[ad_1]
A team of researchers from Georgia Tech, the University of Michigan and Ruhr University in Bochum have developed a new attack called “Hot Pixels”, which can harvest pixels from content displayed in the target’s browser and infer browsing history.
The attack exploits the data-dependent computation times on modern system-on-chips (SoCs) and graphics processing units (GPUs) and applies them to stealthily extract information from web pages visited on Chrome and Safari, even if with the last side – channel countermeasures enabled.
Researchers have found that modern processors struggle to balance power consumption requirements and heat dissipation limitations with high execution speeds. This leads to distinct behavior patterns that point to specific instructions and operations.
These patterns are easily detectable through measurements from internal sensors that are often accessed through software and, depending on the type of device, can help discern what is being viewed on the target device with up to 94% accuracy.
Mapping CPU behavior on modern devices
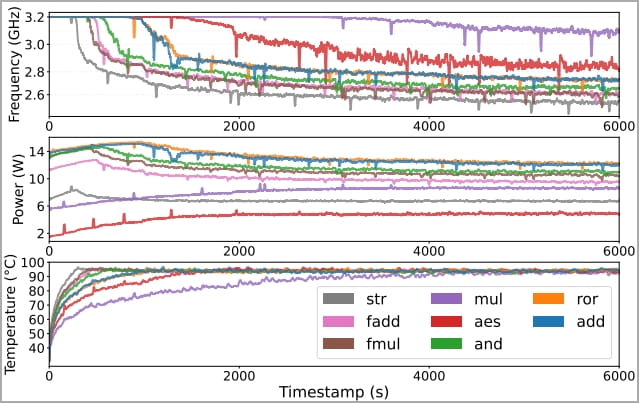
By analyzing frequency, power, and temperature measurements on modern devices, the researchers concluded that passively cooled processors could leak information via power and frequency, while actively cooled chips leaked data via temperature readings. temperature and power.
Researchers experimented with Apple M1 chips, Cortex-X1 Arm cores inside a Google Pixel 6 Pro device, and Qualcomm Snapdragon 8 Gen 1 on OnePlus 10 Pro. They mapped choke points (thermal limits) and correlated workloads with separate frequency and power consumption metrics.
Next, the team experimented with data-dependent leak channels on discrete and integrated GPUs, including Apple’s M1 and M2, AMD Radeon RX 6600, Nvidia GeForce RTX 3060, and Intel Iris Xe.
Researchers performed a detailed investigation and characterization of how different processing behaviors (such as bit-flip operations) might impact observable factors such as power consumption, temperature, and frequency and used this data as a basis for evaluating the “Hot Pixels” attack.
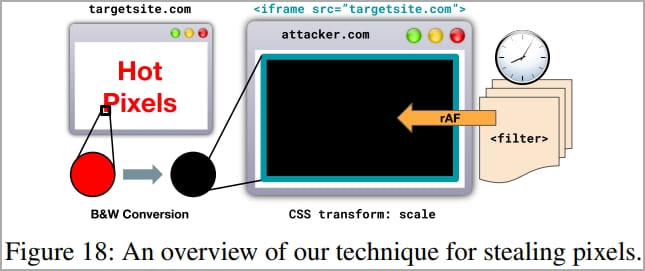
How “Hot Pixels” works
The “Hot Pixels” attack was tested on Chrome 108 and Safari 16.2, the latest versions available at the time of the study, in their default configuration, including all side-channel countermeasures.
The configuration limits the power and temperature of the processors so that data on the color of the pixels displayed on the target screen (white or black) is leaked through the frequency of the processor.
The attack mechanism is to take advantage of SVG filters to induce data-dependent execution on the target CPU or GPU, and then use JavaScript to measure computation time and frequency to infer the color of the pixel.
To steal pixels from an unaffiliated target site, researchers use an iframe element in an attacker-controlled page. The content of the iframe, which presumably contains sensitive information about the victim, is invisible but can be calculated by applying an SVG filter to it and measuring render times.
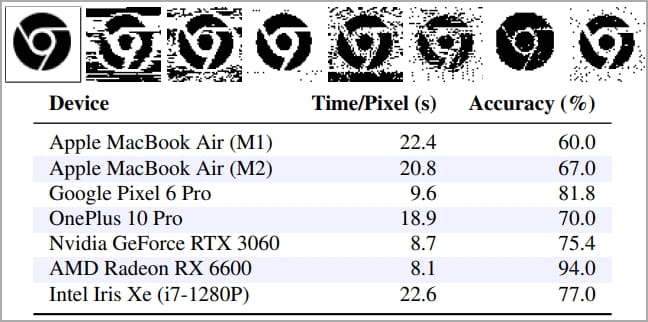
The accuracy of the measurements ranged between 60% and 94%, and the time required to decipher each pixel was between 8.1 and 22.4 seconds.
The “most leaky” device was AMD Radeon RX 6600, while the best protected devices seem to be Apple’s.
Explore browsing history
Safari is not impacted by the attack described in the previous section due to the blocking of the transmission of cookies on iframe elements that do not have the same origin as the parent page. Therefore, the pixels loaded on the iframe will not contain any user data.
However, researchers have discovered that Safari is vulnerable to a subtype of Hot Pixels attack, which can compromise user privacy by sniffing their browsing history.
The designed method is to place links to sensitive pages on the site controlled by the attacker and then use the SVG filtering technique to infer the color.
The hyperlinks of visited sites should have a different color than those the target has never visited, so the basic principles of Hot Pixels can be applied to infer the target’s browsing history.
Also, since the entire hyperlink would have the same color, it would only take a single pixel from each, so very large lists of hyperlinks can be parsed in a short time.
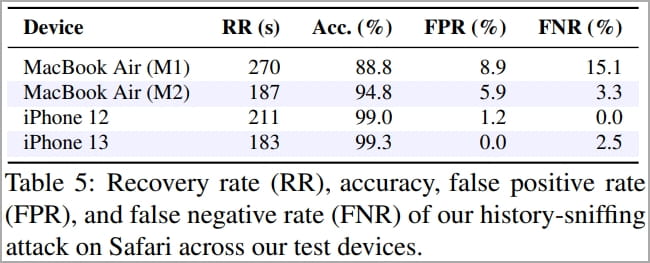
The accuracy of the data stolen in this attack reached 99.3% on the iPhone 13, with only 2.5% false negatives and a recovery rate of 183 seconds for 50 hyperlinks.
Conclusion
The researchers disclosed their findings to Apple, Nvidia, AMD, Qualcomm, Intel and Google in March. All vendors have acknowledged the issues and are working to mitigate them.
Hot Pixel attacks only work well on devices that quickly reach a steady state of power usage, such as smartphones, although the data leak rate is generally low.
However, vendors and affected stakeholders are already discussing solutions to reported issues, such as restricting the use of SVG filters on iframes over the HTML standard.
The Chrome team is already working on implementing the cookie isolation mechanism found in Safari that prevents cookies from being loaded on orphaned iframes.
There are also proposals to restrict access to sensors that give thermal, power, and frequency readings to unauthorized users at the operating system level.
More details on the Hot Pixels attack can be found on the technical document published by the researchers earlier this week.
[ad_2]
Source link
