[ad_1]

A new DDoS-as-a-Service (DDoSaaS) platform named “Passion” has been used in recent attacks by pro-Russian hacktivists against medical institutions in the United States and Europe.
A DDoS (Distributed Denial of Service) attack occurs when threat actors send numerous requests and unwanted traffic to a target server to overwhelm the server and prevent it from responding to legitimate requests.
DDoSaaS platforms lease their available firepower to those looking to launch disruptive attacks on their targets, relieving them of the need to create their own large botnets or coordinate volunteer action.
Typically, these botnets are built by compromise vulnerable IoT devices such as routers and IP cameras, uniting them into a large swarm that generates malicious requests towards a particular target.
Radware discovered the Passion platform, and while its origins are unknown, the operation has distinctive ties to Russian hacking groups, including Killnet, MIRAI, Venom, and Anonymous Russia.
“The Passion Botnet was exploited in the January 27 attacks, targeting medical institutions in the United States, Portugal, Spain, Germany, Poland, Finland, Norway, the Netherlands and the United Kingdom in retaliation for sending tanks in support of Ukraine,” Radware researchers said.
A passion for DDoS
The operators of the Passion DDoS platform first promoted their service in early January 2023, carrying out several defacements on the sites of Japanese and South African organizations.

The service operates as a subscription, where “customers” can purchase desirable attack vectors, duration and intensity.
Passion offers the option of ten attack vectors, allowing subscribers to customize their attack to their needs and even combine vectors to circumvent the mitigations implemented by the target.
Supported attack methods are:
- Raw HTTP
- Crypto
- UAM Browser
- HTTPS mix
- The browser
- bypasses
- DNS l4
- Mixamp l4
- OVH-TCP l4
- TCP-Kill l4
As for the cost of the service, a seven-day subscription costs $30, a month costs $120, while a full year costs threat actors $1,440. Accepted payment methods include Bitcoin, Tether and Russian payment service QIWI.
Passion uses the Dstat.cc measurement service to showcase its L4 and L7 attack capabilities and effectiveness against DDoS mitigation vendors like CloudFlare and Google Shield.
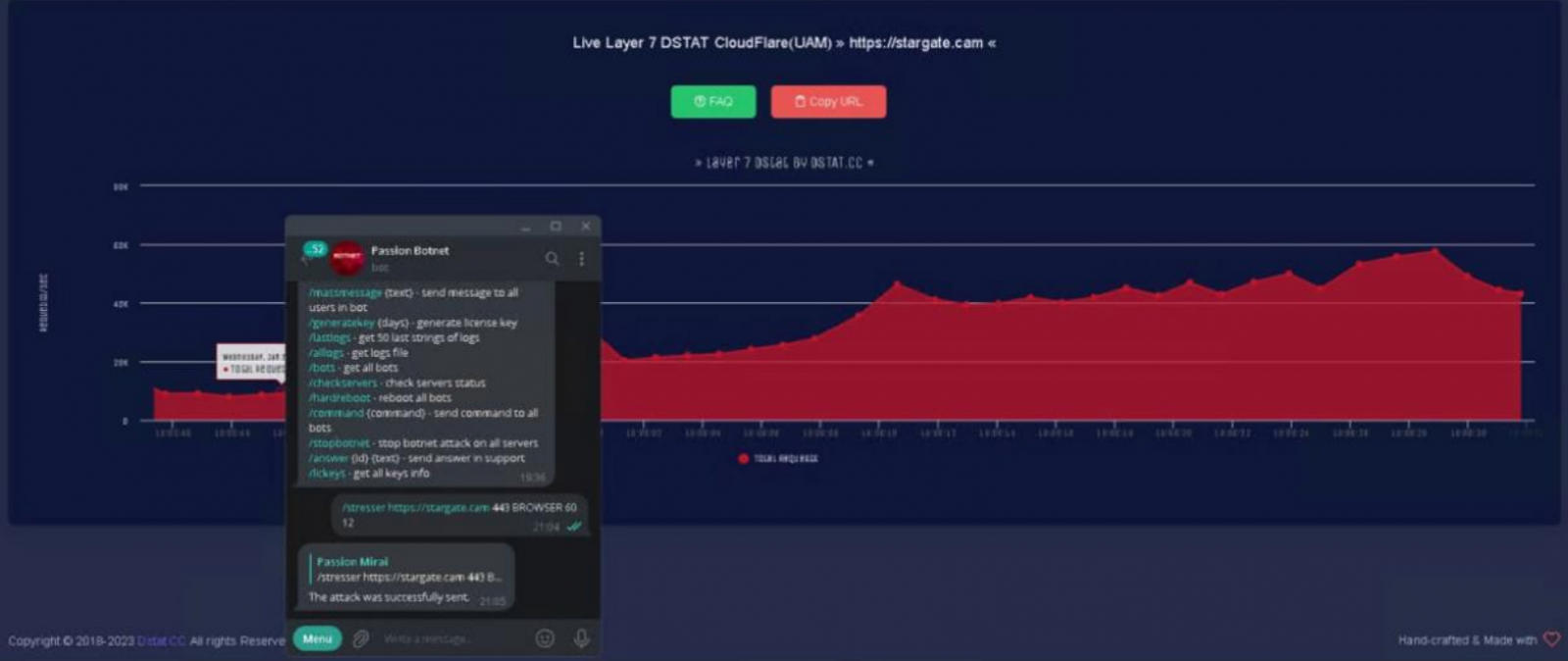
In October 2022, a pro-Russian DDoS crowdsourcing project named ‘DDOSIE‘ launched, paying the volunteers who took part in the attacks and awarding large sums to those with the most firepower.
The passion adds to an already thriving DDoS ecosystem, increasing the problem for organizations around the world who are the recipients of these attacks.
[ad_2]
Source link
