[ad_1]

THE Late 2022 LastPass Security Breach sent shockwaves through the security community. Password managers are generally considered the most secure and trusted platforms because they have to be. Holding credentials for many services, a breach in any client vault can have catastrophic consequences.
No service is perfect, and that goes for password managers, so what can you do to protect yourself even more?
Whether it’s choosing strong service passwords, diligently protecting secret keys, or ensuring the use of multi-factor authentication, there are steps your organization can take to minimize vulnerabilities.
What happened during the LastPass breach?
In December 2022, hackers stole LastPass save data. The breach included source code data and customer vaults containing unencrypted metadata such as URLs and encrypted data such as passwords. This violation affects at least 30 million users and 85,000 businessesaccording to data from a press release on LastPass usage.
This breach occurred when a hacker accessed a cloud-based storage environment containing source code and technical data. The threat actors exploited the stolen data against another LastPass employee which the threat actors used to gain additional access to storage volumes and decrypt the data.
Ultimately, this led to threat actors stealing a large amount of data, including encrypted client vaults.
What can your organization do?
Entrusting your sensitive data to a cloud service already requires significant research to find the ideal solution for your organization. An on-premises solution isn’t inherently more secure either.
It’s entirely possible for overwhelmed IT admins to accidentally configure a solution, lose a threat actor’s credentials, or forget to update an on-premises solution.
One advantage that cloud services have are dedicated teams for all of the above challenges.
Many IT departments need more resources to assign similar groups to an on-premises password management solution. Assuming your IT organization will use a cloud-based service, how can you best protect your data?
Ensure the use of zero-knowledge password management architectures
When you choose a cloud-based password management solution, the service should have no way of decrypting your data. Typically done through an encryption key that the customer owns and the online service does not, this “secret key” ensures that even if the data is lost, it will not be recoverable by a malicious actor.
This encryption is as good as the secret key used to encrypt the data, the quality of its protection and the level of encryption used on the cloud provider side.
What you can do, as a customer, is create a sufficiently complex randomly generated password that is not crackable within a reasonable amount of time.
Protecting the secret key is crucial to ensure that there is no way for a malicious actor to decrypt your organization’s data in the event of a breach.
Securing administrative accounts
Naturally, any service will require administrative access to configure the service online. The administrator account usually has access to all stored data.
Protecting this account against phishing or brute force password attempts with a strong password policy will prevent a malicious actor from gaining access to your company’s password vaults.
An administrative account should not include the use of a default username or breached passwords. NIST recommends checking passwords against a list of breached passwords.
Applying Multi-Factor Authentication
Combined with a strong password, applying proper multi-factor authentication will go a long way to thwarting any attempt to access your organization’s sensitive data. A good MFA setup should include the use of strong methods like a hardware key or a biometric method like a fingerprint.
Often, MFA is seen as an add-on, but a security-conscious organization enforces MFA policies for everyone. Even with a stolen password, MFA usually stops a bad actor because the time and effort needed to compromise MFA is not worth the gains.
Protecting access to resources with strong password policies
The protection of your company’s sensitive data relies on a strong password policy. A strong password policy is crucial for online decryption key, administrative accounts, and all device accounts that access online resources.
By ensuring that your organization has an appropriate password policy that does not reuse breached passwords, your business will be safe in the event of a breach.
Protect Resources with Specops Password Policy
Build the foundation of a strong password policy, Specops password policy features to keep your organization secure and compliant.
With in-depth password complexity rules and the Password Breach Protection add-on, your organization can ensure your users follow best practices for passwords.
Beyond password rules, Specops Password Policy integrates with your Active Directory domain to provide granular device targeting. Plus, your organization can show whether a changed password meets complexity requirements right from the user’s desktop.
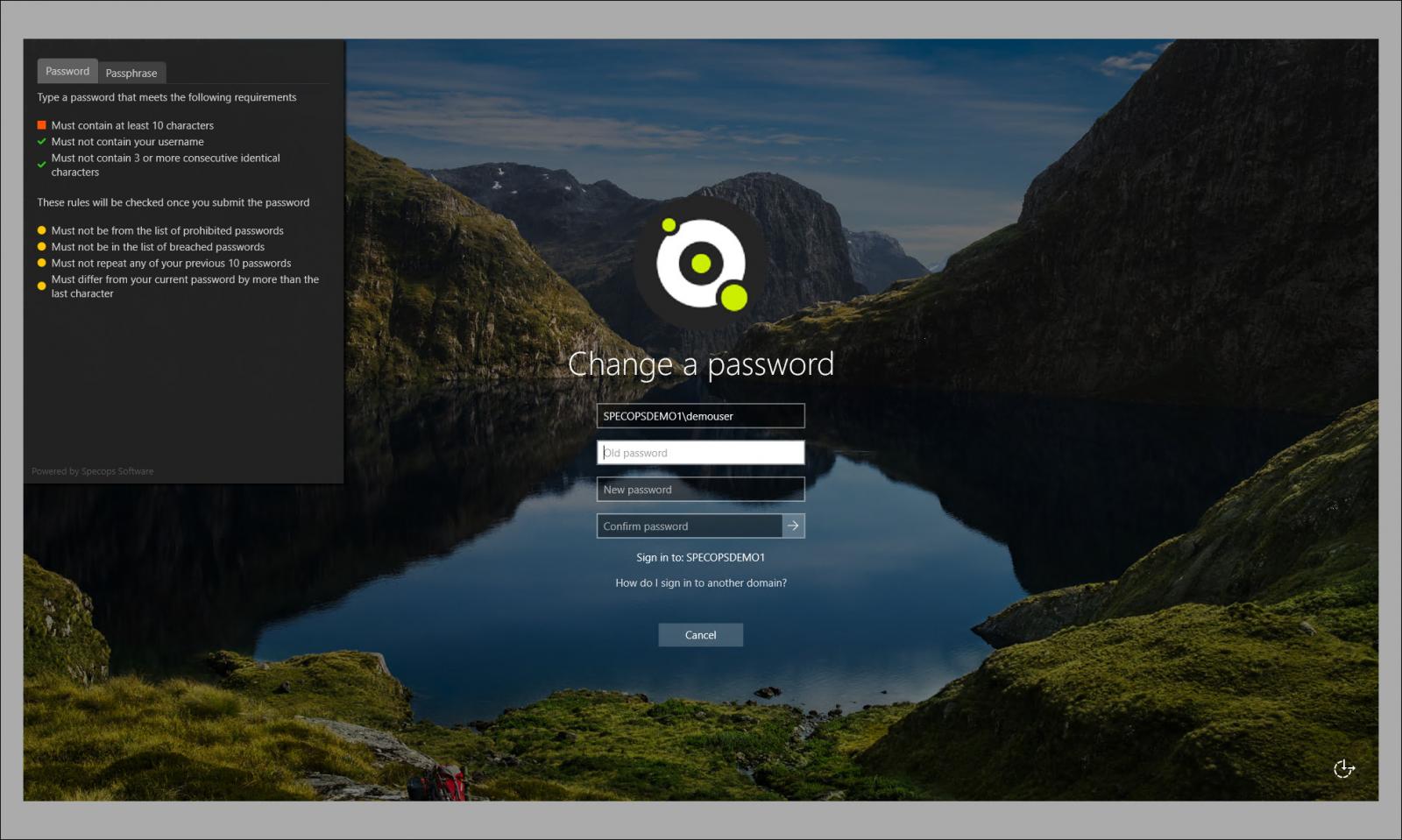
Mitigate the dangers of a hacked password manager
In the end, a hacked password manager is never good, but it doesn’t have to be disastrous. By using common sense account security practices, strong password policies, and enforced multi-factor authentication, you can help protect your organization from victimization.
It’s always best to assume that any service can be breached at any time. Implement appropriate security in the event of a breach and minimize risk to your business and customer data.
Sponsored and written by Specops software
[ad_2]
Source link
