[ad_1]
The LockBit ransomware gang has released a free decryptor for the Hospital for Sick Children (SickKids), claiming that one of its members violated the rules by attacking the healthcare organization.
SickKids is a teaching and research hospital in Toronto that focuses on providing health care to sick children.
On December 18, the hospital suffered a ransomware attack that impacted internal and corporate systems, hospital phone lines and the website.
Although the attack only encrypted a few systems, SickKids said the incident caused delays in receiving lab and imaging results and resulted in longer wait times for patients.
December 29, SickKids announcement that it had restored 50% of its priority systems, including those causing delays in diagnosis or treatment.
The LockBit gang apologizes for the attack
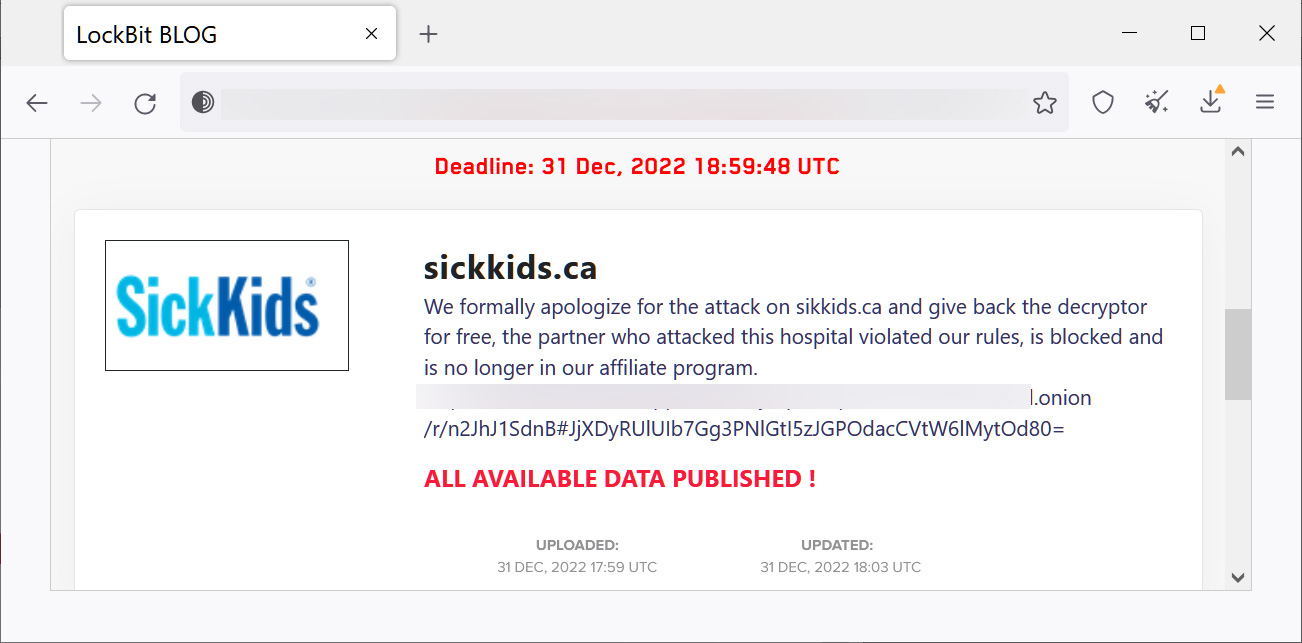
As noted for the first time By threat intelligence researcher Dominic Alvieri, Two days after SickKids’ last announcement, the LockBit ransomware gang has apologized for the attack on the hospital and released a decryptor for free.
“We officially apologize for the attack on sikkids.ca and are returning the decryptor for free, the partner who attacked this hospital violated our rules, is blocked and is no longer part of our affiliate program,” the gang said. ransomware.
BleepingComputer has confirmed that this file is freely available and claims to be a Linux/VMware ESXi decryptor. Since there is no additional Windows decryptor, this indicates that the attacker could only encrypt virtual machines on the hospital network.
Source: BleepingComputer
The LockBit operation functions as a Ransomware-as-a-Service, where operators maintain the encryptors and websites, and operation affiliates or members breach victims’ networks, steal data and encrypt devices.
Under this arrangement, LockBit operators keep around 20% of all ransom payments and the rest goes to the affiliate.
While the ransomware operation allows its affiliates to encrypt pharmaceutical companies, dentists and plastic surgeons, it prohibits its affiliates from encrypting “medical institutions” where attacks could result in death.
“It is prohibited to encrypt institutions where damage to files could result in death, such as heart centers, neurosurgery departments, maternity hospitals and the like, i.e. institutions where surgeries on high-tech equipment using computers can be carried out,” explains the policies of the ransomware operation.
Stealing data from any medical institution is permitted by policy.
According to the ransomware gang, as one of its affiliates encrypted the hospital devices, they were removed from the operation and a decryptor was offered for free.
However, this does not explain why LockBit did not provide a decryptor earlier as patient care was impacted and SickKids struggled to restore operations since the 18th.
Also, LockBit has a habit of encrypting hospitals and not providing encryptors, as seen in its attack against the Center Hospitalier Sud Francilien (CHSF) in France, where a ransom of 10 million dollars was demanded, and patient data finally leaked.
The attack on the French hospital led to referral of patients to other medical centers and postponement of surgeries, which could have posed significant risks to patients.
BleepingComputer had contacted LockBit at the time to understand why they were demanding a ransom from the CHSF, even though it was against policy, but never received a response.
[ad_2]
Source link
