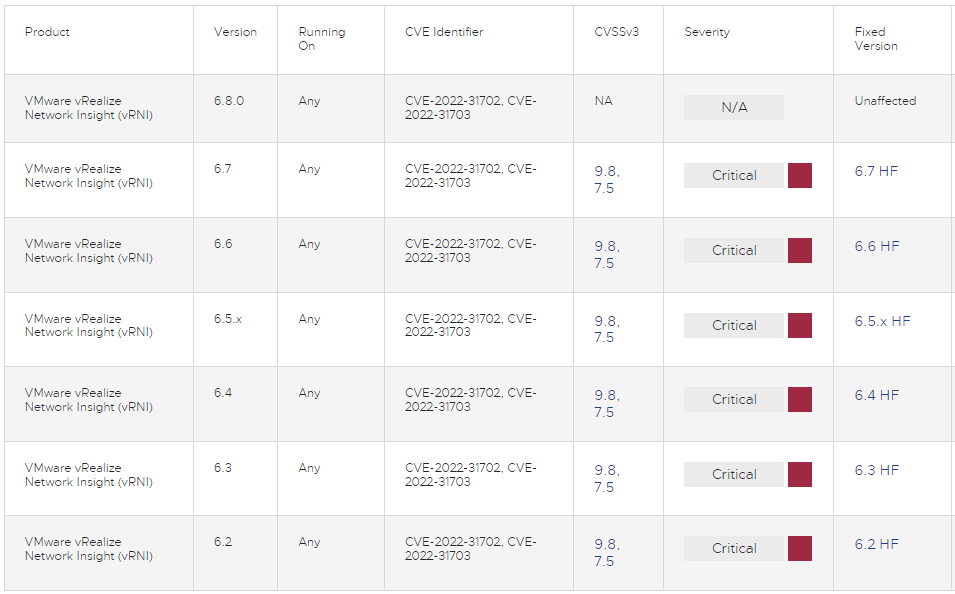
There is no workaround to fix these flaws, so the recommendation is to upgrade to the latest version available for your branch.
[ad_2]
Source link
