[ad_1]

Intel is investigating the leak of alleged private keys used by the Intel Boot Guard security feature, which may impact its ability to block the installation of malicious UEFI firmware on MSI devices.
In March, the Money Message extortion gang attacked MSI’s computer hardware, claiming to have stolen 1.5TB of data in the attack, including firmware, source code and databases.
As first reported by BleepingComputerthe ransomware gang demanded a $4,000,000 ransom and, after not being paid, began leaking MSI’s data on its data leak site.
Last week, threat actors began leaking stolen MSI data, including source code for firmware used by the company’s motherboards.
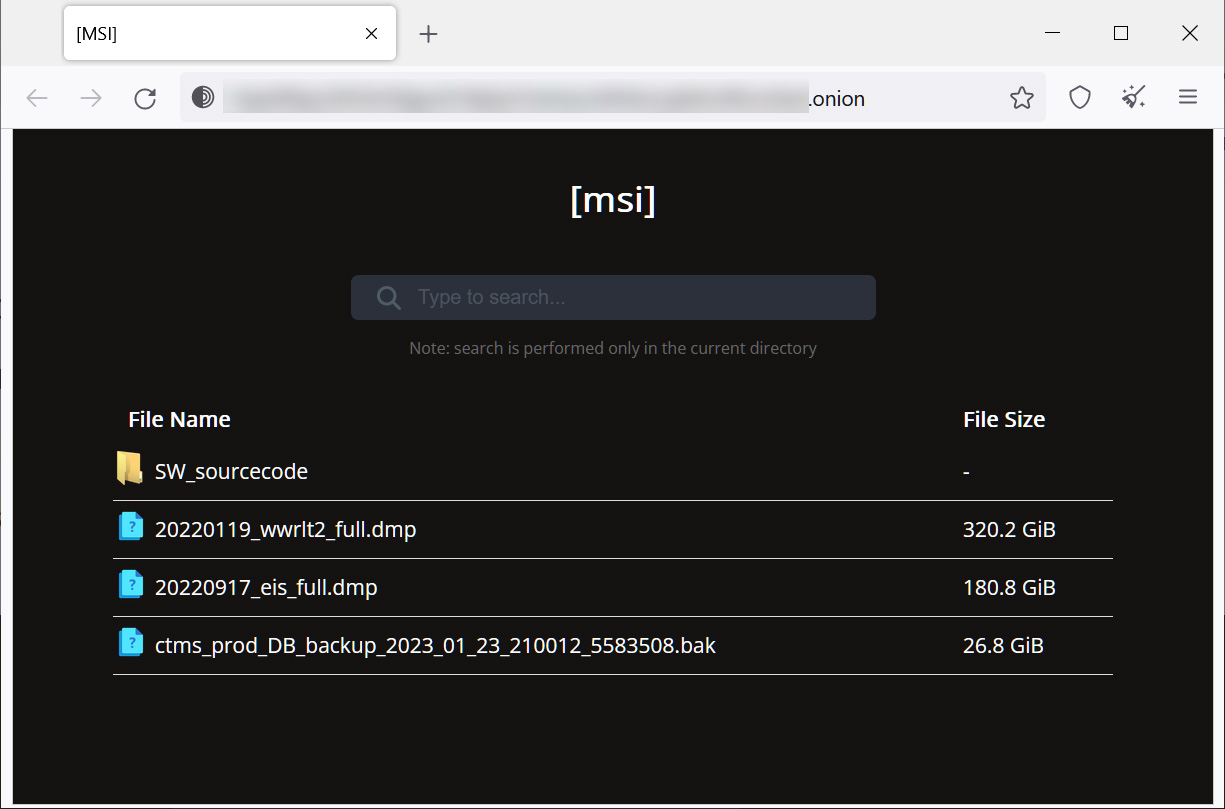
Source: BleepingComputer
Intel Boot Guard impacted by an attack
On Friday, Alex Matrosov, CEO of firmware supply chain security platform Binarly, warned that the leaked source code contains image signing private keys for 57 MSI products and Intel Boot Guard private keys for 116 MSI products.
“Intel is aware of these reports and is actively investigating. Researchers have claimed private signing keys are included in the data, including OEM MSI signing keys for Intel® Boot Guard,” Intel told BleepingComputer in response. to our questions about the leak.
“It should be noted that Intel Boot Guard OEM keys are generated by the system manufacturer and are not Intel signing keys.”
Matrosov said this leak may have prevented Intel Boot Guard from being effective on MSI devices using “11th Tiger Lake, 12th Adler Lake, and 13th Raptor Lake” processors.
“We have evidence that the entire Intel ecosystem is affected by this MSI data breach. It’s a direct threat to MSI customers and unfortunately not just them,” Matrosov told BleepingComputer on Friday afternoon. .
“Signing keys for the fw image allow an attacker to create malicious firmware updates and can be delivered through a normal bios update process with MSI update tools.”
“The Intel Boot Guard key leak impacts the entire ecosystem (not just MSI) and renders this security feature useless.”
Intel Boot Guard is a security feature built into modern Intel hardware designed to prevent the loading of malicious firmware, known as UEFI boot kits. This is an essential feature used to meet Windows UEFI Secure Boot requirements.
This is because malicious firmware loads before the operating system, allowing it to hide its activities from the kernel and security software, to persist even after an operating system is reinstalled, and to help install malware on compromised devices.
To protect against malicious firmware, Intel Boot Guard will check if a firmware image is signed with a legitimate private signing key using an embedded public key built into Intel hardware.
If the firmware can be verified as legitimately signed, Intel Boot Guard will allow it to be loaded onto the device. However, if the signing fails, the firmware will not be allowed to load.
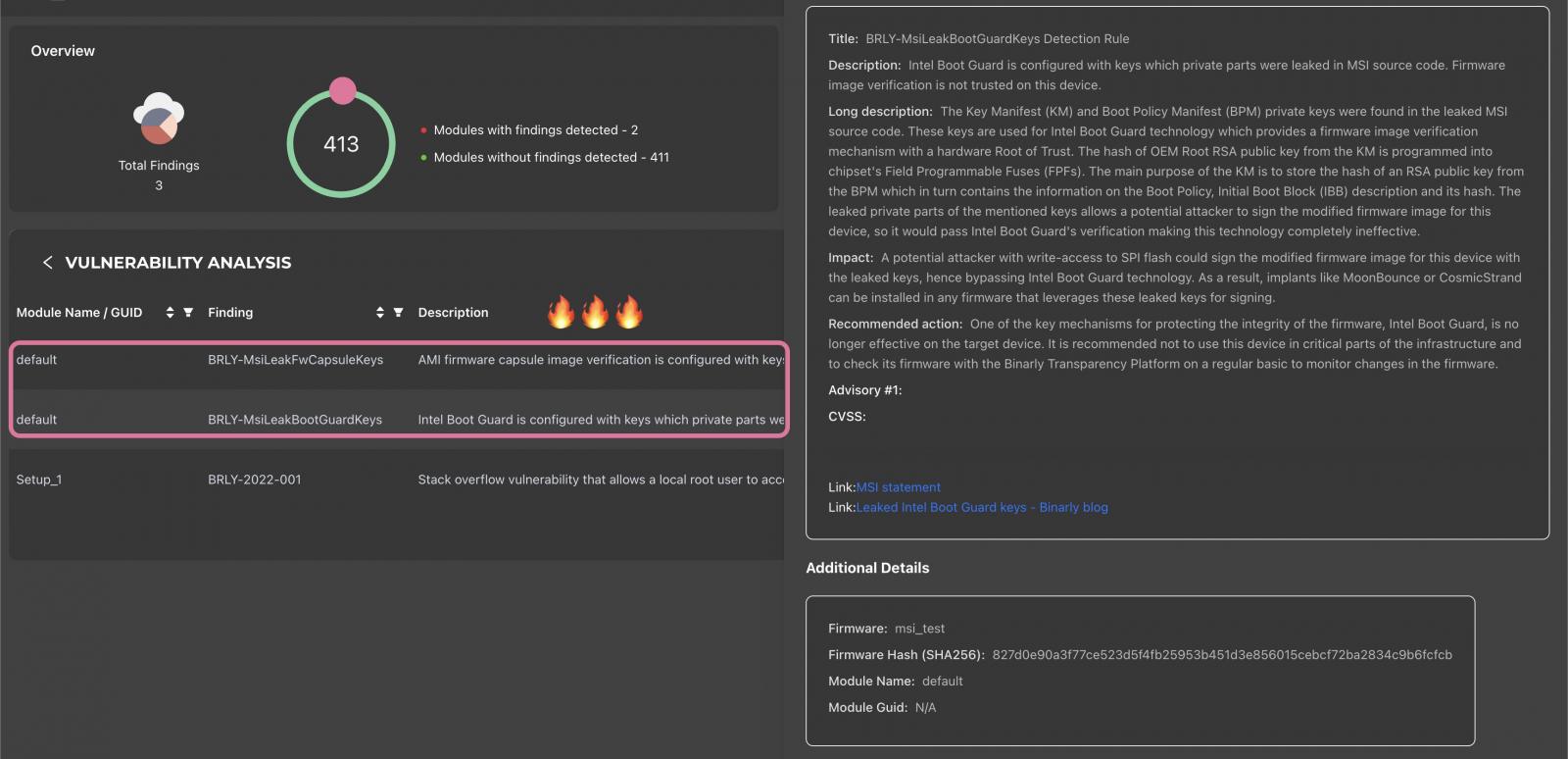
Source: Binary
The biggest problem with this leak is that the public keys used to verify signed firmware using the leaked keys are supposed to be built into Intel hardware. If they cannot be changed, the security function is no longer reliable on devices using these leaked keys.
“The Manifest (KM) and Boot Policy Manifest (BPM) private keys were found in leaked MSI source code. These keys are used for Boot Guard technology which provides firmware image verification with hardware root of trust “, warns Binarly in a notice. shared on Twitter.
“The OEM Root RSA hash public key of the KM manager is programmed into the FPF (Field Programmable) of the chipset. The main purpose of the KM is to store the hash of an RSA public key of the BPM which in turn contains the information on the Boot Policy, description of the initial boot block (IBB) and its hash.”
“The leaked private portions of the mentioned keys allow a potential attacker to sign the modified firmware for this device so that it would pass Intel Boot Guard verification, rendering this technology completely ineffective.”
While these keys are unlikely to be useful to most threat actors, some skilled attackers have used malicious firmware in attacks, such as CosmicStrand And Black Lotus UEFI Malware.
“Now functionality can be compromised and attackers can create malicious firmware updates on affected devices without worrying about Intel Boot Guard,” Matrosov said in a final warning shared with BleepingComputer.
binary a published a list of impacted MSI hardwareincluding 116 MSI devices that were allegedly compromised by leaked Intel Boot Guard keys.
BleepingComputer also contacted MSI and Intel with further questions, but no response was immediately available.
Update 08/05/23: Added statement from Intel
[ad_2]
Source link
