[ad_1]

Hackers are actively exploiting a recently patched vulnerability in the WordPress Advanced Custom Fields plugin approximately 24 hours after a proof-of-concept (PoC) exploit was released.
The vulnerability in question is CVE-2023-30777, a high-severity cross-site scripting (XSS) flaw that allows unauthenticated attackers to steal sensitive information and elevate privileges on impacted WordPress sites.
The flaw was discovered by website security firm Patchstack on May 2, 2023, and was disclosed with a proof-of-concept exploit. May 5a day after the plugin vendor released a security update with version 6.1.6.
As Akamai’s Security Intelligence Group (SIG) reported yesterday, beginning May 6, 2023, it observed significant forensic and exploit activity using the sample code provided in the Description of Patchstack.
“Akamai SIG analyzed XSS attack data and identified attacks starting within 24 hours of PoC exploit publication,” read the report.
“What’s particularly interesting about this is the request itself: the threat actor copied and used the editorial staff’s Patchstack sample code.”
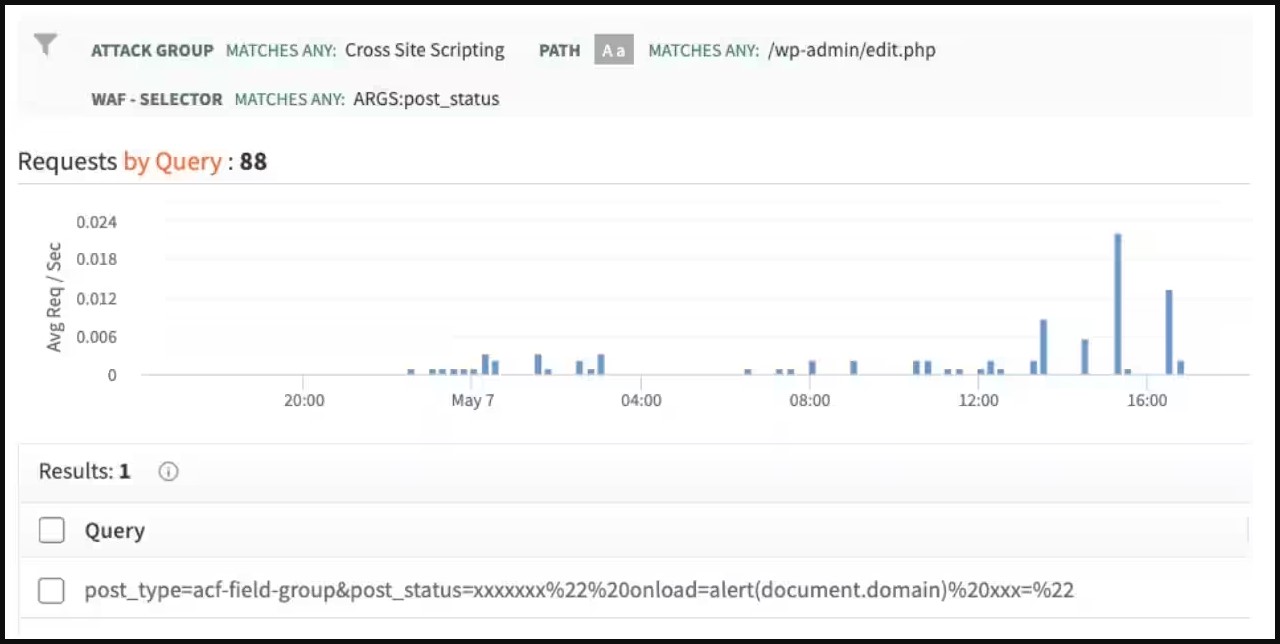
Considering that over 1.4 million websites using the impacted WordPress plugin have not been upgraded to the latest version, based on statistics from wordpress.orgattackers have a fairly large attack surface to explore.
The XSS flaw requires the involvement of a logged-in user who has access to the plugin to execute malicious code on their browser that will give attackers privileged access to the site.
Malicious analytics indicate that this mitigating factor does not deter threat actors who believe they can overcome it through basic trickery and social engineering.
Additionally, the exploit works on the default configurations of the affected plugin versions, which increases threat actors’ chances of success without requiring additional effort.
WordPress site administrators using the vulnerable plugins are advised to immediately apply the available patch to protect themselves from ongoing scanning and exploit activities.
The recommended action is to upgrade the free and professional plugins “Advanced Custom Fields” to versions 5.12.6 (backported) and 6.1.6.
[ad_2]
Source link
