[ad_1]

This week we have several reports of new ransomware families targeting the enterprise, named Cactus and Akira, both of which are increasingly active as they target the enterprise.
THE Operation Cactus launched in March and was found to exploit VPN vulnerabilities to access corporate networks.
The encryptor requires an encryption key to be passed on the command line to decrypt the configuration file used by the malware. If the correct configuration key is not passed, the encryptor will stop and nothing will be encrypted.
This method is to evade detection by security researchers and anti-virus software.
BleepingComputer too reported on Akira ransomwarea new operation launched in March which quickly claimed sixteen victims on its data leak site.
Operation Akira uses a retro data leak site that requires you to enter commands as if you were using a Linux shell.
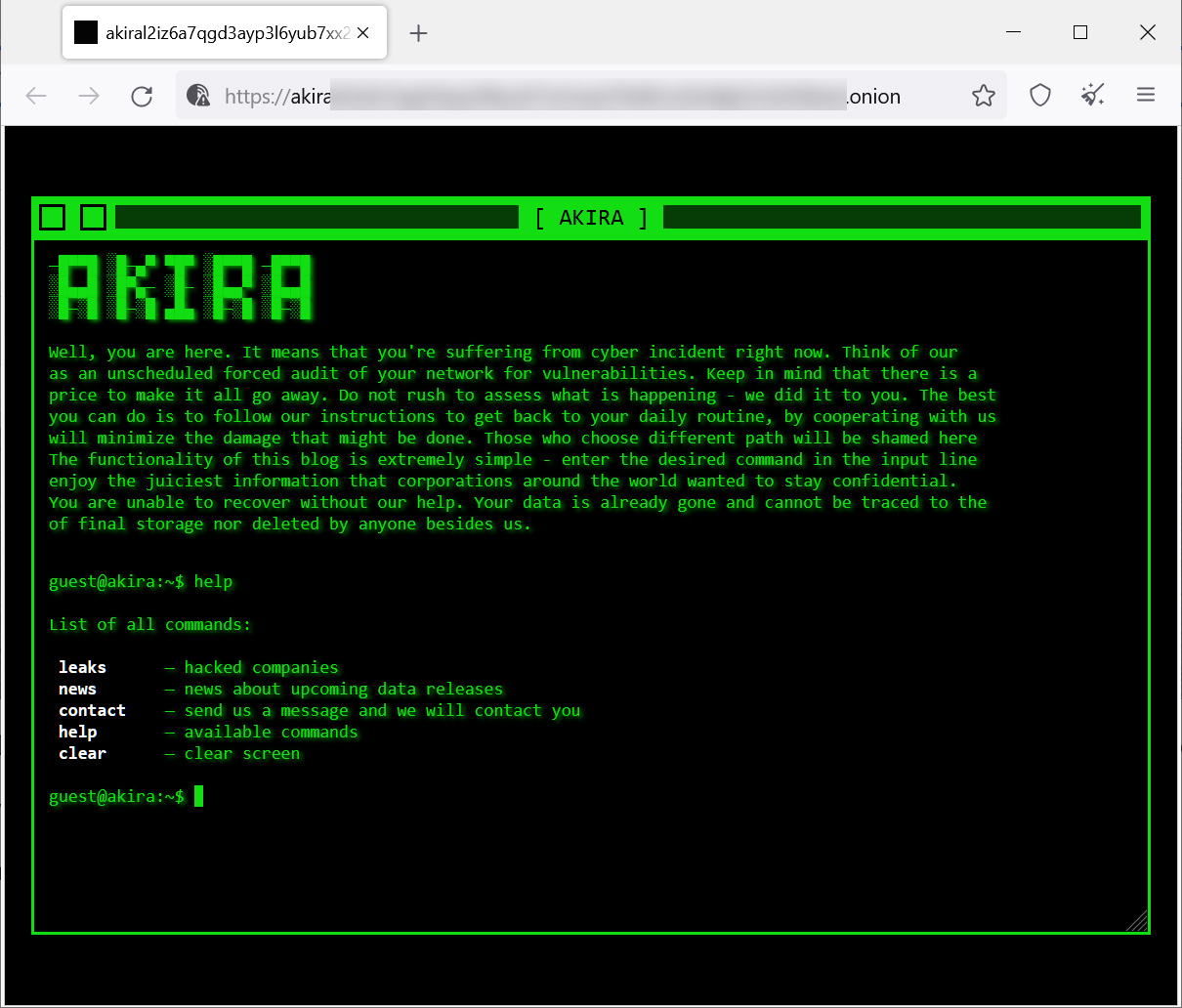
Source: BleepingComputer
We also discovered new attacks and important developers in previous ones.
On May 7, a multinational automation company ABB was attacked by Black Basta ransomwaredisrupting their network and factories.
ABB is the developer of many SCADA and industrial control (ICS) systems for energy suppliers and manufacturing, raising concerns about data theft and content.
Last week, news also revealed that the Money Message ransomware operation released source code owned by MSI, which contained private keys for Intel Boot Guard.
binary notified that these keys have leaked could be used to digitally sign UEFI malware that can bypass Intel Boot Guard on MSI devices.
Finally, researchers and law enforcement released new reports:
Contributors and those who provided new ransomware information and stories this week include: @PolarToffee, @malwhunterteam, @Ionut_Ilascu, @demonslay335, @struppigel, @malwareforme, @BleepinComputer, @billtoulas, @FourBytes, @serghei, @VK_Intel, @fwosar, @LawrenceAbrams, @Seifreed, @jorntvdw, @DanielGallagher, @LabsSentinel, @BrettCallow, @matrosov, @binarly_io, @Checkmarx, @KrollWire, @yinzlovecyberAnd @pcrisk.
May 7, 2023
Meet Akira — A New Ransomware Operation Targeting the Enterprise
The new Akira ransomware operation has slowly built up a list of victims as they break into corporate networks around the world, encrypt files, and then demand million-dollar ransoms.
New Cactus ransomware encrypts itself to evade antivirus
A new ransomware operation called Cactus exploits vulnerabilities in VPN appliances for initial access to the networks of “large commercial entities”.
New variant of STOP ransomware
Risk found a new STOP ransomware variant that adds the .qore extension.
May 8, 2023
Intel investigates Intel Boot Guard private key leak after MSI breach
Intel is investigating the leak of alleged private keys used by the Intel Boot Guard security feature, which may impact its ability to block the installation of malicious UEFI firmware on MSI devices.
May 9, 2023
New variant of GlobeImposter ransomware
PCrisk has found a new variant of GlobeImposter ransomware that adds the .Suffering extension and drops a ransom note named how_to_back_files.html.
New Solix ransomware
PCrisk has found a new ransomware variant that adds the .Solix extension.
New MedusaLocker ransomware
PCrisk has found a new ransomware variant that adds the .newlocker extension and drops a ransom note named HOW_TO_RECOVER_DATA.html.
New BrightNite ransomware
PCrisk has found a new ransomware variant that adds the .BrightNight extension and drops a ransom note named README.txt.
New variant of STOP ransomware
PCrisk has found a new STOP ransomware variant that adds the .notch extension.
May 10, 2023
New ransomware decryptor recovers data from partially encrypted files
A new “White Phoenix” ransomware decryptor allows victims to partially recover files encrypted by ransomware strains that use intermittent encryption.
New variant of Xorist ransomware
PCrisk has found a new Xorist ransomware variant that adds the .SIGSCH extension and drops a ransom note named README_GISSCH.txt.
New Army Signal ransomware
PCrisk has found a new Xorist ransomware variant that adds the .zip3rs extension.
May 11, 2023
Babuk code used by 9 ransomware gangs to encrypt VMWare ESXi servers
A growing number of ransomware operations are adopting leaked Babuk ransomware source code to create Linux encryptors targeting VMware ESXi servers.
Multinational tech company ABB hit by Black Basta ransomware attack
Swiss multinational ABB, a leading provider of electrification and automation technology, suffered a Black Basta ransomware attack, which reportedly impacted business operations.
New variant of STOP ransomware
PCrisk has found a new STOP ransomware variant that adds the .gatz extension.
May 12, 2023
FBI: Bl00dy Ransomware Targets Educational Organizations in PaperCut Attacks
The FBI and CISA have issued a joint advisory to warn that the Bl00dy Ransomware gang is also actively exploiting a PaperCut remote code execution vulnerability to gain initial access to networks.
It’s all for this week ! I hope everyone is having a good weekend!
[ad_2]
Source link
