[ad_1]

A new “File Archivers in the Browser” phishing kit abuses ZIP domains by displaying fake WinRAR or Windows File Explorer windows in the browser to trick users into launching malicious files.
Earlier this month, Google started offering the ability to register ZIP TLD domains, such as bleepingcomputer.zip, for hosting websites or email addresses.
Since the release of the TLD, there have been a lot of debate whether it is in error and whether it could pose a cybersecurity risk to users.
While some experts believe the fears are overblown, the main concern is that some sites automatically turn a string ending in “.zip”, such as setup.zip, into a clickable link that could be used to spread malware or phishing attacks.
For example, if you send someone instructions on how to download a file called setup.zip, Twitter will automatically turn setup.zip into a link, tricking people into thinking they should click on it to download the file.
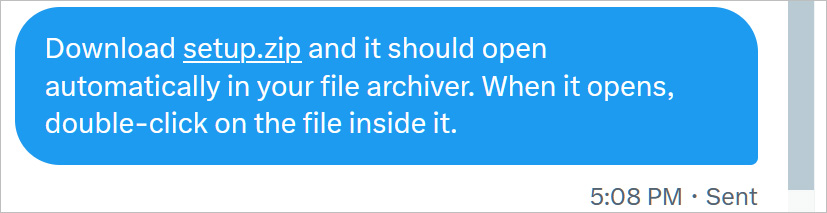
Source: BleepingComputer
When you click this link, your browser attempts to open the https://setup.zip site, which may redirect you to another site, display an HTML page, or prompt you to download a file.
However, as with all malware or phishing campaigns, you must first convince a user to open a file, which can be difficult.
An in-browser file archiver
security researcher sird0x has developed a smart phishing toolkit that allows you to create fake WinRar instances in browser and file explorer windows that are displayed on ZIP domains to trick users into thinking they are a .zip file open.
“With this phishing attack, you simulate file archiving software (e.g. WinRAR) in the browser and use a .zip domain to make it appear more legitimate,” says one new blog post by the researcher.
In a demo shared with BleepingComputer, the toolkit can be used to embed a fake WinRar window directly into the browser when a .zip domain is opened, making it look like the user has opened a ZIP archive and sees now the files it contains.
Although it looks nice when viewed in the browser, it shines as a pop-up window, as you can remove the address bar and scroll bar, leaving what appears to be a WinRar window displayed on the screen , as shown below.
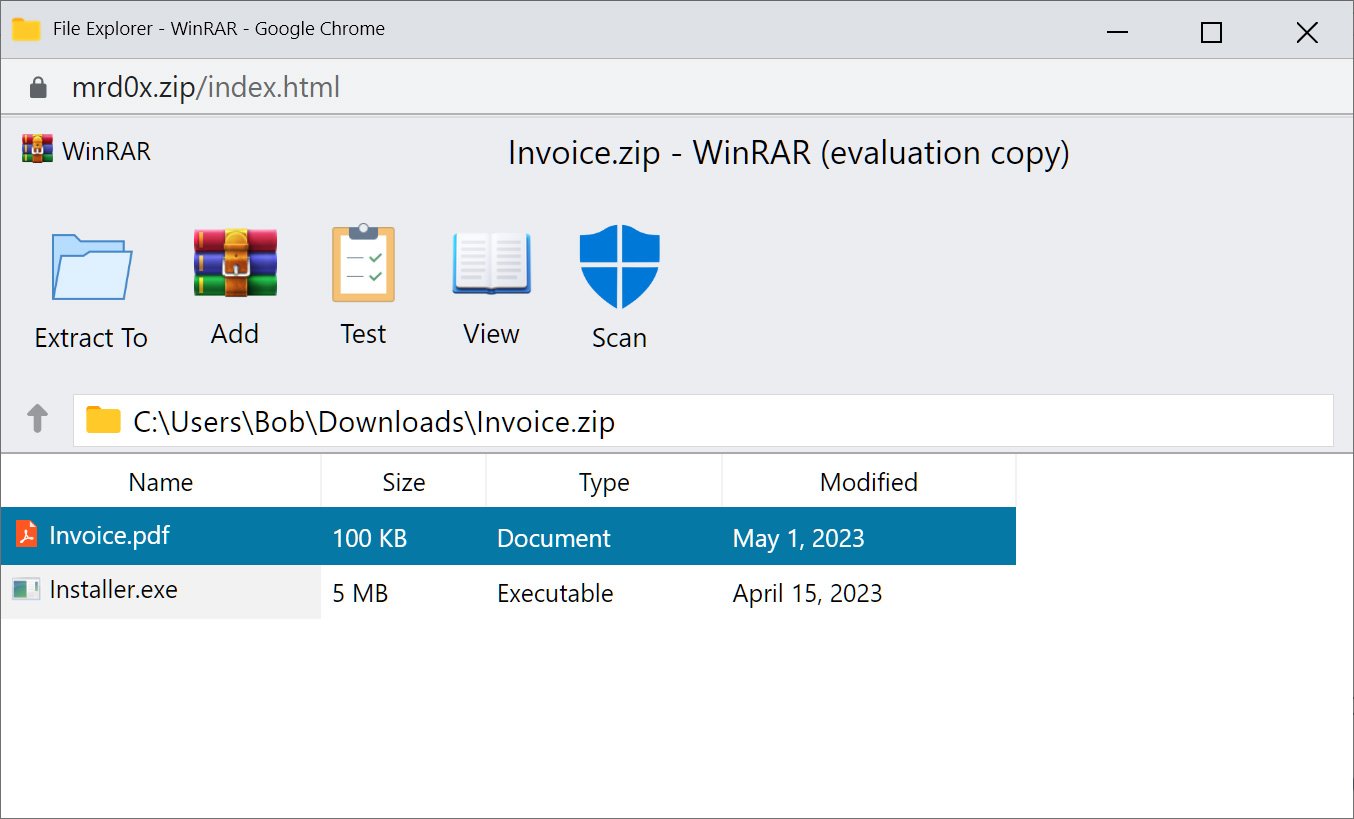
Source: BleepingComputer
To make the fake WinRar window even more convincing, the researchers implemented a fake security scan button which, when clicked, indicates that the files have been scanned and no threats have been detected.
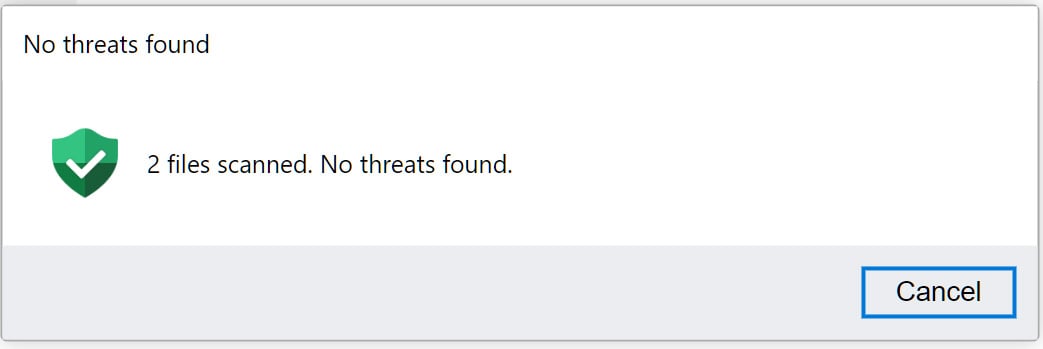
Source: BleepingComputer
Although the toolkit still shows the browser’s address bar, it’s still likely that some users think it’s a legitimate WinRar archive. Also, some creative CSS and HTML could probably be used to further refine the toolkit.
mr.d0x has also created another variant that displays a fake Windows File Explorer in the browser claiming to open a ZIP file. This model is more of a work in progress, so some elements are missing.
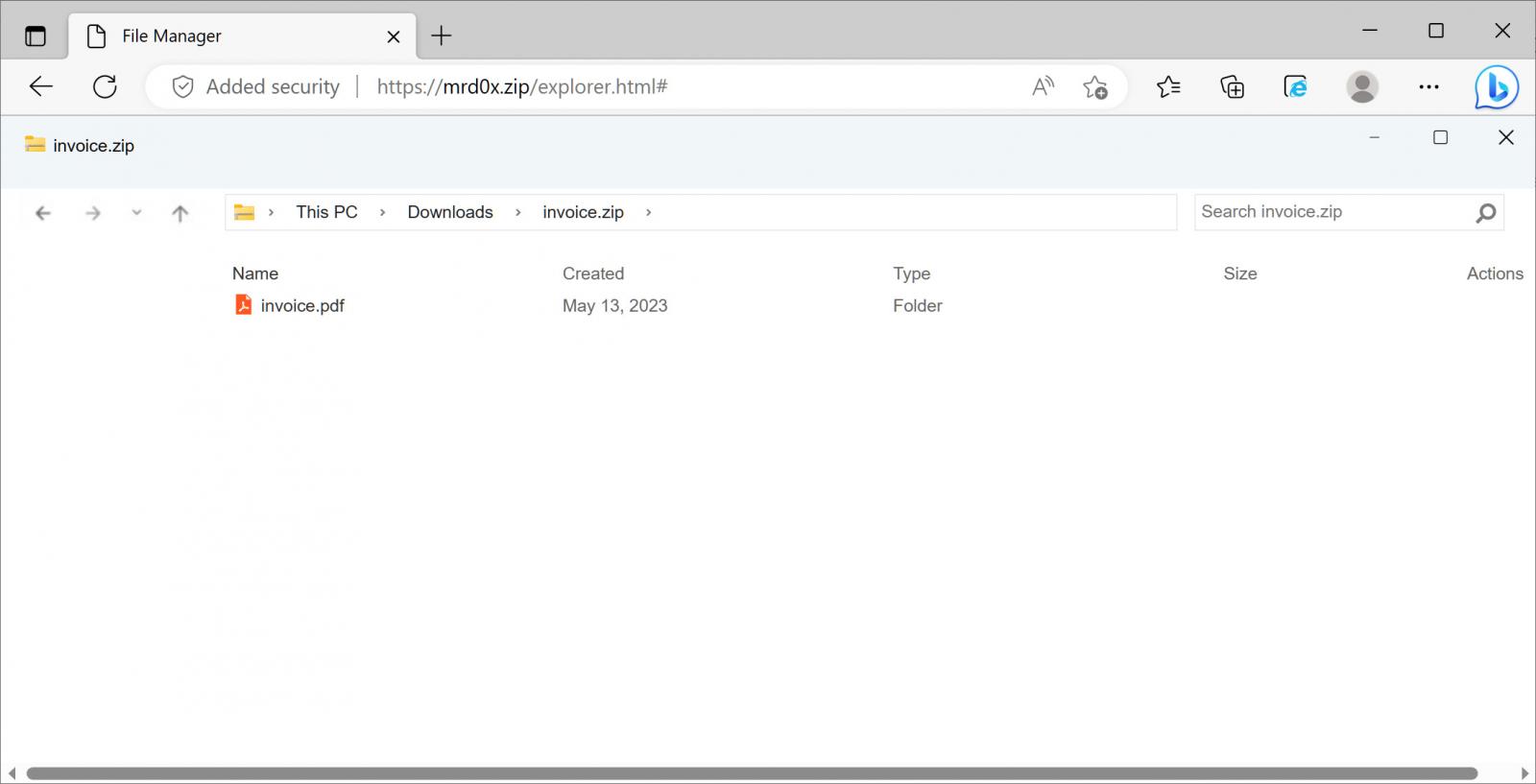
Source: BleepingComputer
Abuse of the Phishing Toolkit
mr.d0x explains that this phishing toolkit can be used for both credential theft and malware distribution.
For example, if a user double-clicks on a PDF in the fake WinRar window, it could redirect the visitor to another page asking for their login credentials to properly view the file.
The toolkit can also be used to spread malware by displaying a PDF file that downloads an .exe file with the same name instead when clicked. For example, the fake archive window might display a document.pdf file, but when clicked, the browser downloads document.pdf.exe.
Since Windows does not display file extensions by default, the user will simply see a PDF file in their downloads folder and possibly double-click on it, not realizing that it is an executable.
Of particular interest is the way Windows searches for files and, when not found, attempts to open the search string in a browser. If this string is a legitimate domain, the website will be opened. otherwise, it will display search results from Bing.
If someone saves a zip domain identical to a common file name and someone searches in Windows, the operating system will automatically open the site in the browser.
If this site hosted the “File Archivers in the Browser” phishing kit, it might trick a user into believing that WinRar is displaying a genuine ZIP archive.
This technique illustrates how ZIP domains can be abused to create clever phishing attacks and malware delivery or credential theft.
mr.d0x is known for its previous clever phishing toolkits, such as use VNC for phishing to bypass MFA and the Technique of the browser in the browser. Threat actors used the latter steal steam credentials.
[ad_2]
Source link
