[ad_1]

A previously unknown campaign involving the Hotabot botnet malware has targeted Spanish-speaking users in Latin America since at least November 2020, infecting them with a banking Trojan and spam tool.
The malware allows operators to take control of the victim’s Gmail, Outlook, Hotmail or Yahoo email accounts, steal email data and 2FA codes arriving in the inbox and send emails from phishing from compromised accounts.
The new Horabot operation was uncovered by analysts at Cisco Talos, who report that the threat actor behind it is likely based in Brazil.
Start with phishing
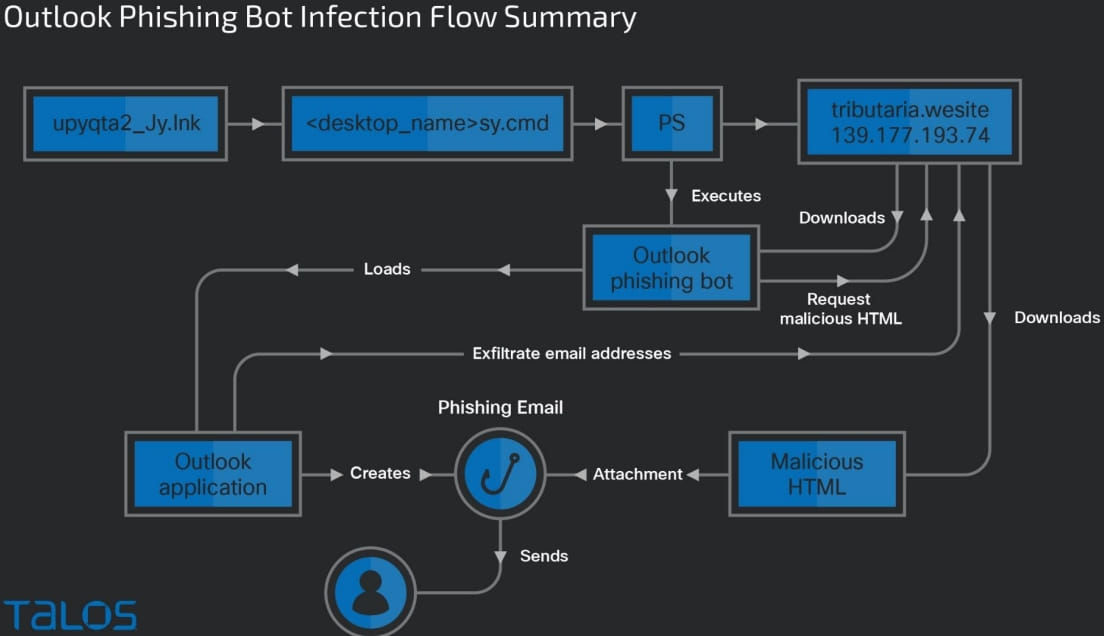
The multi-step infection chain begins with a tax-themed phishing email sent to the target, with an HTML attachment that is supposed to be a payment receipt.
Opening the HTML code launches a URL redirect chain that redirects the victim to an HTML page hosted on an AWS instance controlled by the attacker.
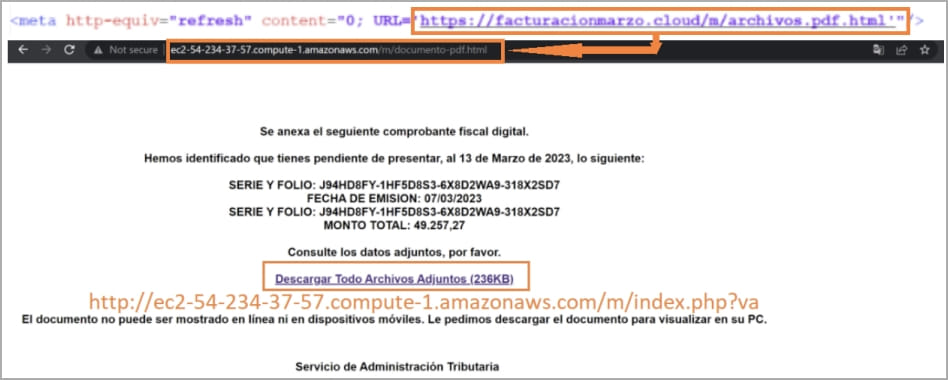
The victim clicks on the page’s hyperlink and downloads a RAR archive containing a batch file with a CMD extension, which downloads a PowerShell script that fetches Trojan DLLs and a set of legitimate executables from the C2 server .
These Trojans run to fetch the final two payloads from a different C2 server. One is a powershell download script and the other is the Horabot binary.
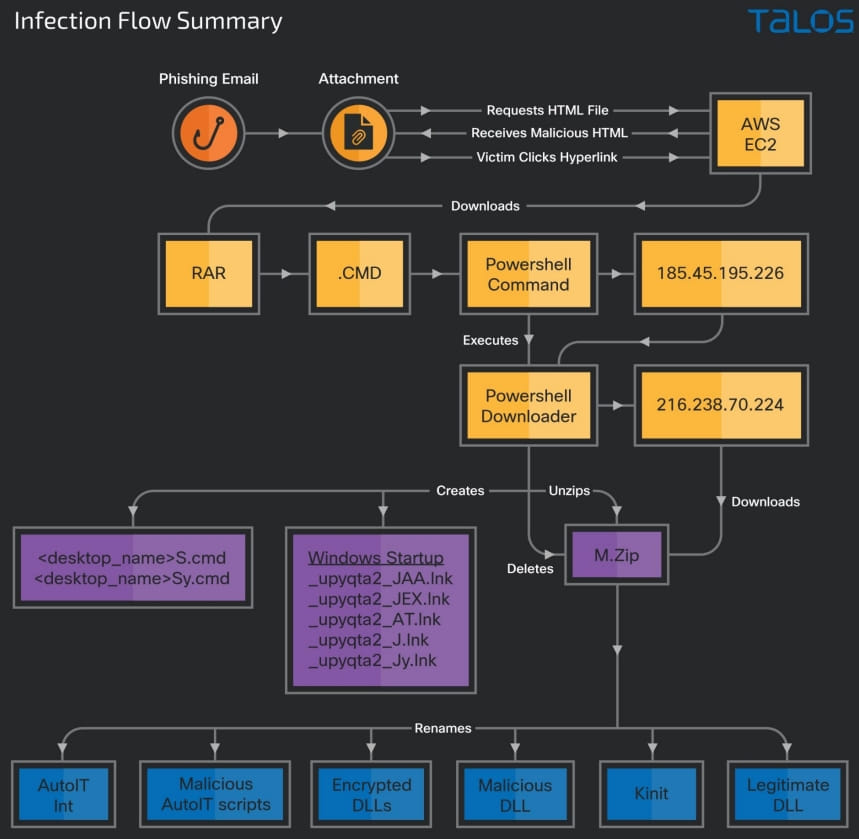
Banking Trojan
One of the DLL files in the downloaded ZIP, “jli.dll”, which is loaded by the “kinit.exe” executable, is a banking Trojan written in Delphi.
It targets system information (language, disk size, antivirus software, hostname, OS version, IP address), user credentials and activity data.
Additionally, the Trojan also provides its operators with remote access capabilities such as performing actions on files and can also perform keylogging, screenshot and event tracking of the mouse.
When the victim opens an application, the Trojan covers a fake window to trick victims into entering sensitive data such as online bank account credentials or one-time codes.
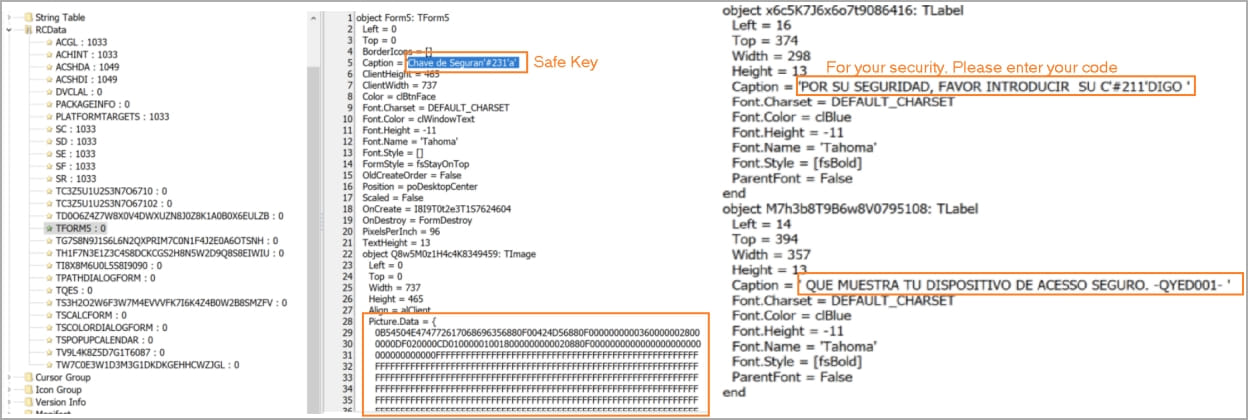
All information collected from the victim’s computer is sent to the attacker’s command and control server via HTTP POST requests.
Cisco explains that the Trojan has several built-in anti-analysis mechanisms to prevent it from running in sandboxes or alongside debuggers.
The ZIP archive also contains an encrypted spam tool DLL named “_upyqta2_J.mdat”, designed to steal credentials from popular webmail services such as Gmail, Hotmail, and Yahoo.
Once the credentials are compromised, the tool takes over the victim’s email account, generates spam emails and sends them to the contacts found in the victim’s mailbox, furthering the infection somewhat randomly .
This tool also offers keylogging, screen capture, and mouse event intercept or tracking functionality, functionally overlapping the banking Trojan, possibly for redundancy.
Horabot
The main payload dropped on victim’s system is Horabot, a documented PowerShell-based botnet that targets victim’s Outlook mailboxes to steal contacts and deliver phishing emails containing malicious HTML attachments.
The malware launches the victim’s desktop Outlook application to examine the address book and contacts from the mailbox contents.
“After initialization, the [Horabot] The script looks for Outlook data files in the victim profile’s Outlook application data folder,” explains Cisco in the report.
“It enumerates all folders and emails in victim’s Outlook data file and extracts email addresses from sender, recipients, CC and BCC fields of emails.”
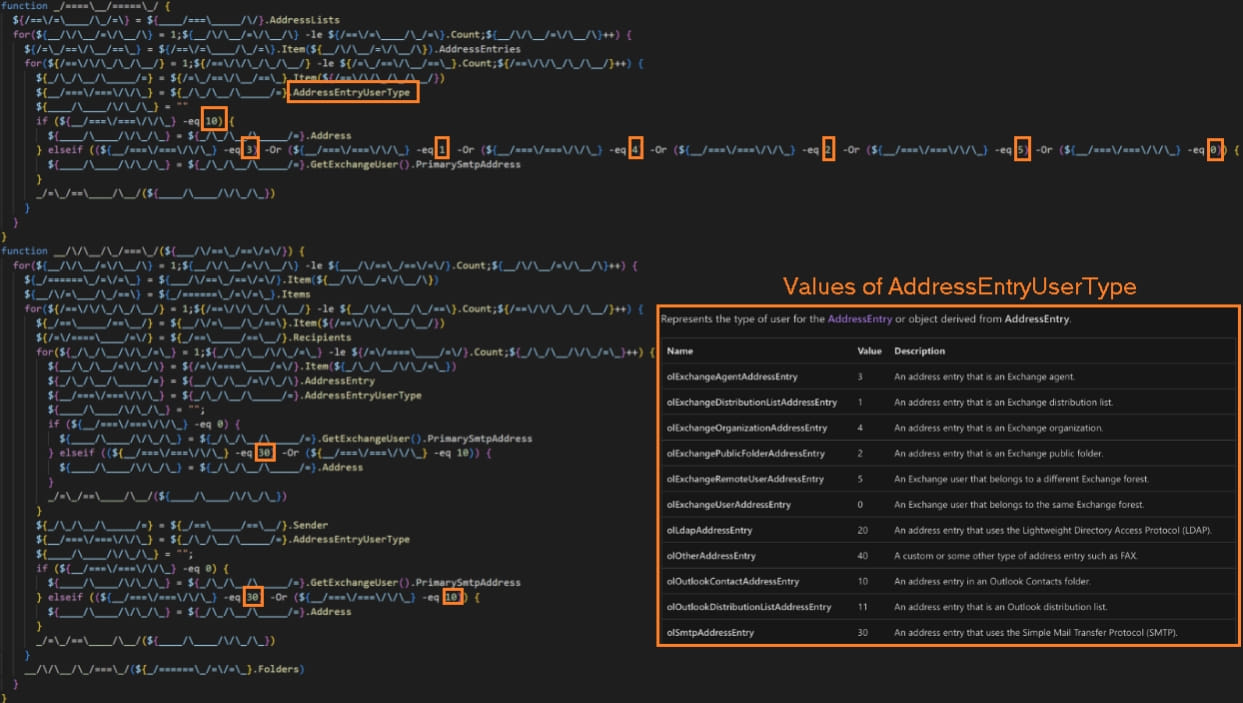
All extracted email addresses are written to an “.Outlook” file then encoded and exfiltrated to the C2 server.
Finally, the malware creates an HTML file locally, fills it with content copied from an external resource, and sends phishing emails to all extracted email addresses individually.
When the phishing email distribution process is complete, locally created files and folders are deleted to erase all traces.
Although this Horabot campaign primarily targets users in Mexico, Uruguay, Brazil, Venezuela, Argentina, Guatemala, and Panama, the same threat actors or collaborating actors could expand its reach to other markets to any time, using phishing themes written in English.
[ad_2]
Source link
