[ad_1]

Kinsing malware now actively breaches Kubernetes clusters by exploiting known weaknesses in container images and misconfigured and exposed PostgreSQL containers.
While these tactics aren’t new, Microsoft’s Defender for Cloud team reports that they’ve seen an increase lately, indicating that threat actors are actively looking for specific entry points.
Kinsing is Linux malware with a history of targeting containerized environments for crypto mining, using hacked server hardware resources to generate revenue for threat actors.
Threat actors behind Kinsing are known to exploit known vulnerabilities like Log4Shelland, more recently, a Atlassian Confluence CRE to exceed goals and establish persistence.
Finding Container Image Defects
Microsoft says it has seen an increase in two methods used by Kinsing operators to gain initial access to a Linux server – exploiting a vulnerability in container images or misconfigured PostgreSQL database servers.
When exploiting image vulnerabilities, threat actors look for remote code execution flaws that allow them to push their payloads.
Microsoft Defender for Cloud telemetry indicated that threat actors are attempting to exploit vulnerabilities in the following applications for initial access:
- PHPUnit
- life ray
- Oracle WebLogic
- WordPress
In the WebLogic cases, hackers are looking for CVE-2020-14882, CVE-2020-14750, and CVE-2020-14883, all remote code execution flaws affecting the Oracle product.
“Recently, we identified a widespread campaign by Kinsing that targeted vulnerable versions of WebLogic servers,” it reads. a report by Microsoft security researcher Sunders Bruskin.
“Attacks begin by scanning a wide range of IP addresses, looking for an open port that matches WebLogic’s default port (7001).”
Mitigating this issue is as simple as using the latest available versions of the images you want to deploy and only sourcing those images from official repositories and trustworthy locations.
Microsoft also suggests minimizing access to exposed containers by using IP allow lists and following the principles of least privilege.
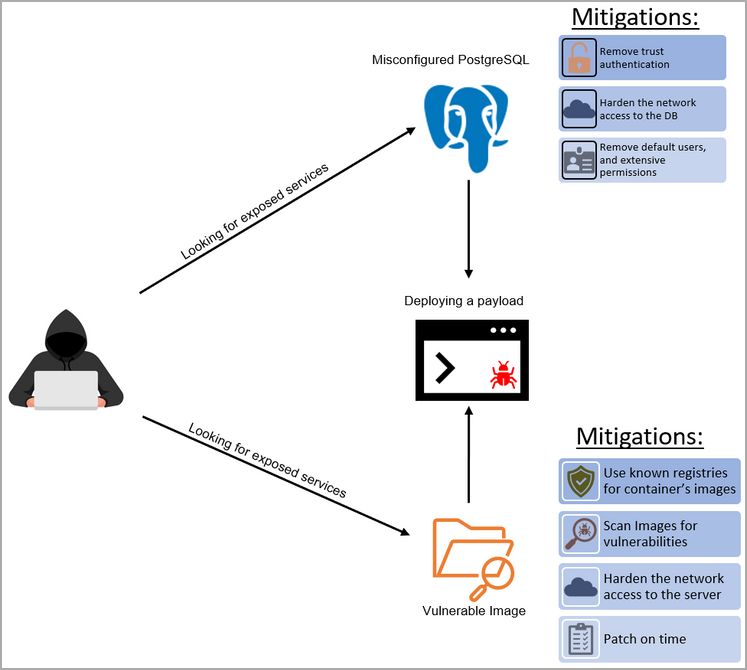
Attacking PostgreSQL
The second initial attack path observed by Microsoft security experts was an increase in targeting of misconfigured PostgreSQL servers.
One of the most common misconfigurations exploited by attackers is the “trusted authentication” setting, which instructs PostgreSQL to assume that “anyone who can connect to the server has permission to access the database.”
Another mistake is assigning a range of IP addresses that is way too wide, including any IP addresses the attacker can use to give them access to the server.
Even though IP access configuration is strict, Microsoft says Kubernetes is still prone to Address Resolution Protocol (ARP) poisoning, so attackers could spoof cluster applications to gain access.
To mitigate PostgreSQL configuration issues, see the project security recommendations web page and implement the proposed measures.
Finally, Microsoft says Defender for Cloud can detect permissive settings and misconfigurations on PostgreSQL containers and help administrators mitigate risks before hackers exploit them.
For PostgreSQL administrators whose servers are infected with Kinsing, Sreeram Venkitesh of BigBinary wrote an article about how the malware infected their device and how they ultimately deleted it.
[ad_2]
Source link
