[ad_1]

A growing number of ransomware operations are adopting leaked Babuk ransomware source code to create Linux encryptors targeting VMware ESXi servers.
SentinelLabs security researchers observed this upward trend after spotting a rapid succession of nine Babuk-based ransomware variants that surfaced between the second half of 2022 and the first half of 2023.
“There is a noticeable trend that players are increasingly using the Babuk builder to develop ESXi and Linux ransomware,” said Alex Delamotte, threat researcher at SentinelLabs.
“This is especially evident when used by actors with fewer resources, as those actors are less likely to significantly modify Babuk’s source code.”
The list of new ransomware families that have adopted it to create new Babuk-based ESXi encryptors since H2 2022 (and related extensions added to encrypted files) include Play (.FinDom), mario (.emario), Conti POC (.conti), REvil aka Revix (.rhkrc), Cylance Ransomware, Dataf Locker, Rorschach aka bablock, Lock4And GTR locker.
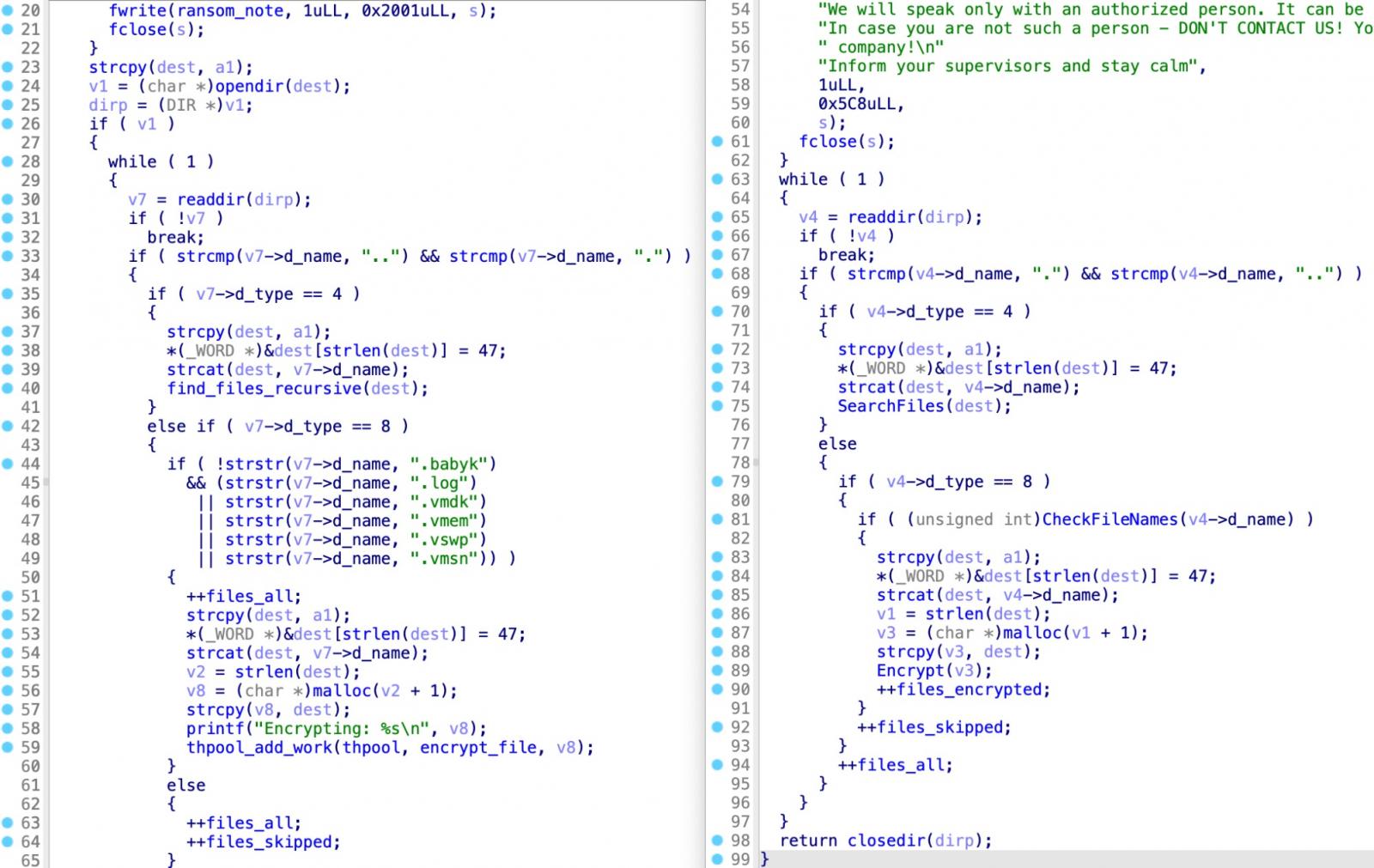
As expected, Babuk’s leaked constructor has allowed attackers to target Linux systems even if they lack the expertise to develop their own custom ransomware strains.
Unfortunately, its use by other ransomware families has also made it much more difficult to identify attackers, as the adoption of the same tools by multiple actors significantly complicates attribution efforts.
These are in addition to many other unique, non-Babuk-based ransomware strains targeting VMware ESXi virtual machines that have been discovered in the wild for several years.
Some of those found in nature are Royal ransomware, Nevada Ransomware, GwisinLocker ransomware, Luna ransomware, RedAlert ransomwareas well as basta black, LockBit, BlackMatter, AvosLocker, Hello Kitty, REvil, RansomEXXAnd Hive.
Source code and decryption keys leaked
THE Babuk (aka Babyk and Babuk Locker) ransomware operation surfaced early 2021 by targeting businesses in double extortion attacks.
The gang’s ransomware source code was leaked on a Russian-speaking hacking forum in September 2021, with VMware ESXi, NAS and Windows encryptors, as well as compiled encryptors and decryptors for some of the gang’s victims.
After attacking Washington DC Metropolitan Police Department (MPD) in April 2021, the cybercrime group attracted unwanted attention from US law enforcement and claimed to have shut down the operation after it began to feel the heat.
The Babuk members went their separate ways, with the admin launching the Ramp cybercrime forum and the other core members relaunching the ransomware as Babuk V2.
[ad_2]
Source link
