[ad_1]

The BlackCat (aka ALPHV) ransomware group runs malicious advertising campaigns to lure people to fake pages that mimic the official website of the WinSCP file transfer application for Windows, but instead push installers infested with malware.
WinSCP (Windows Secure Copy) is a free and open-source SFTP, FTP, S3, SCP client and file manager with SSH file transfer capabilities with 400,000 weekly downloads on SourceForge alone.
BlackCat uses the program as a decoy to potentially infect the computers of system administrators, web administrators, and IT professionals for initial access to valuable corporate networks.
This previously unknown ALPHV ransomware infection vector was discovered by analysts from Trend Microwho spotted ad campaigns promoting the fake pages on Google and Bing search pages.
From WinSCP to CobaltStrike
The BlackCat attack observed by Trend Micro starts with the victim searching for “WinSCP Download” on Bing or Google and gets promoted malicious results ranked above secure WinSCP download sites.
Victims click on these advertisements and visit a website that hosts tutorials on performing automated file transfers using WinSCP.
These sites do not contain anything malicious that might escape detection by Google’s anti-abuse crawlers, but redirect visitors to a clone of the official WinSCP site with a download button. These clones use domain names similar to the real winscp.net domain for the utility, like winsccp[.]com.
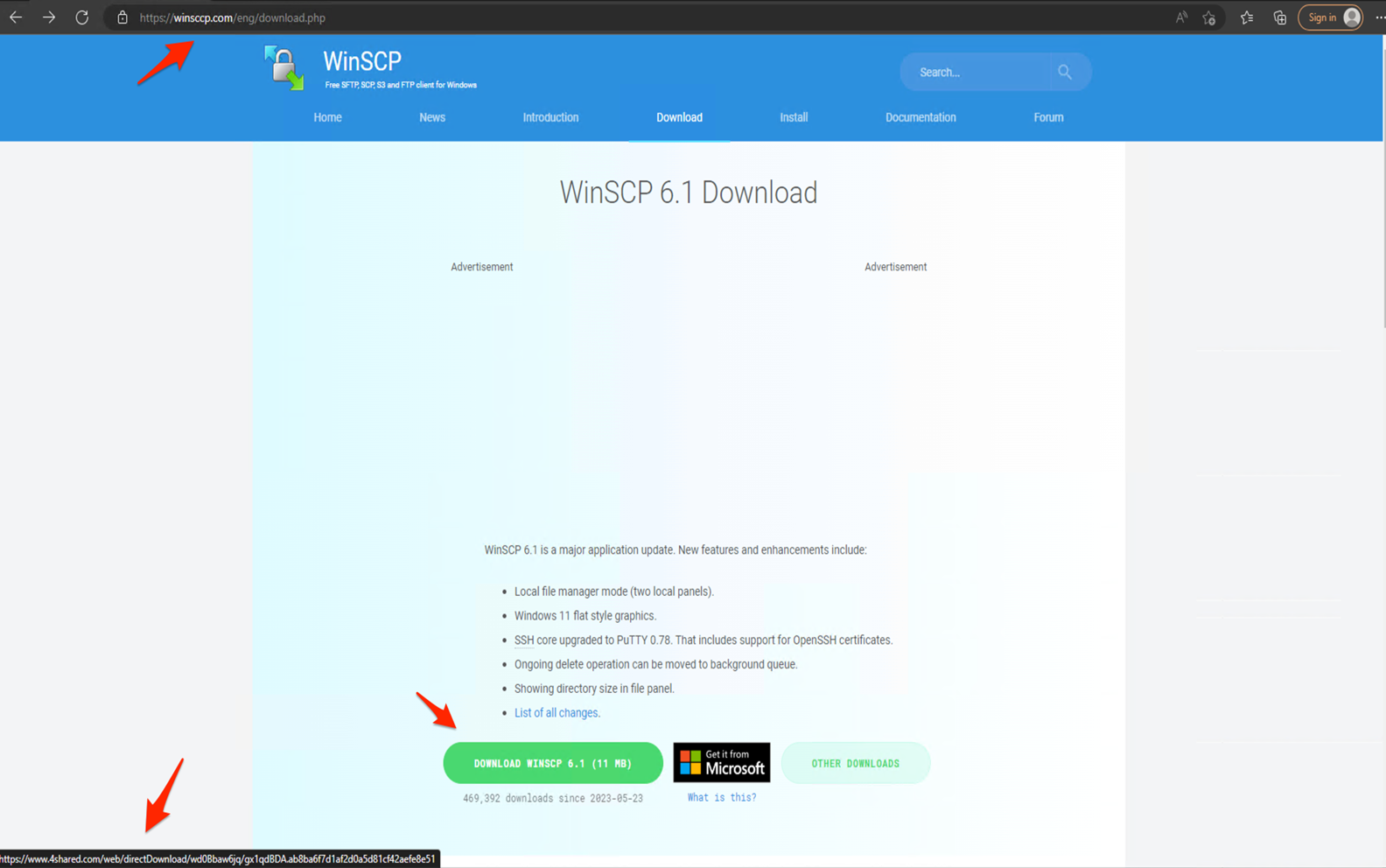
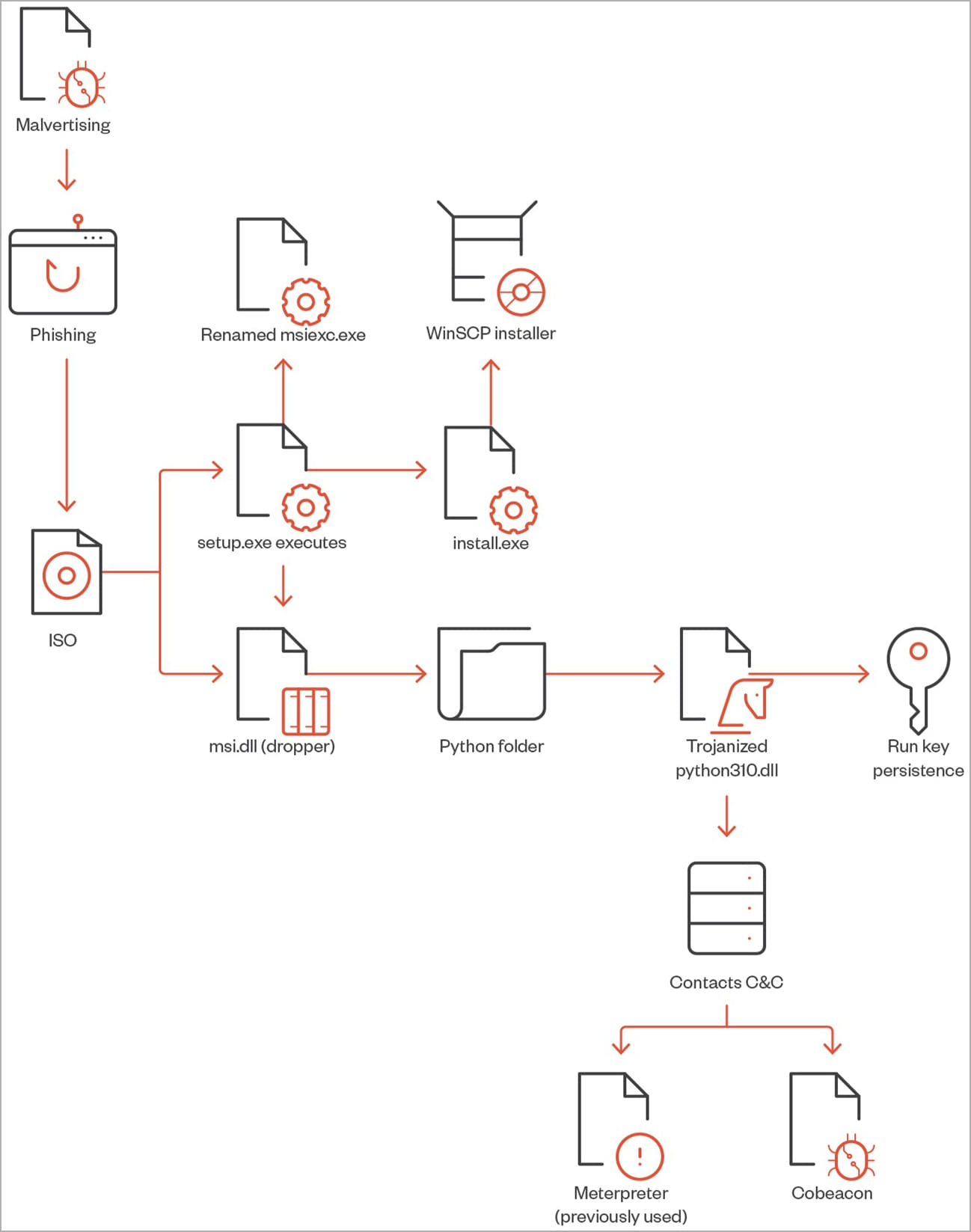
The victim clicks the button and receives an ISO file containing “setup.exe” and “msi.dll”, the former being the decoy to be launched by the user and the latter being the malware launcher triggered by the executable.
“Once setup.exe is executed, it will call the msi.dll which will later extract a Python folder from the RCDATA DLL section as an actual WinSCP installer to install on the machine,” the Trend Micro report explains.
This process also installs a python310.dll trojan and creates a persistence mechanism by creating an execution key named “Python” and value “C:\Users\Public\Music\python\pythonw.exe”.
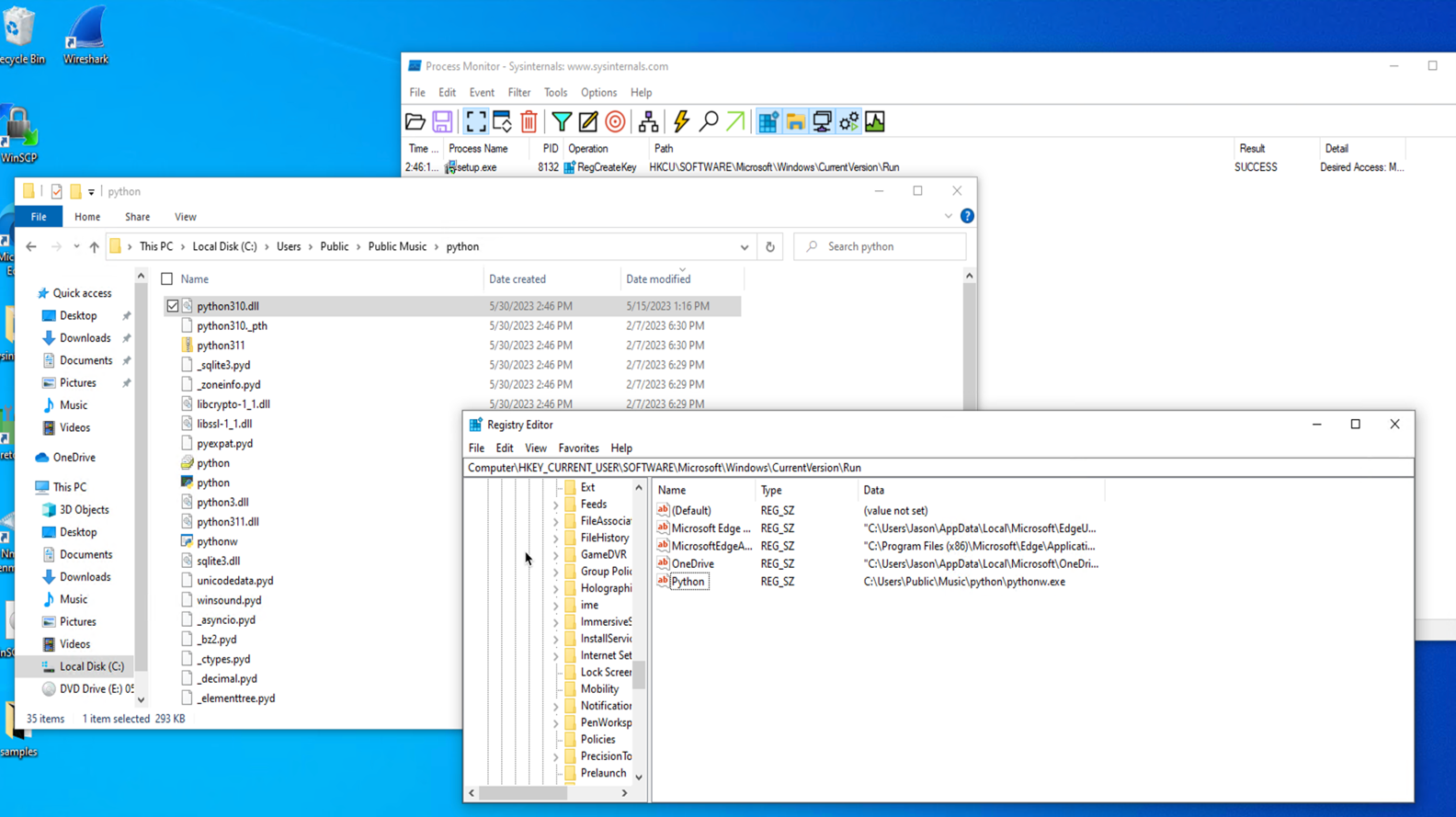
The pythonw.exe executable loads a modified obfuscated python310.dll that contains a Cobalt Strike tag that connects to a command and control server address.
Other tools used by ALPHV
With Cobalt Strike running on the system, it’s easy to run additional scripts, pick up tools for lateral movement, and generally deepen the trade-off.
Trend Micro analysts noticed that ALPHV operators used the following tools in the following phases:
- AdFind: command line tool used to retrieve information from Active Directory (AD).
- PowerShell commands used to collect user data, extract ZIP files and run scripts.
- AccessChk64: command-line tool used for the recognition of user and group permissions.
- findstr: command line tool used to find passwords in XML files.
- Power View: PowerSploit script used in AD discovery and enumeration.
- Python scripting used to run the LaZagne password recovery tool and obtain Veeam credentials.
- PsExec, BitsAdminAnd Loopused for lateral movement
- AnyDesk: Legitimate remote management tool abused to maintain persistence
- KillAV BAT script used to disable or bypass antivirus and antimalware programs.
- putty Secure Copy client used to exfiltrate collected information from the hacked system.
In addition to the above tools, ALPHV also used the SpyBoy”terminator“, an EDR and antivirus disabler sold by threat actors on Russian-speaking hacking forums for up to $3,000.
Recent research from CrowdStrike confirmed that “Terminator” is able to bypass several Windows security tools by using a “bring your own vulnerable driver” (BYOVD) mechanism to elevate privileges on the system and disable them.
Trend Micro claims to have linked the above TTPs to confirmed ALPHV ransomware infections. It also found a Clop ransomware file in one of the investigated C2 domains, so the threat actor may be affiliated with multiple ransomware operations.
[ad_2]
Source link
