[ad_1]

GitHub has introduced a new option to configure code analysis for a repository called “default configuration”, designed to help developers configure it automatically with just a few clicks.
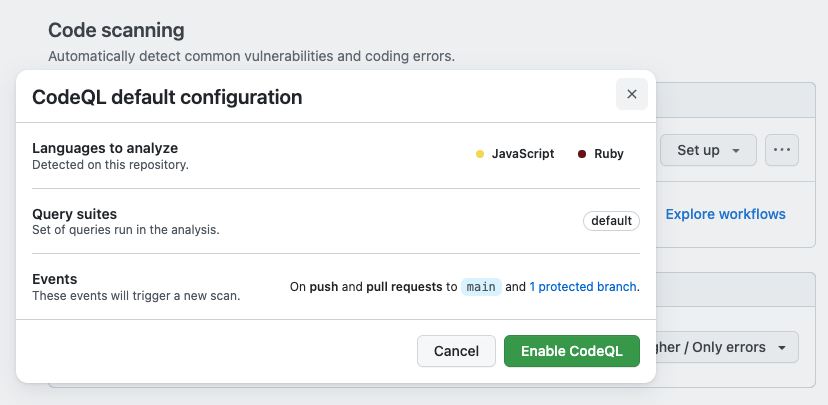
While the CodeQL code analysis engine, which powers GitHub’s code analysis, supports many languages and compilersthe new option only shows for Python, JavaScript, and Ruby repositories.
Product Marketing Manager Walker Chabbott said GitHub is working to expand support for more languages over the next six months.
To use the new Code Analysis configuration option, you need to go to “Code Security and Analysis” in your repository settings, click on the “Configure” drop-down menu and choose the Default option.
“When you click ‘Default’ you will automatically see a custom configuration summary based on the contents of the repository”, Chabbott said.
“This includes the languages detected in the repository, the query packs that will be used, and the events that will trigger scans. Going forward, these options will be customizable.”
After clicking “Enable CodeQL”, Code Analysis will immediately begin scanning the repository for vulnerabilities to help you fix any flaws it finds and build more secure software.
The CodeQL code analysis engine was added to the capabilities of the GitHub platform after the acquisition of the Semmle code analysis platform in September 2019.
The first beta version of scanning code to Satellite GitHub in May 2020, and its General Availability was announced four months later, in September 2020.
During beta testing, the feature was used to scan over 12,000 repositories 1.4 million times to find over 20,000 security issues, including remote code execution (RCE) flaws, SQL and cross-site scripting (XSS) injection.
Code analysis is free for all public repositories and is also available as a GitHub advanced security feature for private GitHub Enterprise repositories.
Last month, GitHub also rolled out support for the free analysis of exposed secrets (such as authentication tokens and credentials) to all public repositories.
[ad_2]
Source link
