[ad_1]

A new ransomware gang named “Money Message” has emerged, targeting victims worldwide and demanding million dollar ransoms for withholding data and releasing a decryptor.
The new ransomware was first reported by a victim on the IT Forums on March 28, 2023, with Zscaler’s ThreatLabz shortly after sharing information on Twitter.
Currently, the threat actor lists two victims on its extortion site, one of which is an Asian airline with annual revenue of around $1 billion. Additionally, the threat actors claim to have stolen files from the company and include a screenshot of the accessed file system as evidence of the breach.
.jpg)
During its investigation, BleepingComputer saw evidence of a potential Money Message breach on a well-known hardware vendor. However, we have not been able to independently confirm the attack with the company at this time.
How Money Message encrypts a computer
The Money Message Encryptor is written in C++ and includes a built-in JSON configuration file that determines how a device will be encrypted.
This configuration file includes folders to prevent from being encrypted, extension to add, services and processes to terminate, if logging is enabled, and domain logins and passwords that may be used to encrypt other devices.
In the sample analyzed by BleepingComputer, the ransomware will not encrypt files in the following folders:
C:\msocache,C:\$windows.~ws,C:\system volume information,C:\perflogs,C:\programdata,C:\program files (x86), C:\program files,C:\$windows.~bt,C:\windows,C:\windows.old,C:\boot]Once launched, it will delete volume shadow copies using the following command:
cmd.com /c vssadmin.exe delete shadows /all /quiet to clear shadow volume copiesThe ransomware will then terminate the following process:
sql.exe,oracle.exe,ocssd.exe,dbsnmp.exe,synctime.exe,agntsvc.exe,isqlplussvc.exe,xfssvccon.exe,mydesktopservice.exe,ocautoupds.exe,encsvc.exe,firefox.exe,tbirdconfig.exe,mdesktopqos.exe,ocomm.exe,dbeng50.exe,sqbcoreservice.exe,excel.exe,infopath.exe,msaccess.exe,mspub.exe,onenote.exe,outlook.exe,powerpnt.exe,steam.exe,thebat.exe,thunderbird.exe,visio.exe,winword.exe,wordpad.exe,vmms.exe,vmwp.exeThen the ransomware stops the following Windows services:
vss, sql, svc$, memtas, mepocs, sophos, veeam, backup, vmmsWhile encrypting files, it will not add any extension, but this may change depending on the victim. According to a security researcher rivalrythe encryptor uses ChaCha20/ECDH cipher when encrypting files.
The only files excluded from encryption by default are:
- desktop.ini
- ntuser.dat
- inch.db
- iconcache.db
- ntuser.ini
- ntldr
- bootfont.bin
- ntuser.dat.log
- bootsect.bak
- boot.ini
- autorun.inf
In our tests, file encryption by Money Message was quite slow compared to other encryptors.
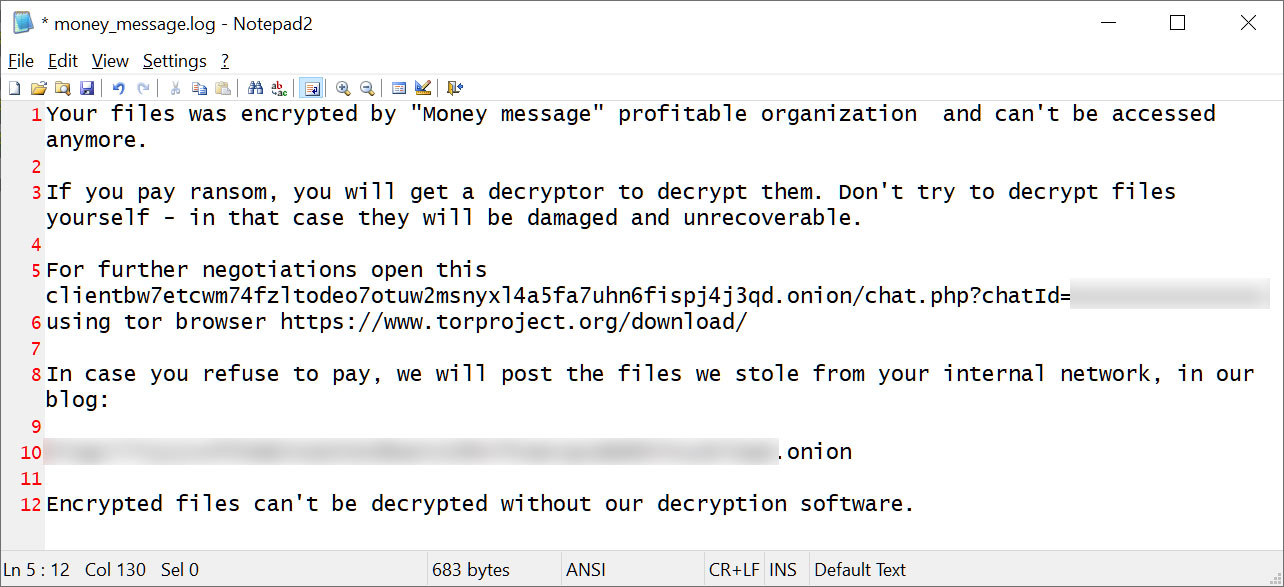
After encrypting the device, the ransomware will create a ransom note named money_message.log which contains a link to a TOR trading site used to negotiate with threat actors.
The ransomware will also warn that it will publish all stolen data on its data leak site if a ransom is not paid.
The emergence of the Money Message ransomware group introduces an additional threat that organizations need to watch out for.
Although the cipher used by the group does not appear to be sophisticated, the operation has been confirmed to be successful in stealing data and encrypting devices during their attacks.
Experts will analyze the ransomware, and if a weakness in the encryption is discovered, we will update this post.
[ad_2]
Source link
