[ad_1]

Data theft involves stealing data stored in corporate databases, terminals and servers. Stolen data may include identifying information, credit card numbers, personally identifiable information, medical records, software code and proprietary technologies. Data theft occurs both inside and outside an organization.
Malicious actors can steal data from organizations or individuals to resell to other malicious actors. Data theft is a major risk for many organizations, as it can lead to identity theft, reputational damage and financial loss.
Common causes of data theft
Threat actors steal data from organizations using various techniques. Common causes of data theft are:
- Software vulnerabilities and misconfigurations: Poorly written or outdated software can have vulnerabilities that malicious actors can exploit to steal data. A misconfiguration occurs when security settings are not set correctly during the configuration process.
Misconfigurations can include default passwords, usernames, and insecure protocols, ports, and services. Malicious actors can steal sensitive information from an organization’s servers that are not properly configured.
- Malware Downloads: An employee of an organization can accidentally download malware onto their device by visiting a compromised website. This malware can allow a malicious actor to steal data from the infected device.
- Internal threat: Employees can pose a serious threat to an organization since they have authorized access to sensitive organizational data. A disgruntled employee can steal or sell this data for profit. Insider threats can come from current or former employees, contractors, and partners who have access to an organization’s sensitive data.
Consequences of data theft for organizations
Organizations that are Data theft victims may suffer the following consequences:
- Loss of customers: An organization’s customers may suffer financial loss or be exposed to sensitive data due to data theft. This usually discourages customers or users from continuing to do business with the affected organization.
- Customer lawsuits: Customers whose data has been mishandled by an organization can take legal action against those organizations.
- High recovery costs: Organizations spend a lot of money fixing systems and recovering data after they have been victims of data theft.
- Regulatory fines: Depending on the industry, an organization can face hefty fines from regulators for non-compliance with their security mandates.
- Disruption of business operations: An organization can suffer a disruption of its business operations following the theft of data on its critical systems.
How Wazuh Detects Data Theft
Wazuh is a free and open source enterprise-ready security solution that provides unified SIEM and XDR protection across multiple workloads.
It provides a centralized view for threat detection and security monitoring in virtualized, on-premises, cloud-based, and containerized environments.
Wazuh offers several abilities organizations can implement to prevent, detect and respond to security threats. The sections below highlight several Wazuh features that provide protection against data theft.
File integrity monitoring
The File Integrity Monitoring (FIM) module monitors files and directories on an endpoint. It triggers an alert when a file is created, modified or deleted.
The Wazuh FIM The module stores the cryptographic checksum and other attributes of Windows registry files and keys to detect any changes in these values. Monitoring of Windows files, directories and registries is performed periodically or in near real time.
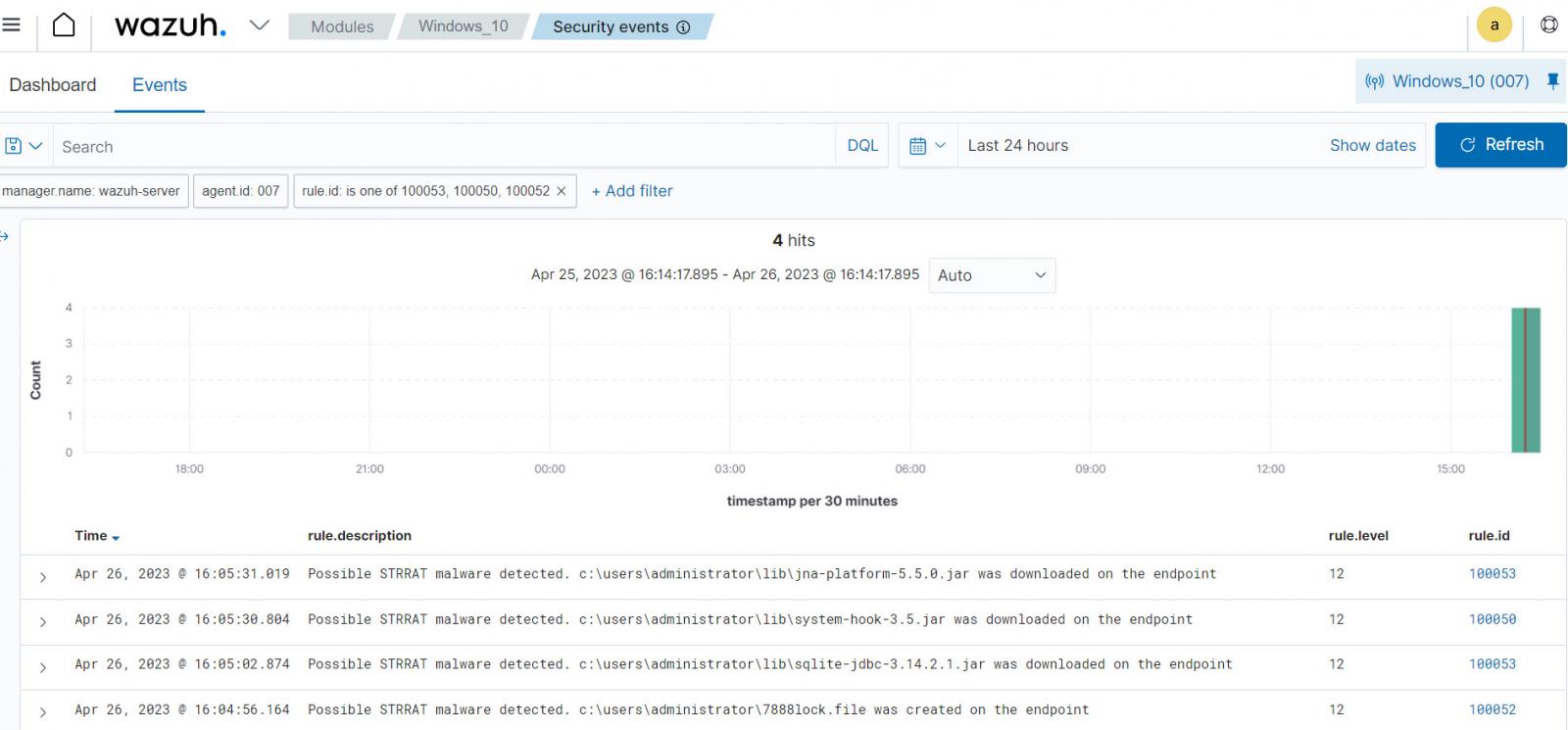
Malicious actors use malware to steal data from endpoints. This malware creates or uploads malicious files to infected endpoints. The Wazuh FIM module detects when these files are created or downloaded on infected endpoints.
For example, in this blog post, the Wazuh FIM module detects files created and downloaded by the STRRAT malware. Figure 3 below shows the detection of STRRAT malware with the Wazuh FIM module.
Vulnerability detection
Vulnerability scanning is the process of identifying security weaknesses in the operating system and applications installed on monitored endpoints. Wazuh uses the Vulnerability detector module to detect vulnerabilities on monitored endpoints.
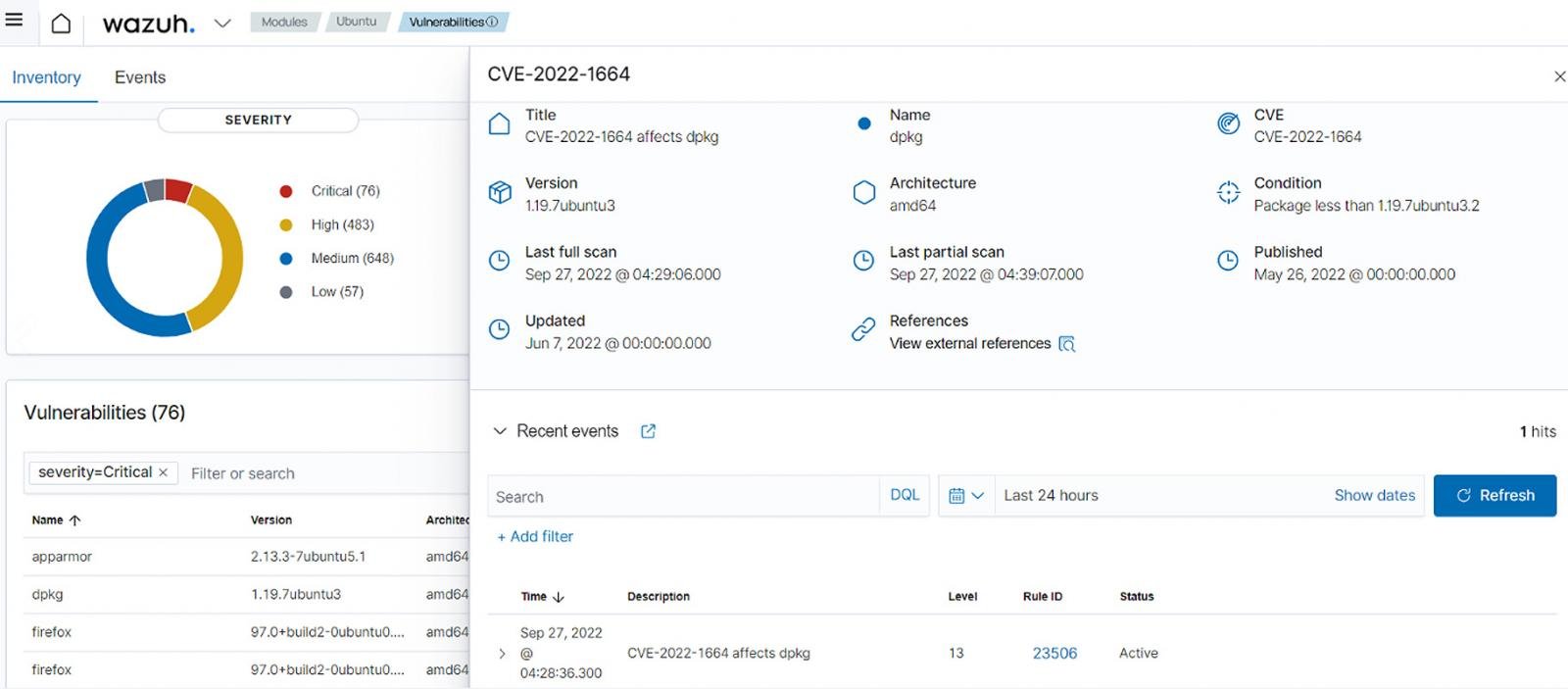
Wazuh creates a global vulnerability database from publicly available Common Vulnerabilities and Exposures (CVE) repositories. Wazuh then uses this database to cross-correlate application inventory data collected from monitored endpoints to detect vulnerable software.
The Wazuh Vulnerability Detector module can discover unpatched vulnerabilities on endpoints that malicious actors can exploit to steal data.
Security Configuration Assessment (SCA)
Security configuration assessment is the process of scanning monitored endpoints to discover misconfigurations that can expose those endpoints to cyberattacks.
SCA continuously improves system configuration posture by adopting standards such as the Center of Internet Security (CIS), NIST, PCI-DSS, HIPAA, and many others.
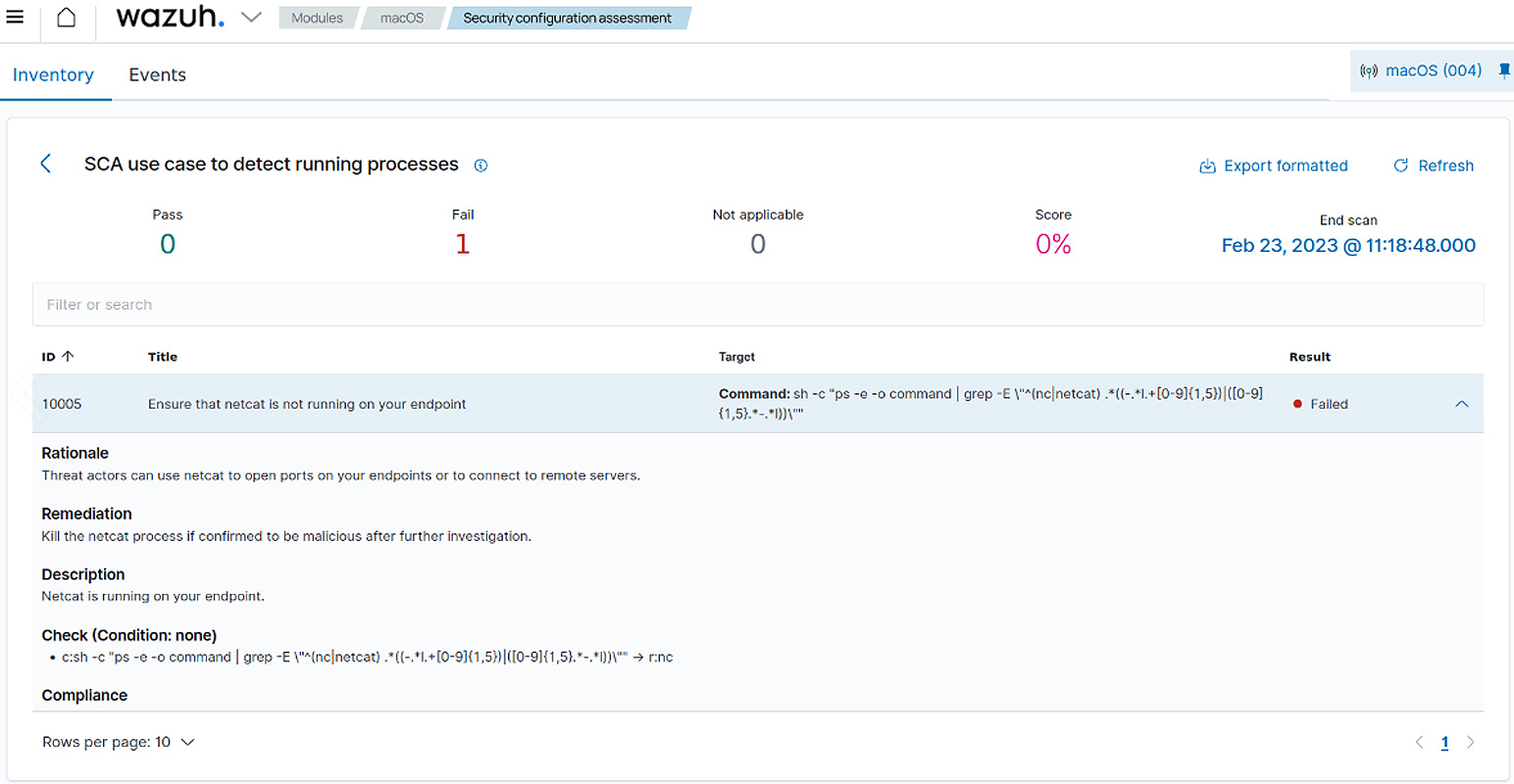
Wazuh SCA The module performs regular scans on monitored endpoints to uncover sensitive data exposures or misconfigurations. These scans evaluate the configuration of the device or applications on the device using policy files containing rules to test against the actual configuration of the device.
Wazuh SCA can discover unnecessary services, default credentials, insecure protocols, and ports on monitored endpoints that malicious actors can exploit to steal data.
Log data analysis
Log data analysis is the process of examining logs generated from devices to detect cyber threats and identify bugs and security risks.
Wazuh collects security logs generated from multiple endpoints and uses decoders and rules to analyze them.
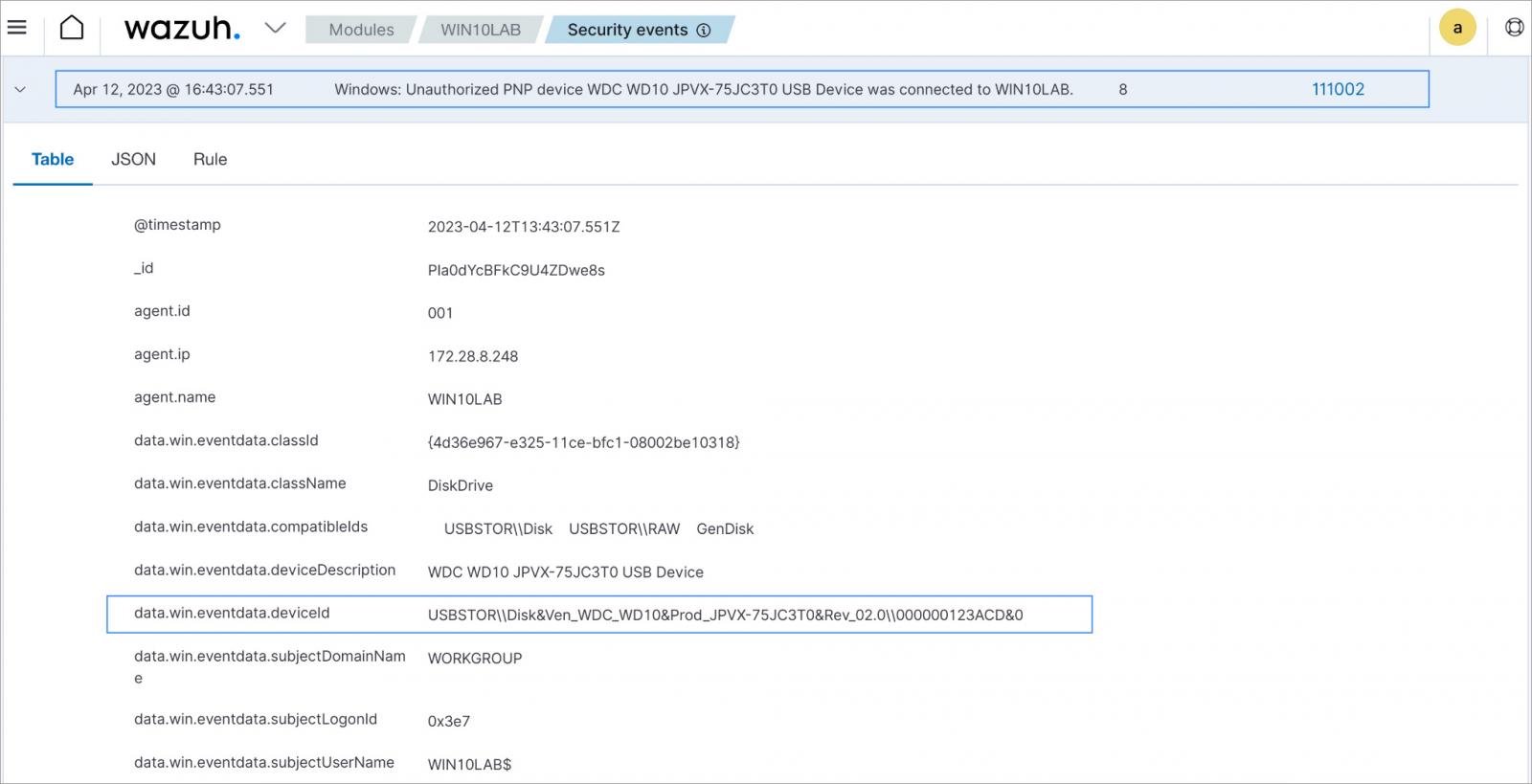
Disgruntled employees or malicious actors can use USB drives to steal sensitive data from an organization’s endpoint. Wazuh collects and analyzes event logs generated when a USB drive is inserted into a terminal.
In this blog postWazuh detects unauthorized and authorized USB drives using a list of authorized USB drives in a constant database (CDB).
Conclusion
Organizations are at risk of data theft if they do not implement effective security controls. The impact of data theft can be very devastating for organizations. Therefore, organizations can take advantage of various features of Wazuh to effectively detect data theft.
Wazuh is a free and open source XDR solution with multiple modules for detecting and responding to cyber threats.
Wazuh seamlessly integrates with third-party solutions and technologies. Wazuh also has steady growth community where users are supported. To learn more about Wazuh, please see our Documentation And blog posts.
Sponsored and written by Wazuh
[ad_2]
Source link
