[ad_1]

ALPHV ransomware operators got creative with their extortion tactics and, in at least one case, created a replica of the victim’s site to post stolen data on.
It appears that ALPHV, also known as BlackCat ransomwareis known for testing new extortion tactics as a way to pressure and shame their victims into paying.
While these tactics may not be successful, they introduce an ever-expanding threat landscape that victims must navigate.
Hackers make it easier to access stolen data
On December 26, the threat actor posted on his hidden data leak site on the Tor network that he had compromised a financial services company.
As the victim did not respond to the threat actor’s requests, BlackCat released all stolen files as punishment – a standard step for ransomware operators.
As a departure from the usual process, the hackers decided to also leak the data to a site that mimics the victim’s in terms of appearance and domain name.
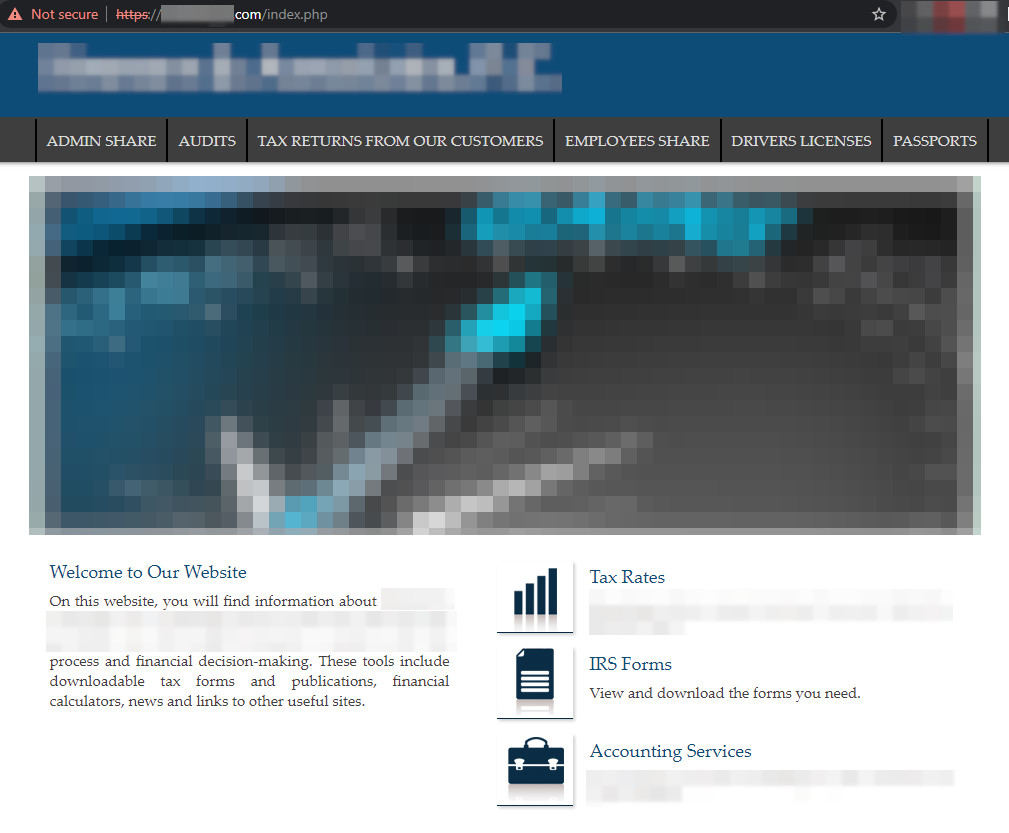
source: BleepingComputer
The pirates did not keep the original headings of the site. They used their own headers to organize the leaked data.
The cloned site is on the clear web to ensure the wide availability of the stolen files. It currently displays various documents, memos to staff, payment forms, employee information, asset and expense data, financial data for partners, and passport scans.
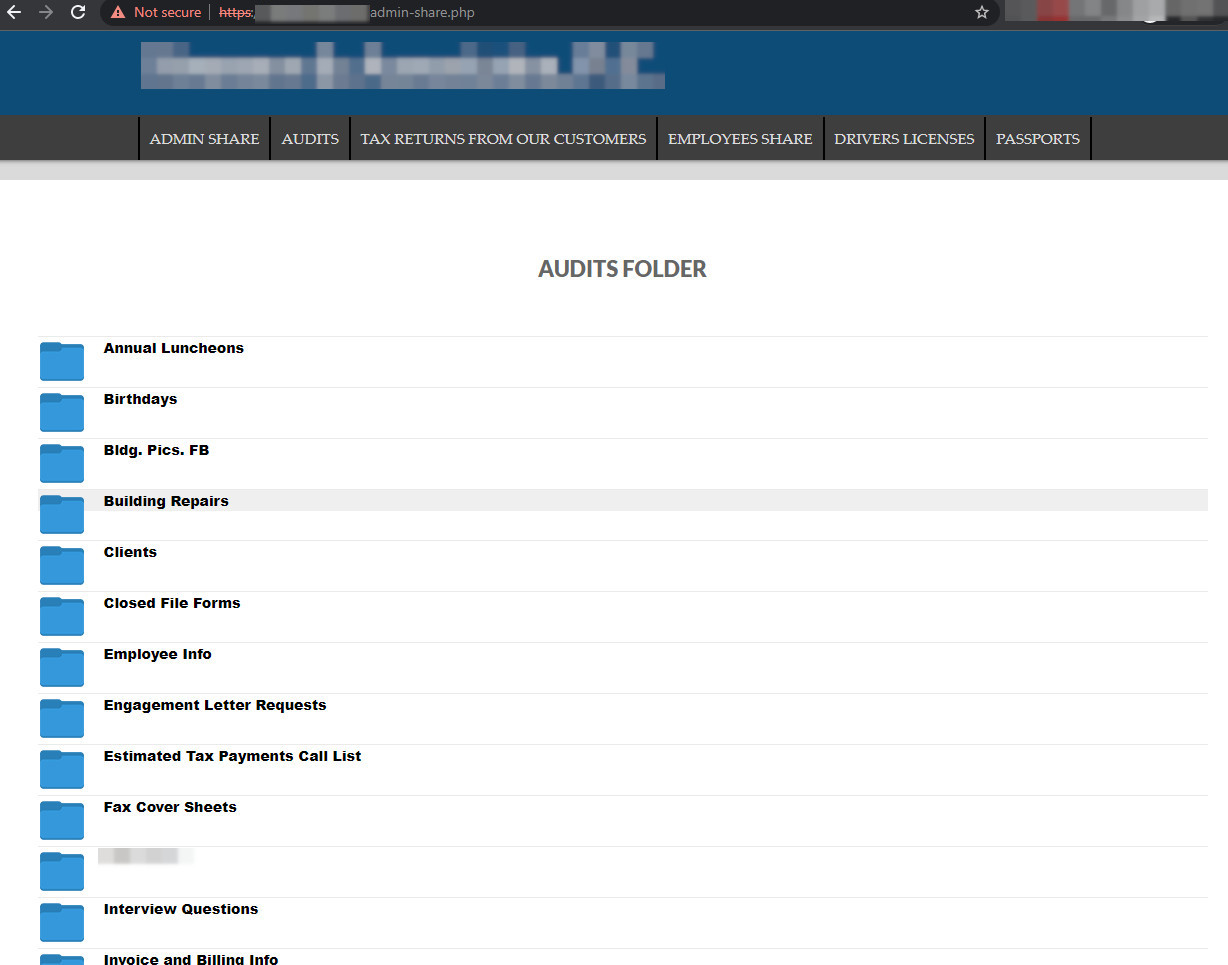
source: BleepingComputer
In total, there are 3.5 GB of documents. ALPHV also shared the stolen data on a file-sharing service that allows anonymous downloading and distributed the link on its leak site.
New trend
Brett Callowthreat analyst from cybersecurity firm Emsisoft, said sharing the data on a typosquatted domain would be a bigger concern for the victimized company than distributing the data through a website on the Tor network, which is mostly known to the public. infosec community.
“I wouldn’t be at all surprised if Alphv tried to arm the company’s customers by directing them to this website” Brett Callow
This tactic could represent the start of a new trend that could be adopted by other ransomware gangs, especially since the costs to do so are far from significant.
Ransomware operations have always looked for new options to extort their victims. Between publishing the name of the hacked company, stealing data and threatening to publish it unless the ransom is paid, and the DDoS threat, this tactic could represent the start of a new trend that could be adopted by many. other ransomware gangs, especially since the costs to do so are far from significant.
The success of this scheme is unclear at this time, but it exposes the breach to a wider audience, putting the victim in a more difficult position as their data is readily available without any restrictions.
ALPHV is the first ransomware gang to create a search for specific data stolen from their victims. The pages are for customers and employees of their victims to check if their data has been stolen by the hackers.
[ad_2]
Source link
