[ad_1]
Aftermarket enterprise network equipment hides sensitive data that hackers could use to break into corporate environments or obtain customer information.
By examining several used enterprise routers, the researchers found that most of them had been improperly erased during the decommissioning process and then sold online.
Core Routers For Sale
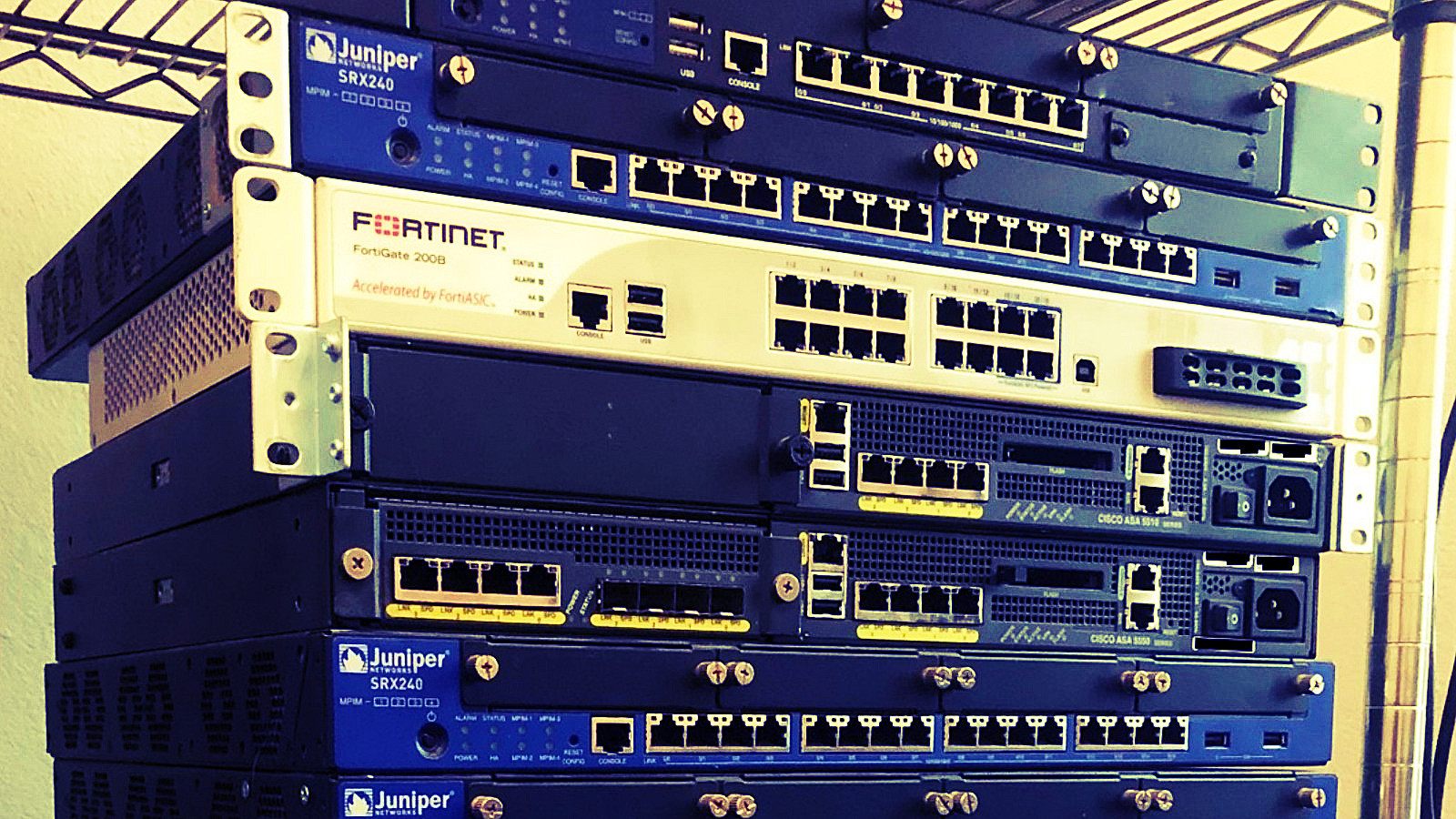
Researchers at cybersecurity firm ESET bought 18 used primary routers and found that full configuration data was still accessible on more than half of those that worked properly.
Core routers are the backbone of a large network as they connect all other network devices. They support multiple data communication interfaces and are designed to transfer IP packets at the highest speeds.
Initially, the ESET research team purchased a few used routers to set up a test environment and found that they had not been properly wiped and contained network configuration data as well as information. identifying previous owners.
The equipment purchased included four devices from Cisco (ASA 5500), three from Fortinet (Fortigate series) and 11 from Juniper Networks (SRX Series Services Gateway).
In a report earlier this week, Cameron camp And Tony Anscomb say one device was dead on arrival and eliminated from testing and that two of them were a mirror of each other and counted as one in the evaluation results.
Of the remaining 16 devices, only five were properly erased and only two were hardened, making some data more difficult to access.
For most of them, however, it was possible to access full configuration data, which is a wealth of detail about the owner, how he configured the network, and the connections between other systems.
With corporate network devices, the administrator must run a few commands to safely erase the configuration and reset it. Without this, routers can be booted into a recovery mode that can verify how it was configured.
The secrets of the network
The researchers claim that some of the routers retained client information, data enabling third-party connections to the network, and even “credentials to connect to other networks as a relying party.”
Additionally, eight of the nine routers that exposed full configuration data also contained authentication keys and router-to-router hashes.
The list of trade secrets extended to comprehensive maps of sensitive applications hosted on-premises or in the cloud. Some examples include Microsoft Exchange, Salesforce, SharePoint, Spiceworks, VMware Horizon, and SQL.
“Due to the granularity of specific applications and versions used in some cases, known exploits could be deployed on network topology that an attacker has already mapped” – ESET
Such extensive insider details are typically reserved for “highly trained personnel” such as network administrators and their managers, the researchers explain.
An adversary with access to this type of information could easily come up with a plan for an attack path that would take him deep inside the network undetected.
“With this level of detail, impersonating a network or internal hosts would be much easier for an attacker, especially since devices often contain VPN credentials or other easily hacked authentication tokens. – ESET
Based on the details discovered in the routers, several of them were in managed IT vendor environments, which operate the networks of large enterprises.
One device even belonged to a managed security service provider (MSSP) that managed the networks of hundreds of customers in various industries (eg, education, finance, healthcare, manufacturing).
Following their findings, the researchers emphasize the importance of properly cleaning network devices before disposing of them. Businesses should have procedures in place for the secure destruction and disposal of their digital equipment.
The researchers also warn that using a third-party service for this activity isn’t always a good idea. After informing the owner of a router of their findings, they learned that the company had used such a service. “It obviously didn’t go as planned.”
The advice here is to follow the device manufacturer’s recommendations to clean the equipment of potentially sensitive data and return it to a factory default state.
[ad_2]
Source link
