[ad_1]

Microsoft warns of a phishing campaign targeting accounting firms and tax preparers with remote access malware allowing initial access to corporate networks.
As the United States comes to the end of its annual tax season, accountants are scrambling to gather tax documents from clients in order to complete and file their tax returns.
For this reason, now is a great time for hackers to target tax preparers, hoping they are mistakenly opening malicious files that they would typically be more careful with when they are less busy.
That’s exactly what Microsoft sees in a new phishing scam targeting tax professionals to install the Remcos remote access Trojan malware.
“Ahead of Tax Day in the United States, Microsoft observed phishing attacks targeting accounting and tax preparation companies to deliver the Remcos Remote Access Trojan (RAT) and compromise the target networks from February this year,” Microsoft warns in a new report.
Target tax professionals
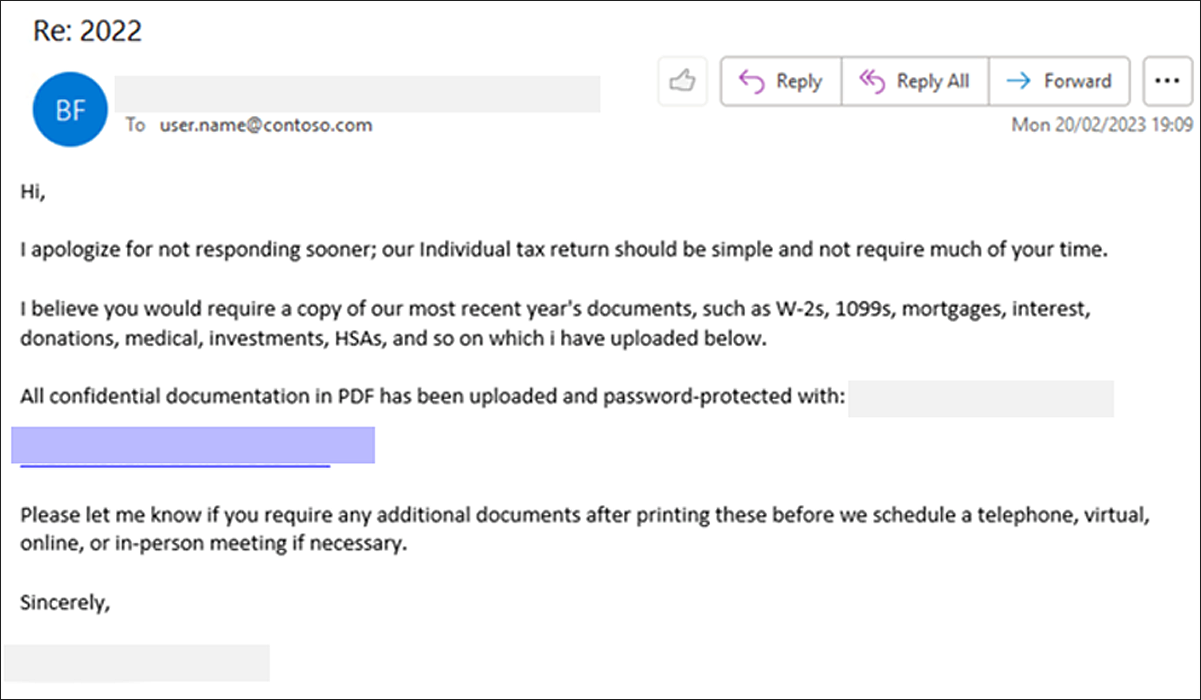
The phishing campaign starts with emails that pretend to be customers sending the necessary documents to complete their declaration.
“I apologize for not responding sooner; our individual tax return should be simple and not require much of your time,” reads one phishing email seen by Microsoft.
“I think you would need a copy of our most recent year’s documents, such as W-2s, 1099s, mortgages, interest, gifts, medical investments, HSAs, etc. which I uploaded below.”
Source: Microsoft
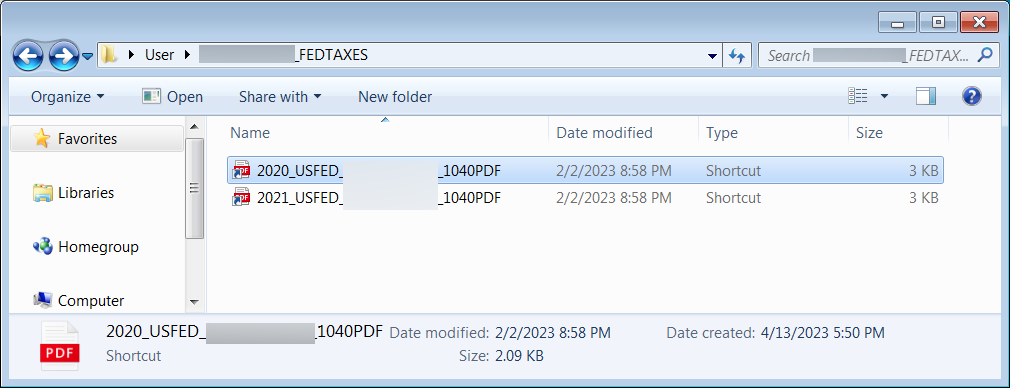
These phishing emails contain links that use click-tracking services to evade detection by security software and ultimately lead to a file hosting site that downloads a ZIP archive.
This ZIP archive contains many files pretending to be PDFs for various tax forms, but are actually Windows shortcuts.
Source: Microsoft
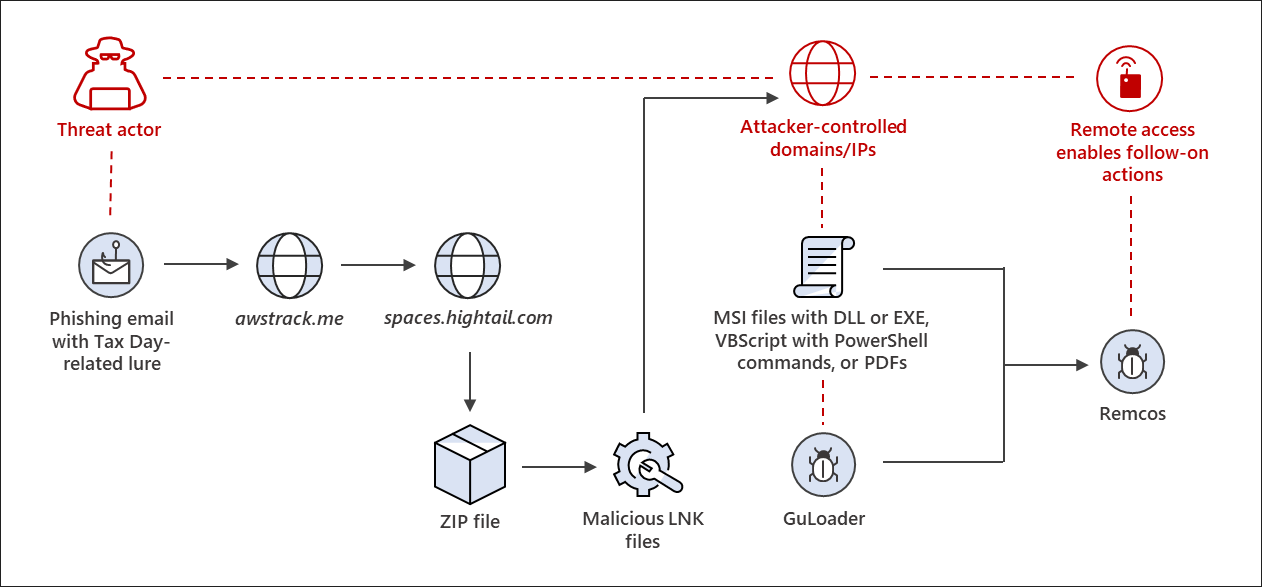
When double-clicked, these Windows shortcuts run PowerShell to download a heavily obfuscated VBS file from a remote host, which is saved to C:\Windows\Tasks\ and executed.
At the same time, the VBS script will download a decoy PDF file and open it in Microsoft Edge so as not to arouse the suspicion of the targeted person.
Microsoft says these VBS files will download and run the GuLoader malware, which in turn installs the Remcos remote access Trojan.
Source: Microsoft
Remcos is a remote access trojan that threatens actors commonly used in phishing campaigns to gain initial access to corporate networks.
Using this access, threat actors can spread further across the network, steal data, and deploy other malware to a device.
Microsoft says that while phishing campaigns typically use tax-related themes, this campaign is unusual because it only targets businesses and individuals responsible for preparing tax returns.
“While social engineering lures like this are common around Tax Day and other major news events, these campaigns are specific and targeted in an uncommon way.”
“The targets of this threat are exclusively organizations that deal in tax preparation, financial services, CPAs and accounting firms, and professional services firms dealing with accounting and tax.”
As accountants hold highly sensitive data for individuals and businesses, a data breach in this type of organization could significantly harm a large group of people.
Since the initial loaders of this campaign’s malware are malicious files masquerading as PDF files, we always recommend users enable display of file extensions in Windows so that they can identify suspicious files.
Unfortunately, Windows Shortcuts are a special file type that uses the .lnk file extension but does not display the file extension when viewed in File Explorer.
This behavior makes it harder to detect that a file is a disguised shortcut. However, the list of files in File Explorer in “Details” mode will show that it is a Windows shortcut, which will make it a little easier to spot.
Ultimately, no one should click on links in emails or open attachments unless they confirm whether they are from a legitimate contact. Otherwise, delete the email.
[ad_2]
Source link
