[ad_1]

Security researchers see threat actors moving to a new open source command and control (C2) framework known as Havoc as an alternative to paid options such as Cobalt Strike and Brute Ratel.
Among his most interesting abilities, Ravaged is cross-platform and bypasses Microsoft Defender on up-to-date Windows 11 devices using sleep obfuscation, return address stack spoofing, and indirect system calls.
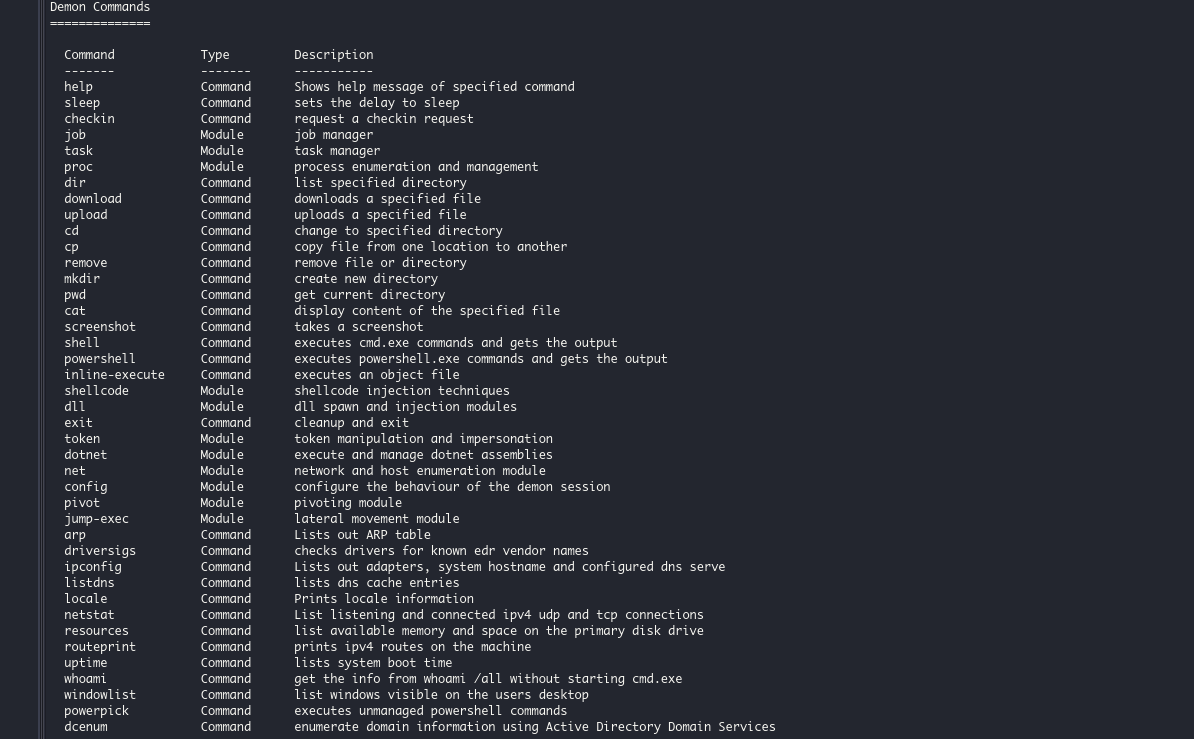
Like other exploit kits, Havoc includes a wide variety of modules that allow pen testers (and hackers) to perform various tasks on exploited devices, including running commands, managing processes, downloading additional payloads, Windows token manipulation, and shellcode execution.
This is all done through a web-based management console, allowing the “attacker” to see all of their compromised devices, events, and task results.
Havoc abused in attacks
An unknown threat group recently deployed this post-exploit kit in early January as part of an attack campaign targeting an undisclosed government organization.
Like the Zscaler ThreatLabz research team that spotted it in the wild observedthe abandoned shellcode loader on compromised systems will disable Event Tracing for Windows (ETW) and the final Havoc Demon payload is loaded without DOS and NT headers, both to evade detection.
The framework was also deployed through a legitimate malicious npm package typosquatting module (Aabquerys), like revealed in a report by the ReversingLabs research team earlier this month.
“Demon.bin is a malicious agent with typical RAT (Remote Access Trojan) functionality that was built using an open-source, post-exploitation, command-and-control framework named Havoc “said Lucija Valentić, threat researcher at ReversingLabs.
“It supports creating malicious agents in multiple formats, including Windows PE executable, PE DLL, and shellcode.”
More Cobalt Strike alternatives deployed in the wild
While Cobalt Strike has become the most common tool used by various threat actors to drop “beacons” onto their victims’ hacked networks for later relocation and delivery of additional malicious payloads, some of which have also recently started to seek alternatives as defenders have become better at detecting and stopping their attacks.
As BleepingComputer previously reported, Brute Ratel and Sliver are other options that help them evade antivirus and Endpoint Detection and Response (EDR) solutions.
Both of these C2 frameworks have already been field tested by a wide range of threat groups, from financially motivated cybercrime gangs to state-backed hacking groups.
Brute Ratel, a post-exploitation toolkit developed by Mandiant and CrowdStrike, former Red Team member Chetan Nayak, was used in attacks suspected of being linked to the Russian-sponsored APT29 (aka CozyBear) hacking group. At the same time, some Brute Ratel licenses likely landed in the hands of former Conti ransomware gang members.
In August 2022, Microsoft also noted that several threat actors, from state-sponsored groups to cybercriminal gangs (APT29, FIN12, Bumblebee/Coldtrain), now use Go-based Sliver C2 framework developed by researchers from cybersecurity firm BishopFox in their attacks as an alternative to Cobalt Strike.
[ad_2]
Source link
