[ad_1]

The malicious QBot operation began exploiting a DLL hacking flaw in the Windows 10 WordPad program to infect computers, using the legitimate program to evade detection by security software.
A DLL is a library file containing functions that can be used by several programs at the same time. When an application is launched, it attempts to load all required DLLs.
It does this by looking for the DLL in specific Windows folders and, when found, loading it. However, Windows applications will prioritize DLLs in the same folder as the executable, loading them before all others.
DLL hijacking occurs when a malicious actor creates a malicious DLL with the same name as a legitimate DLL and places it in the first Windows search path, usually the same folder as the executable. When this executable is launched, it loads the malware DLL rather than the legitimate DLL and executes all the malicious commands it contains.
QBot abuses WordPad DLL hijack flaw
QBot, also known as Qakbot, is Windows malware that started out as a banking Trojan but evolved into a malware dropper. Ransomware gangs, including basta black, EgregoreAnd Prolockhave partnered with the malware operation to gain initial access to corporate networks to carry out extortion attacks.
Security researcher and member of Cryptolaemus ProxyLife tells BleepingComputer that a new QBot phishing campaign began abusing a DLL hijacking vulnerability in the Windows 10 WordPad executable, write.exe.
Although BleepingComputer did not see the original phishing emails, ProxyLife told us they contained a link to download a file.
When someone clicks the link, they download a randomly named ZIP archive from a remote host.
This ZIP file contains two files: document.exe (the Windows 10 WordPad executable) and a DLL file named edputil.dll (used for DLL hijacking).
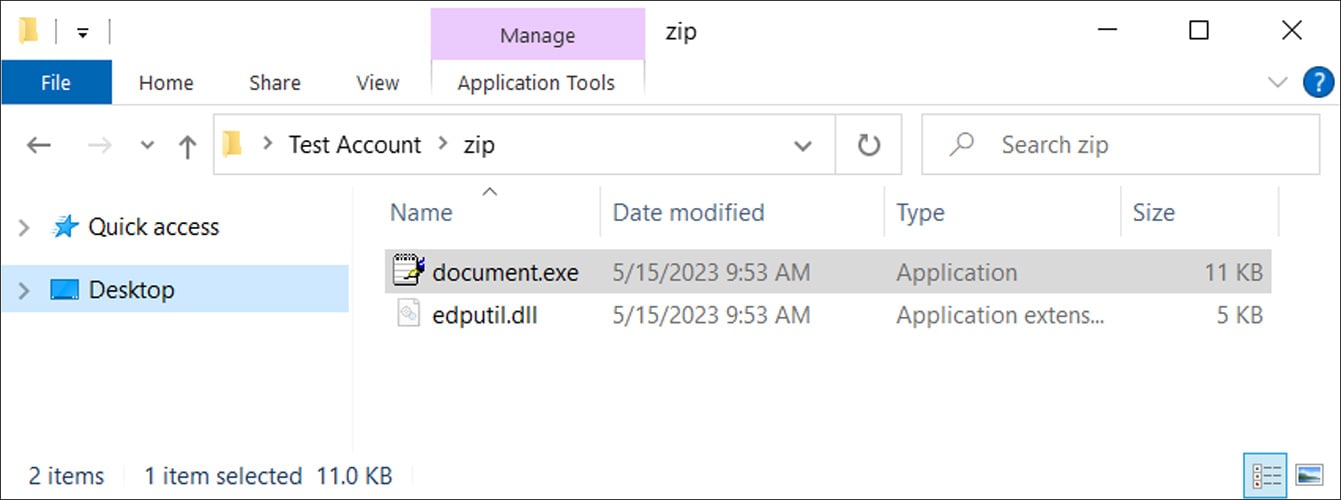
Source: BleepingComputer
As you can see in the properties of the document.exe file, it is simply a renamed copy of the legitimate Write.exe executable used to launch the Windows 10 WordPad document editor.
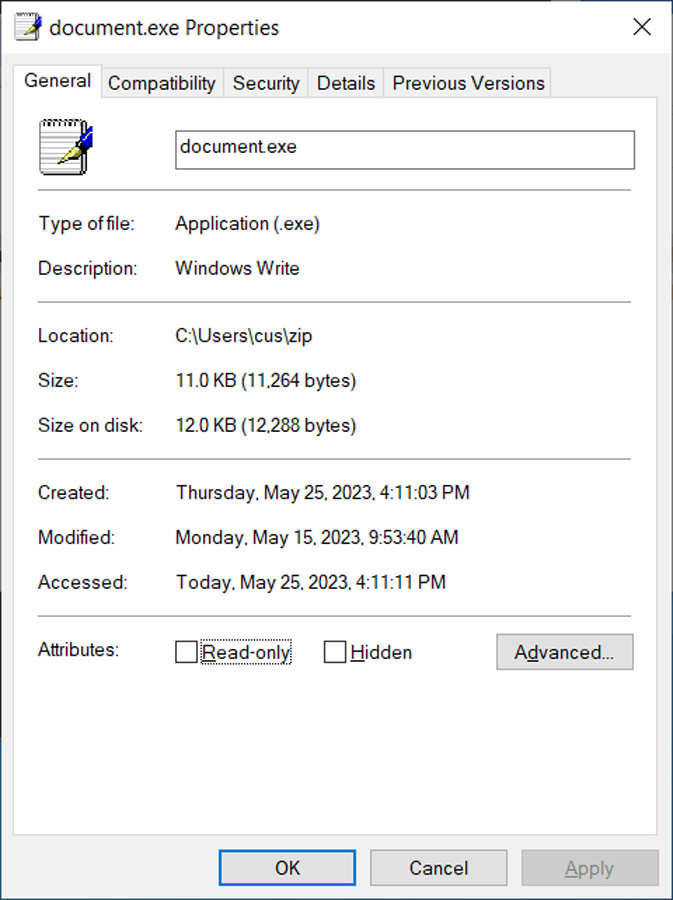
Source: BleepingComputer
When document.exe is launched, it automatically attempts to load a legitimate DLL file called edputil.dll, which is normally located in the C:\Windows\System32 folder.
However, when the executable attempts to load edputil.dll, it does not check for it in a specific folder and will load any DLL of the same name found in the same folder as the document.exe executable.
This allows threat actors to perform a DLL hijack by creating a malicious version of the edputil.dll DLL and storing it in the same folder as document.exe to be loaded instead.
After the DLL was loaded, ProxyLife told BleepingComputer that the malware uses C:\Windows\system32\curl.exe to download a DLL camouflaged as a PNG file from a remote host.
This PNG file (actually a DLL) is then run using rundll32.exe with the following command:
rundll32 c:\users\public\default.png,printQBot will now run quietly in the background, stealing emails for use in other phishing attacks and optionally downloading other payloads, such as Cobalt Strike (a post-exploitation toolkit used by actors of the threat to gain initial access to the infected device).
This device will then be used as an anchor point to spread laterally throughout the network, typically resulting in corporate data theft and ransomware attacks.
By installing QBot through a reliable program such as Windows 10 WordPad (write.exe), threat actors hope that the security software will not flag the malware as malicious.
However, using curl.exe means that this method of infection will only work on Windows 10 and later, as earlier versions of the operating system do not include the Curl program.
For the most part, this shouldn’t be a problem, as older versions of Windows were phased out after reaching end of support.
Currently, Operation QBot has transitioned to other methods of infection over the past few weeks, but it’s not uncommon for them to switch to previous tactics in later campaigns.
[ad_2]
Source link
