[ad_1]

Microsoft has denied claims by so-called “Anonymous Sudan” hacktivists that they hacked into the company’s servers and stole the credentials of 30 million customer accounts.
Anonymous Sudan is notorious for its debilitating Distributed Denial of Service (DDoS) attacks against Western entities These last months. The group has confirmed their affiliation with pro-Russian hacktivists like Killnet.
Last month, Microsoft admitted that Anonymous Sudan was responsible for service disruptions and outages in early June that impacted several of its services, including Azure, Outlook and OneDrive.
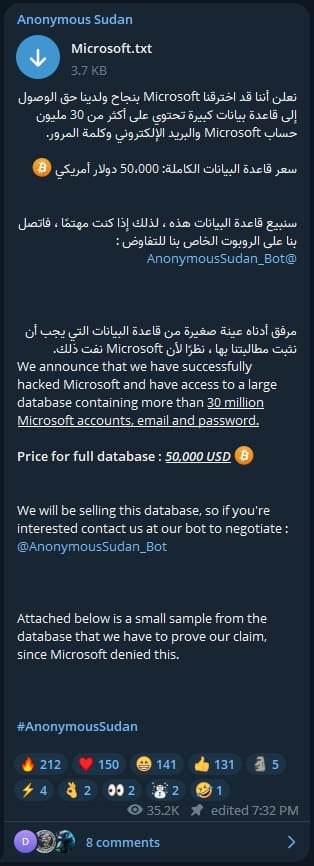
Yesterday, the hacktivists claimed to have “succeeded in hacking Microsoft” and “accessed a vast database containing more than 30 million Microsoft accounts, emails and passwords”.
Anonymous Sudan offered to sell this database to interested parties for $50,000 and urged interested buyers to get in touch with their Telegram bot to arrange the purchase of the data.
(Computer Beep)
The message even includes a sample of the data they offered (allegedly stolen from Microsoft) as evidence of the breach and warned that Microsoft would deny these allegations.
The group provided 100 pairs of credentials but their origin could not be verified (old data, the result of a breach at a third-party service provider, stolen from Microsoft systems).
BleepingComputer contacted Microsoft to seek comment on the validity of Anonymous Sudan’s statement and a company spokesperson categorically denied any data breach allegations.
“At this time, our analysis of the data shows that this is not a legitimate claim and an aggregation of data,” a company representative told BleepingComputer.
“We have seen no evidence that our customer data has been accessed or compromised” – Microsoft spokesperson
It’s unclear at this time if Microsoft’s investigation is complete or ongoing. Also, the company’s reaction to the potential release of the data remains to be seen.
[ad_2]
Source link
