[ad_1]

North Korean hackers are using trojanized versions of the PuTTY SSH client to deploy backdoors to targets’ devices as part of a fake Amazon job evaluation.
A new element of this campaign is the use of a trojanized version of the PuTTY and KiTTY SSH utility to deploy a backdoor, which in this case is ‘AIRDRY.V2’.
According Beggar technical report released today, the threat group responsible for this campaign is “UNC4034” (aka “Temp.Hermit” or “Labyrinth Chollima”).
The group’s latest activities appear to be a continuation of the ‘Operation Dream Job‘, which has been ongoing since June 2020, this time targeting media companies.
“In July 2022, during proactive threat hunting activities at a company in the media industry, Mandiant Managed Defense identified a new spear phishing methodology employed by the threat cluster tracked as UNC4034,” Mandiant explained.
Using the PuTTY SSH Client to Drop Malware
The attack begins with threat actors approaching their targets via email with a lucrative job offer at Amazon, then communicating with WhatsApp, where they share an ISO file (“amazon_assessment.iso”).
The ISO includes a text file (“readme.txt”) containing an IP address and login credentials and a trojanized version of putty (PuTTY.exe), a very popular open source SSH console application.
BleepingComputer is also aware of threat actors using spoofing Kitty SSH clienta fork of PuTTY, using the filename ‘Amazon-Kitty.exe‘.
Although it is unknown what discussions took place between the threat actors and the victims, the hackers probably told the victim to open the ISO and use the SSH tool and the credentials. credentials attached to connect to the host and perform a skills assessment.
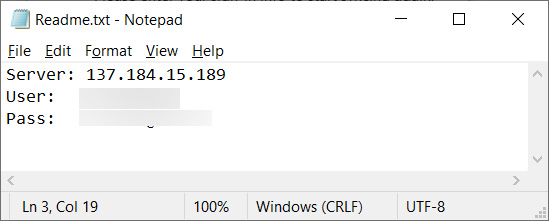
Source: BleepingComputer
However, the PuTTY shared by the hackers was modified to include a malicious payload in its data section, making the faked version much larger than the legitimate version.
As the PuTTY executable was compiled from the legitimate program, it is fully functional and looks exactly like the legitimate version.
However, hackers modified PuTTY’s connect_to_host() so that upon successful SSH login using the attached credentials, the program deploys a malicious DAVESHELL shellcode payload in the form of a DLL (“colorui.dll”) containing Themida.
To make launching the shellcode stealthy, the malicious PuTTY uses a search order hijacking vulnerability in “colorcpl.exe”, the legitimate Windows color management tool, to load the malicious DLL.
DAVESHELL functions as the final payload dropper, the AIRDRY.V2 backdoor malware, which is executed directly in memory.
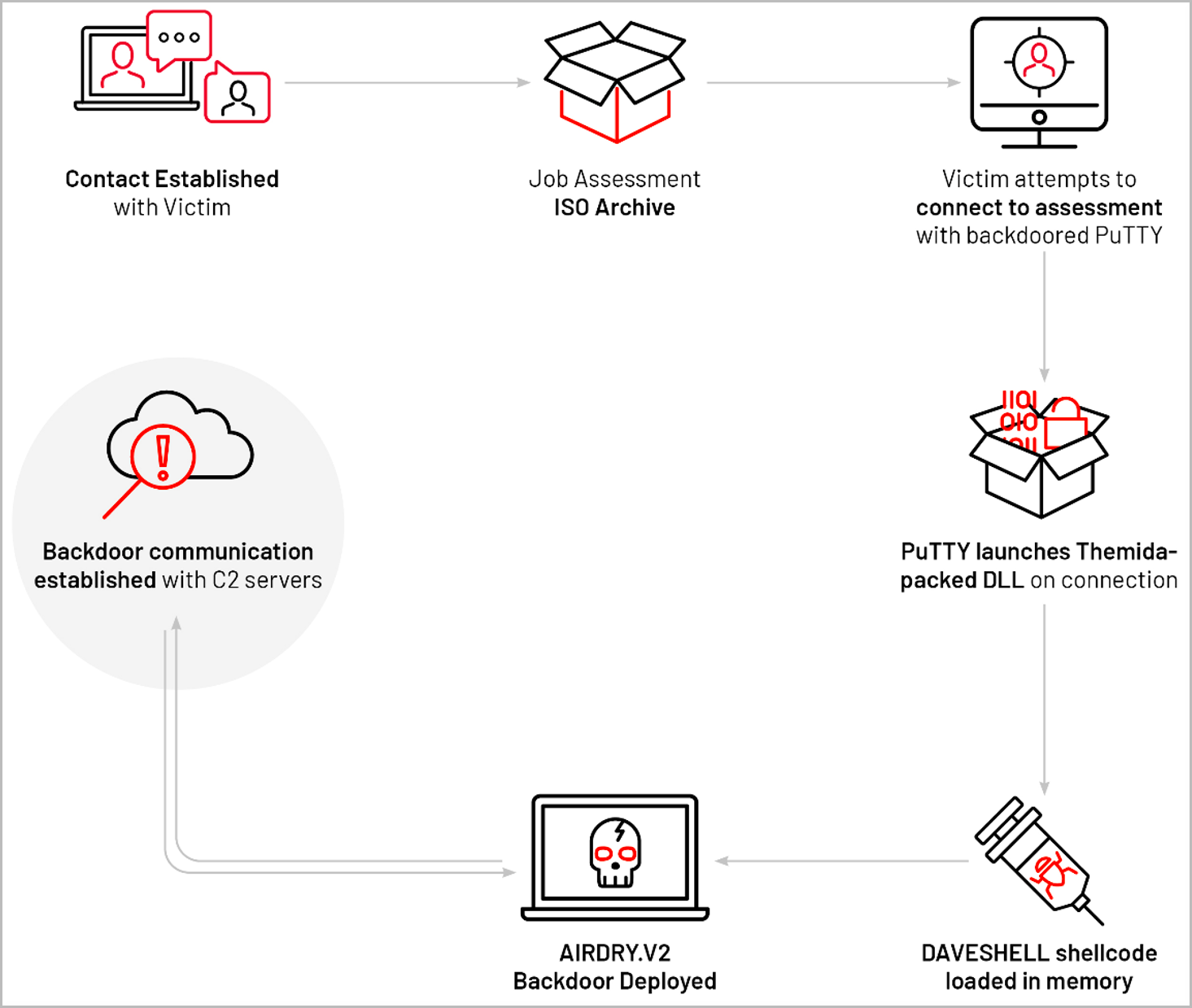
AIRDRY.V2 can communicate over HTTP, file, or SMB via a named pipe, attempting to connect five times to one of three hard-coded C2 addresses before going into a 60-second sleep.
While the backdoor has the technical ability to use a proxy server and monitor active RDP sessions, the version Mandiant reviewed has these features disabled by default.
- The commands supported by AIRDRY.V2 are the following nine:
- Download basic system information
- Update the beacon interval based on a value provided by the C2 server
- Disable until new start date and time
- Download current configuration
- Update configuration
- Stay alive
- Update beacon interval based on a value in config
- Update the AES key used to encrypt C2 requests and configuration data
- Download and run a plugin in memory
Compared to the previous version of AIRDRY, the new variant supports fewer commands, but in-memory plug-in execution and AES key update for C2 communications are new features.
Reducing the number of supported commands does not impact the versatility of the backdoor, as fetching plugins from the C2 opens up new potential for more surgical attacks.
To check for trojanized versions of PuTTY, you can check the properties of the executable and make sure it is digitally signed by “Simon Tatham”.
Unfortunately, the legitimate KiTTY program is normally not signed by the developer and must instead be uploaded to a virus scanning service, such as VirusTotal, to check for malicious detections.
[ad_2]
Source link
