[ad_1]

A phishing campaign that security researchers have named SmugX and attributed to a Chinese threat actor is targeting embassies and foreign ministries in the UK, France, Sweden, Ukraine, the Czech Republic, Hungary and Slovakia since December 2022.
Researchers at cybersecurity firm Check Point analyzed the attacks and observed overlaps with activity previously attributed to tracked advanced persistent threat (APT) groups like Mustang Panda and RedDelta.
In examining the decoy documents, researchers have noticed that they are generally thematic around European domestic and foreign policies.
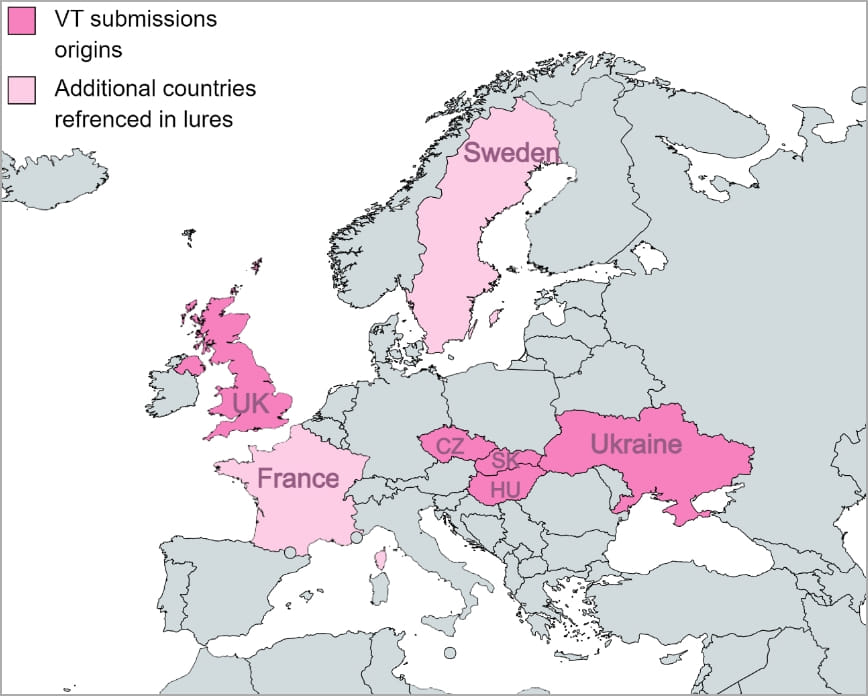
Among the samples that Check Point collected during the investigation are:
- A letter from the Serbian Embassy in Budapest
- a document setting out the priorities of the Swedish Presidency of the Council of the European Union
- an invitation to a diplomatic conference issued by the Hungarian Ministry of Foreign Affairs
- an article about two Chinese human rights lawyers
The decoys used in the SmugX campaign betray the threat actor’s target profile and indicate that espionage is the likely goal of the campaign.

SmugX Attack Chains
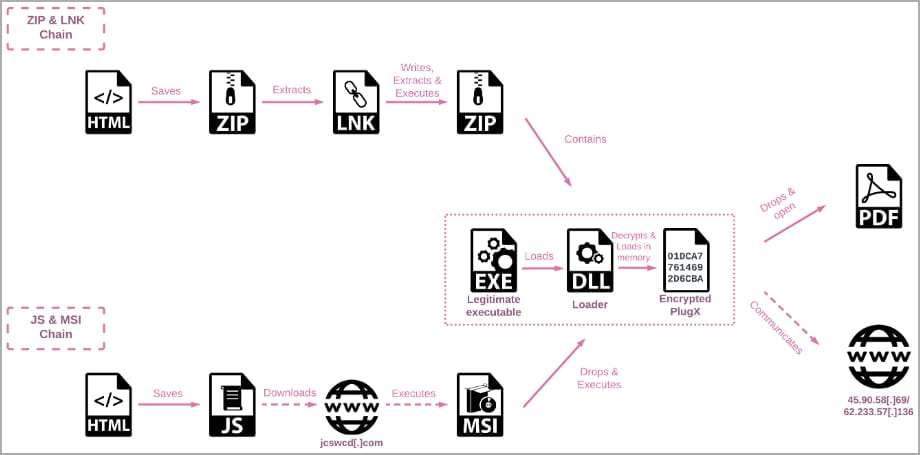
Check Point has observed that SmugX attacks rely on two infection chains, both of which use the HTML smuggling technique to hide malicious payloads in encoded strings of HTML documents attached to the decoy message.
A variant of the campaign delivers a ZIP archive with a malicious LNK file that runs PowerShell when launched, to extract an archive and save it to the Windows temporary directory.
The extracted archive contains three files, one being a legitimate executable (either “robotaskbaricon.exe” or “passwordgenerator.exe”) of an older version of the RoboForm password manager that allowed loading unrelated DLL files with the application, a technique called DLL sideloading.
The other two files are a malicious DLL (Roboform.dll) which is loaded using one of two legitimate executables, and “data.dat” – which contains the PlugX Remote Access Trojan (RAT ) run through PowerShell.
The second attack chain variant uses HTML smuggling to download a JavaScript file that executes an MSI file after downloading it from the attacker’s command and control (C2) server.
The MSI then creates a new folder in the “%appdata%\Local” directory and stores three files: a hacked legitimate executable, the loader DLL, and the encrypted PlugX payload (‘data.dat’).
Again, the legitimate program is executed and the PlugX malware is loaded into memory via DLL sideloading in an attempt to evade detection.
To ensure persistence, the malware creates a hidden directory where it stores legitimate executable and malicious DLL files and adds the program to the “Run” registry key.
Once PlugX is installed and executed on the victim’s machine, it can load a deceptive PDF file to distract the victim and reduce their suspicion.
PlugX is a modular RAT that has been used by several Chinese APTs since 2008. It comes with a wide range of functions which include file exfiltration, taking screenshots, logging keystrokes and executing commands.
Although the malware is usually associated with APT groups, it has also been used by cybercriminals.
However, the version Check Point saw deployed in the SmugX campaign is largely the same as those seen in other recent attacks attributed to a Chinese adversary, except that it used RC4 encryption instead of XOR. .
Based on the details uncovered, Check Point researchers believe the SmugX campaign shows that Chinese threat groups are increasingly interested in European targets, likely for espionage purposes.
[ad_2]
Source link
