[ad_1]

A relatively new ransomware operation known as Nevada appears to be rapidly expanding its capabilities as security researchers have noticed improved locker functionality targeting Windows and VMware ESXi systems.
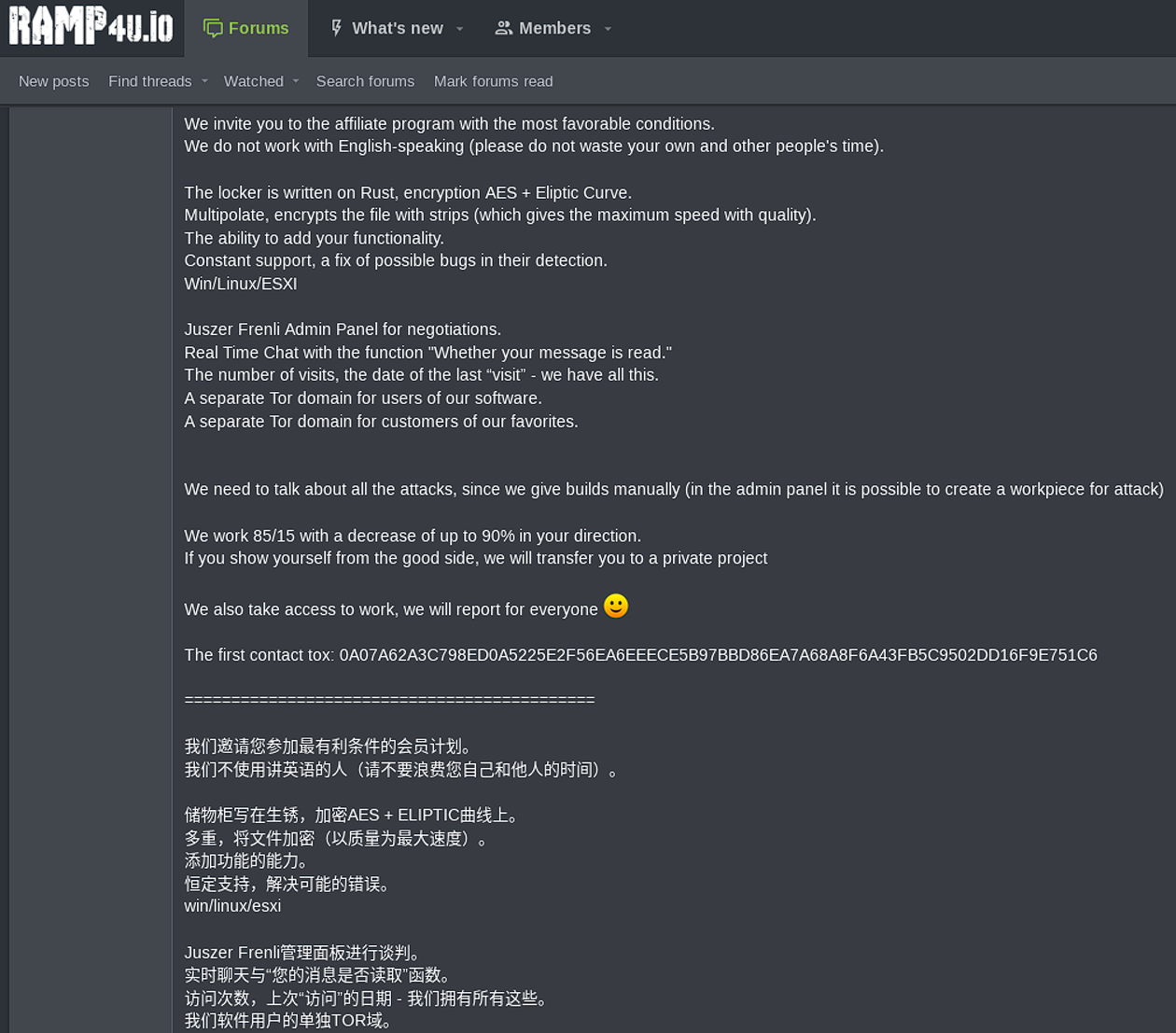
The Nevada ransomware started being promoted on darknet RAMP forums on December 10, 2022, inviting Russian and Chinese cybercriminals to join it for an 85% reduction in ransoms paid.
For high casualty affiliates, Nevada says they will increase their revenue share to 90%.
RAMP has been Previously reported as a space where Russian and Chinese hackers promote their cybercrime operations or communicate with their peers.
Nevada ransomware offers a Rust-based locker, a real-time trading chat portal, separate domains in the Tor network for affiliates and victims.
.png)
Resecurity researchers have analyzed the new malware and published a report on their findings. They say that while Nevada ransomware is explicit about excluding English-speaking affiliates, operators are open to doing business with approved access brokers from anywhere.
Targeting Windows hosts
The Nevada ransomware variant that focuses on Windows machines is executed through the console and supports a set of flags that give its operators some control over encryption:
- -file > encrypt selected file
- -dir > encrypt selected directory
- -sd > self-delete after all done
- -sc > delete shadow copies
- -lhd > load hidden drives
- -nd > search and encrypt network shares
- -sm > safe mode encryption
An interesting feature of Nevada ransomware is the set of system locales it spares from the encryption process. Typically, ransomware gangs exclude victims in Russia and CIS (Commonwealth of Independent States) countries. With this malware, the list extends to Albania, Hungary, Vietnam, Malaysia, Thailand, Turkey and Iran.
The payload uses MPR.dll to collect information about network resources, adding shared directories to the encryption queue. Each drive, including hidden drives, is assigned a drive letter and all files in them are also added to the queue.
After this step, the encryptor is installed as a service and then the hacked system reboots into Windows Safe Mode with an active network connection.
The locker uses the Salsa20 algorithm to perform intermittent encryption on files larger than 512 KB for faster encryption.
Executables, DLLs, LNKs, SCRs, URLs and INI files in Windows system folders and user program files are excluded from encryption to avoid making the victim host unbootable.
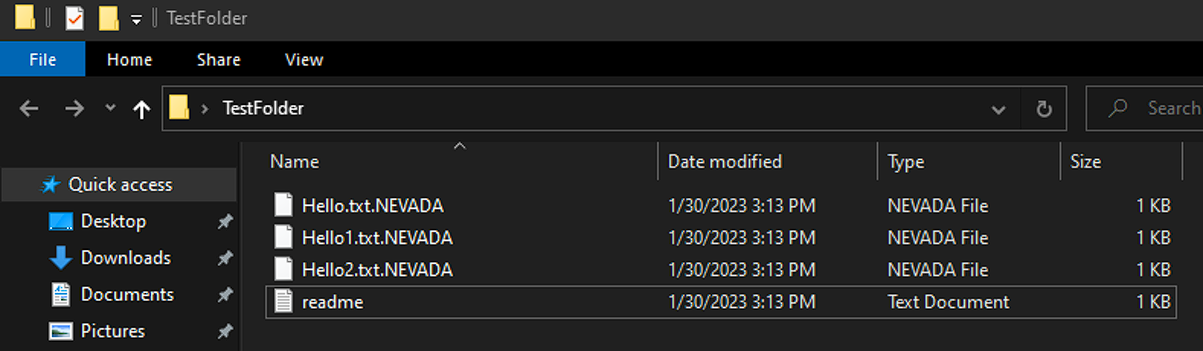
Encrypted files are appended with “.NEVADA” file extension and each folder hosts a ransom note that gives victims five days to respond to the threat actor’s demands otherwise their stolen data would be published on the site Nevada data leak web.
.png)
Targeting VMware ESXi Systems
The Linux/VMware ESXi version of Nevada ransomware uses the same encryption algorithm (Salsa20) as the Windows variant. It relies on a constant variable, an approach already seen in Petya ransomware.
The Linux cipher follows the same intermittent cipher system. fully encrypting only files smaller than 512 KB.
Likely due to a bug in the Linux version, Nevada ransomware will skip all files between 512 KB and 1.25 MB in size, the researcher found.
The Linux locker supports the following arguments:
- -help > help
- -daemon > create and start a ‘nevada’ service
- -file > encrypt a particular file
- -dir > encrypt a particular folder
- -esxi > disable all virtual machines
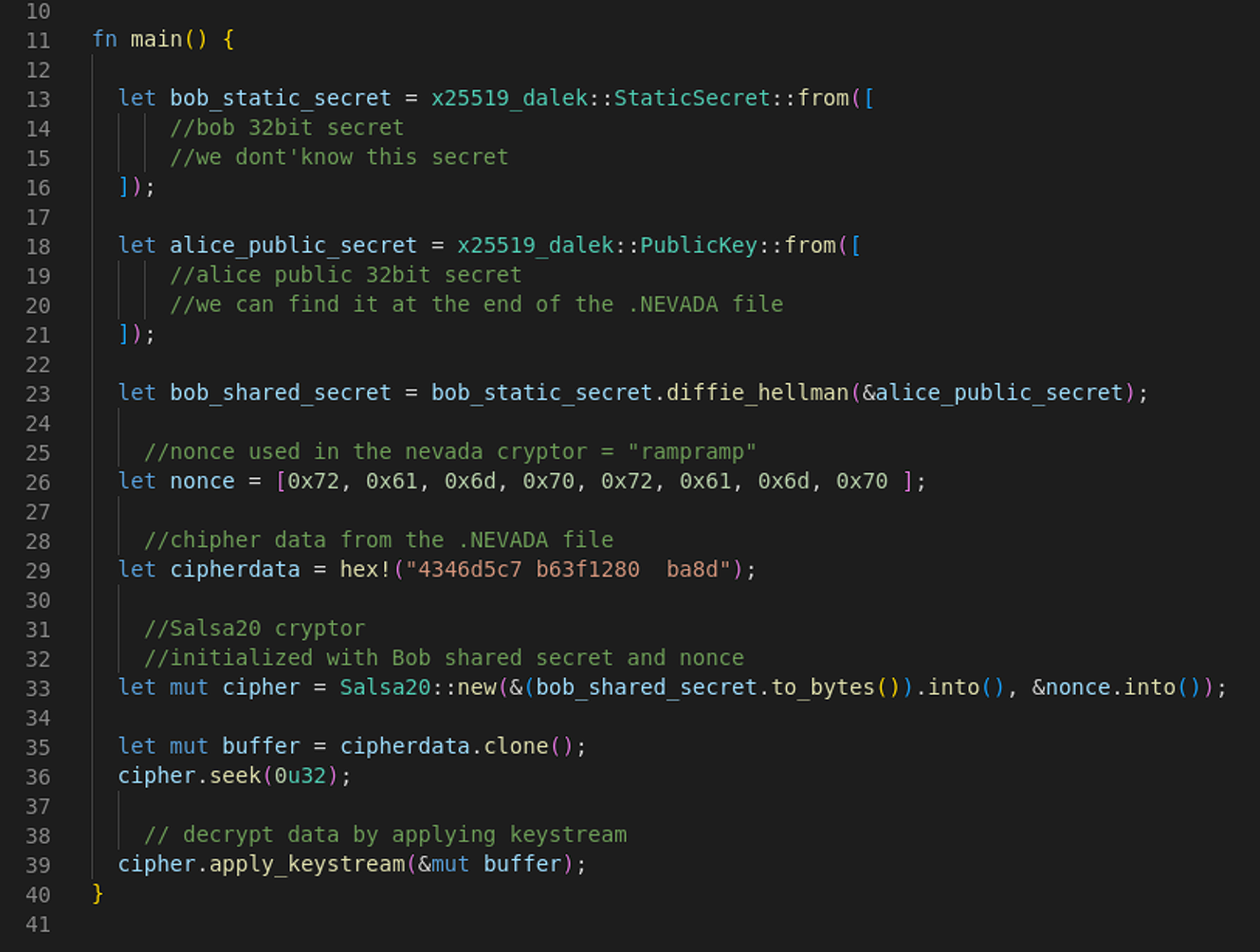
On Linux systems, the public key is stored at the end of the encrypted file as an extra 38 bytes.
Resecurity says the shared similarities with Petya ransomware extend to bugs in the encryption implementation that could also allow the private key to be retrieved, allowing data to be recovered without paying the ransom.
Nevada ransomware is still building its network of affiliates and initial access brokers, looking for skillful hackers.
Resecurity observed ransomware operators in Nevada buying access to compromised endpoints and hiring a dedicated post-exploitation team to perform the intrusion.
The researchers note that this threat appears to be continuing to grow and needs to be watched closely.
[ad_2]
Source link
