[ad_1]

A new cross-platform malicious botnet named “MCCrash” infects Windows, Linux and IoT devices to carry out distributed denial of service attacks on Minecraft servers.
The botnet was discovered by Microsoft’s Threat Intelligence team, which reports that once it infects a device, it can spread to other systems on the network by brute-forcing SSH credentials.
“Our analysis of the DDoS botnet revealed features specifically designed to target private Minecraft Java servers using specially crafted packages, most likely as a service sold on forums or darknet sites,” Microsoft’s new report explains.
Currently, most MCCrash-infected devices are in Russia, but there are also victims in Mexico, Italy, India, Kazakhstan, and Singapore.
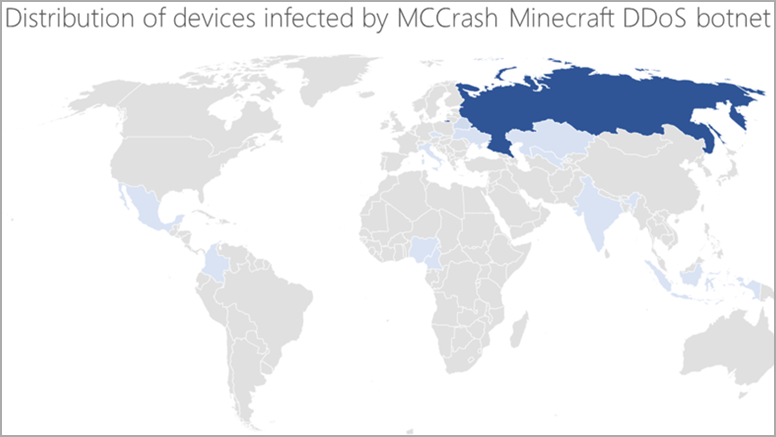
Minecraft servers are often the target of DDoS attacks, whether for pain players on the server or as part of an extortion request.
In October 2022, Cloudflare reported mitigating a record 2.5 Tbbs DDoS attack targeting Wynncraft, one of the largest Minecraft servers in the world.
Starts with pirated software
Microsoft claims that devices are initially infected with MCCrash after users installed fake Windows Product Activation Tools and Microsoft Office License Activators (KMS Tools) containing Trojans.
The hacking tools contain malicious PowerShell code that downloads a file named “svchosts.exe”, which launches “malicious.py”, the main payload of the botnet.
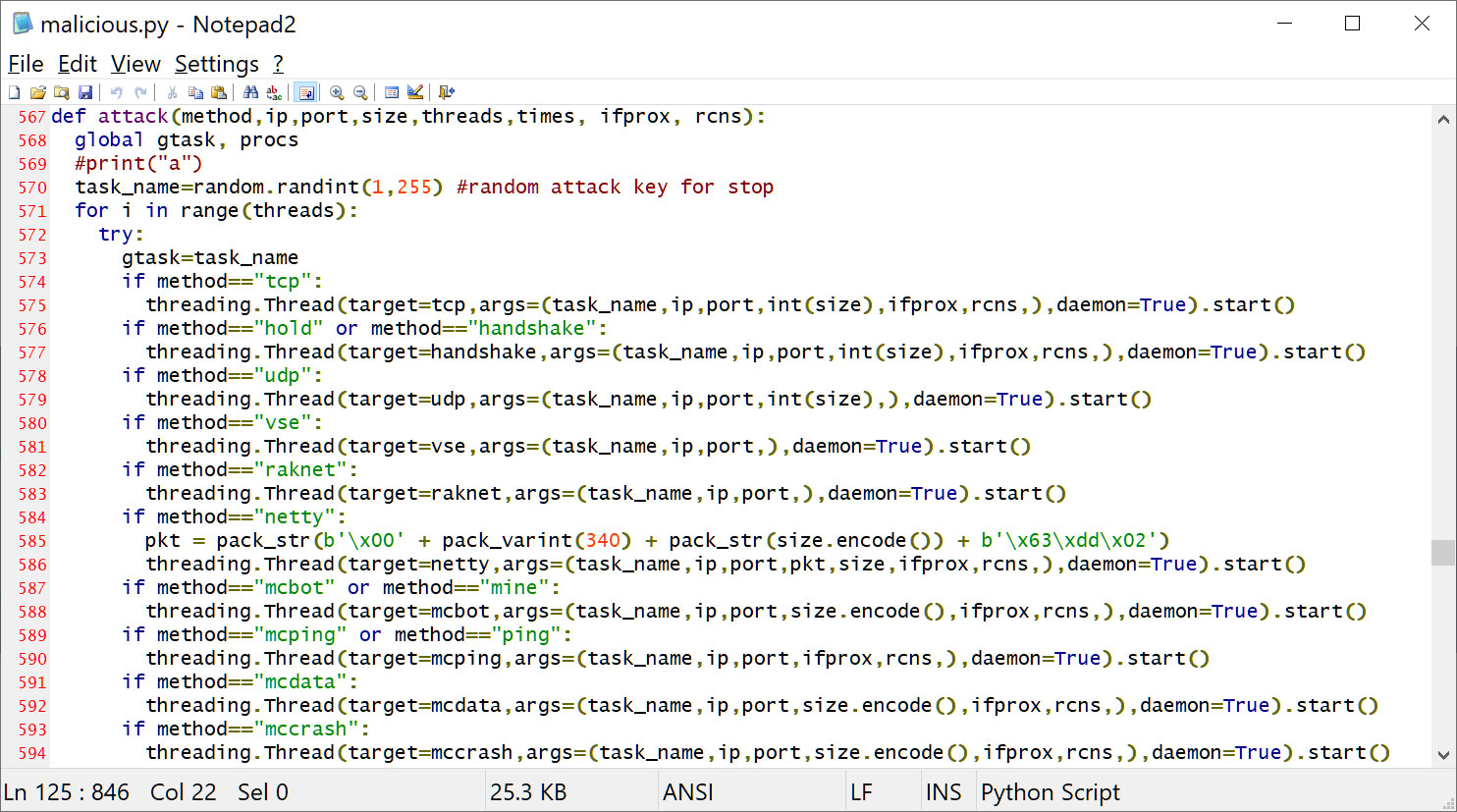
Source: BleepingComputer
MCCrash then attempts to spread to other devices on the network by performing brute force SSH attacks on IoT and Linux devices.
“The botnet spreads by enumerating default credentials on Secure Shell (SSH) enabled devices exposed to the internet.
Since IoT devices are typically enabled for remote configuration with potentially insecure settings, these devices could be vulnerable to attacks like this botnet.
The botnet’s propagation mechanism makes it a unique threat because even though the malware can be removed from the infected source PC, it can persist on unmanaged IoT devices in the network and continue to function as part of the botnet.” – Microsoft .
The malicious Python file can run on both Windows and Linux environments. When first launched, it establishes a TCP communication channel with the C2 on port 4676 and sends basic information about the host, such as the system it is running on.
On Windows, MCCrash establishes persistence by adding a registry value to the “Software\Microsoft\Windows\CurrentVersion\Run” key, with the executable as the value.
.png)
Attack Minecraft Servers
The botnet receives encrypted commands from the C2 server based on the type of operating system identified in the initial communication.
The C2 will then send one of the following commands back to the infected MCCrash device to execute:
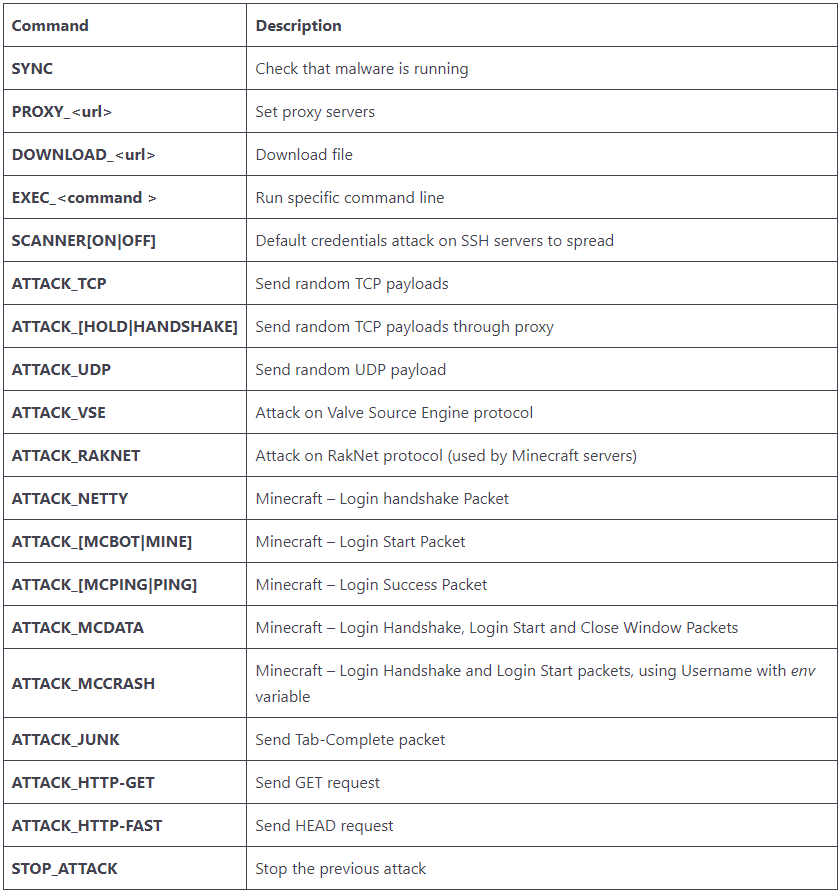
Most of the above commands specialize in DDoS attacks on Minecraft servers, with “ATTACK_MCCRASH” being the most notable due to using a new method to crash the target server.
According to Microsoft, hackers created the botnet to target Minecraft server version 1.12.2, but all server versions from 1.7.2 to 1.18.2 are also vulnerable to attacks.
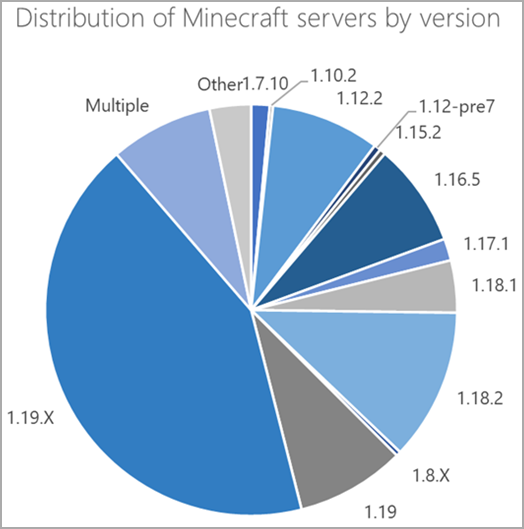
Version 1.19, released in 2022, is unaffected by the current implementation of ATTACK_MCCRASH, ATTACK_[MCBOT|MINE]and ATTACK_MCDATA commands.
Still, a considerable number of Minecraft servers are running on older versions, most located in the United States, Germany, and France.
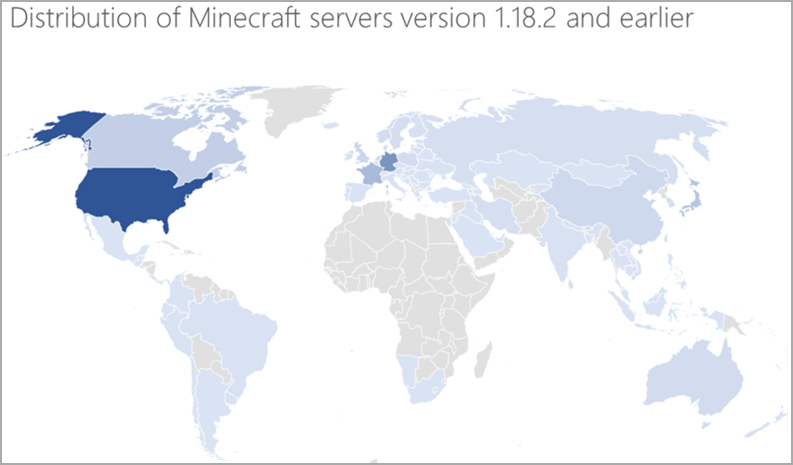
“This threat’s unique ability to use IoT devices that often go unmonitored as part of the botnet greatly increases its impact and reduces its chances of being detected,” Microsoft comments.
To protect your IoT devices from botnets, keep their firmware up-to-date, change default credentials to a strong (long) password, and disable SSH logins if not needed.
[ad_2]
Source link
