[ad_1]

An Iran-aligned hacking group is using an elaborate new phishing technique in which it uses multiple people and email accounts to lure targets into believing it’s a realistic email conversation.
Attackers email targets while CCing another email address under their control, then respond from that email, initiating a fake conversation.
Called “multi-persona imitation” (MPI) by the Proofpoint researchers who first noticed it, the technique relies on the psychological principle of “social proof” to obscure logical thinking and add an element of reliability to phishing threads.
TA453 is an Iranian threat group believed to operate from the IRGC (Islamic Revolutionary Guard Corps), seen previously impersonate journalists target academics and policy experts from the Middle East.
Multi-person identity theft
TA453’s new tactic requires much more effort on their part to carry out phishing attacks, as each target must be trapped in an elaborate realistic conversation held by fake personas, or puppets socks.
However, the extra effort pays off, as it creates a realistic email exchange, which makes the conversation seem legitimate.
An example shared in The Proofpoint Report dated June 2022, with the sender impersonating the Director of Research at FRPI and the email sent to the target and cc’d to a Director of Global Attitudes Research at the PEW Research Center.
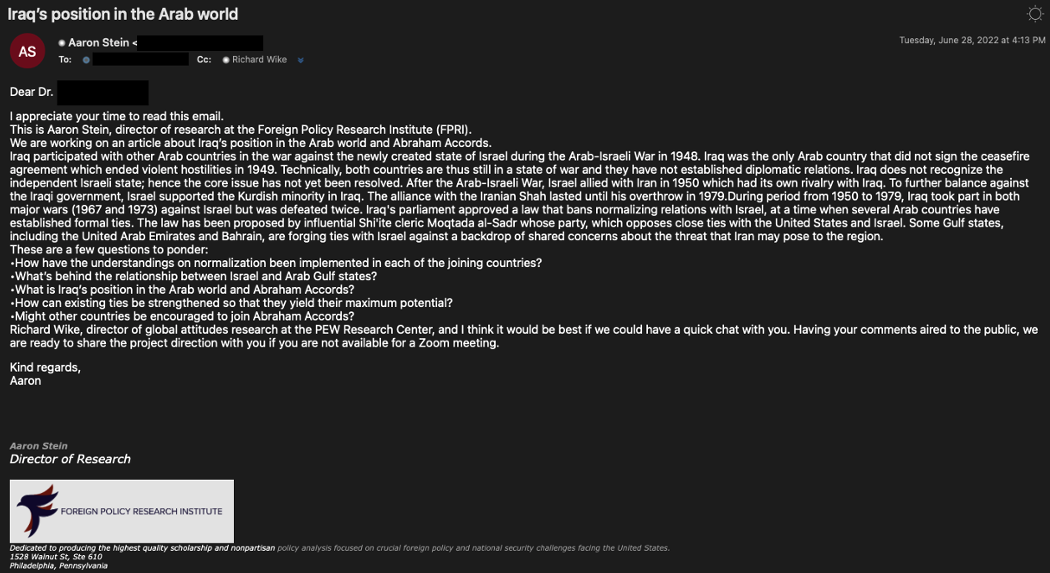
The next day, the impersonated PEW director responded to questions sent by the FRPI director, creating the false impression of an honest conversation that would entice the target to join.
In another case seen by Proofpoint, involving scientists specializing in genome research, the CCed persona responded with a OneDrive link that led to the download of a DOCX document containing malicious macros.
In a third MPI phishing attack launched by TA453 against two academics specializing in nuclear arms control, threat actors copied three personalities, opting for an even more complex attack.
.png)
In all cases, the threat actors used personal email addresses (Gmail, Outlook, AOL, Hotmail) for senders and cc’s instead of spoofed institution addresses, which is a clear sign of suspicious activity.
The malicious payload
The documents that targets were tricked into downloading via OneDrive links in TA453’s recent campaign are password-protected files that perform template injection.
“The downloaded template, dubbed Korg by Proofpoint, has three macros: Module1.bas, Module2.bas, and ThisDocument.cls,” the report details.
“The macros collect information such as username, list of running processes, and user’s public IP address from my-ip.io and then exfiltrate this information to the using the Telegram API.”
The researchers couldn’t get past the step of tagging reconnaissance information, but speculated that additional exploitation occurs in subsequent steps to give remote threat actors capabilities to execute code on hosts. .
[ad_2]
Source link
