[ad_1]

Poland’s military counterintelligence service and its computer emergency response team have linked state-sponsored APT29 hackers, part of the Russian government’s Foreign Intelligence Service (SVR), to widespread attacks targeting NATO and European Union countries.
As part of this campaign, the cyber espionage group (also tracked as Cozy Bear and Nobelium) aimed to harvest information from diplomatic entities and foreign ministries.
“At the time of publication of the report, the campaign is still ongoing and in development,” a notice published today warns.
“The Military Counter-Intelligence Service and CERT.PL recommend that all entities that may be in the actor’s area of interest set up mechanisms to improve the security of the computer security systems used and to increase attack detection.”
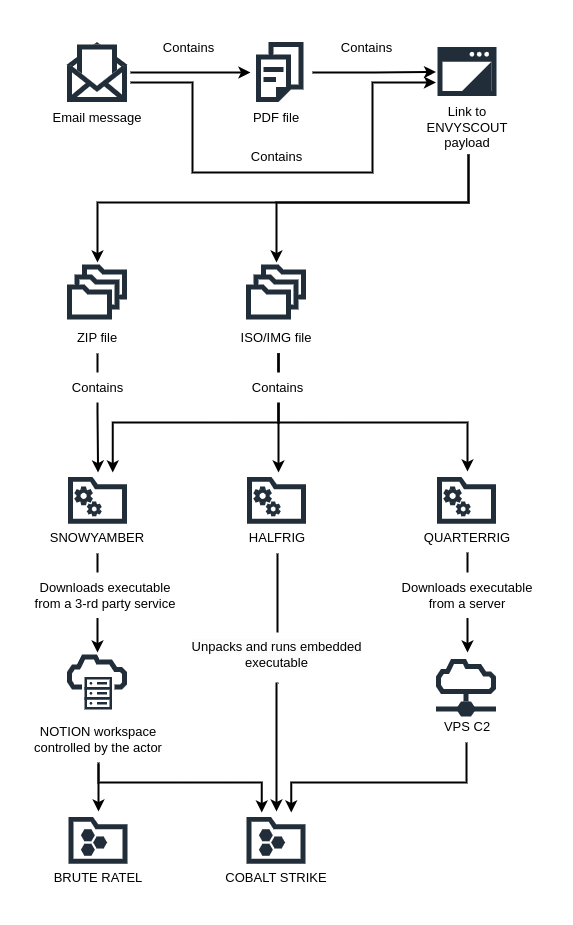
Attackers targeted diplomatic personnel using phishing emails posing as embassies of European countries with links to malicious websites or attachments designed to deploy malware via ISO, IMG and ZIP files .
Websites controlled by APT29 victims infected with EnvyScout dropper via HTML contrabandwhich helped deploy downloaders known as SNOWYAMBER And QUARTERRIG and designed to deliver additional malware, as well as a CobaltStrike Beacon stager named SEMI-RIGID.
SNOWYAMBER and QUARTERRIG were used for reconnaissance to help attackers assess the suitability of each target and determine whether they compromised honeypots or virtual machines used for malware analysis.
“If the infected workstation passed the manual check, the aforementioned downloaders were used to deliver and start COBALT STRIKE or BRUTE RATEL commercial tools”, a separate malware analysis report released today bed.
“HALFRIG, on the other hand, functions as a so-called loader – it contains the COBALT STRIKE payload and executes it automatically.”
APT29 is the hacking division of the Russian Foreign Intelligence Service (SVR) which was also related At SolarWinds Supply Chain Attack which led to the compromise of several US federal agencies three years ago.
Since then, the hacking group hacked the networks of other organizations using stealth malware that went undetected for years, including new malware being tracked as TrailBlazer and a GoldMax Linux backdoor variant.
Unit 42 also observed the Brute Ratel adversary attack simulation tool being used in the attacks suspected of being linked to Russian cyber-spies SVR.
More recently, Microsoft reported that the APT29 Hackers Use New Malware able to hijack Active Directory Federation Services (ADFS) to log in as anyone in Windows systems.
They also targeted Microsoft 365 accounts in NATO countries in attempts to access foreign and orchestrated policy information a wave of phishing campaigns targeting governments, embassies and senior officials across Europe.
[ad_2]
Source link
