[ad_1]

One of the most popular WordPress Elementor plugins, “Essential Addons for Elementor”, has been found to be vulnerable to an unauthenticated elevation of privilege that could allow remote attacks to gain admin rights on the site .
Essential Addons for Elementor is a library of 90 extensions for the ‘Elementor’ page builder, used by over a million WordPress websites.
The flaw, discovered by PatchStack on May 8, 2023, is identified as CVE-2023-32243 and is an unauthenticated privilege escalation vulnerability on the plugin’s password reset functionality, impacting versions 5.4.0 to 5.7.1.
“[By exploiting the flaw] It is possible to reset the password of any user as long as we know their username, thus being able to reset the password of the administrator and log in to their account,” it reads. PatchStack Bulletin.
“This vulnerability occurs because this password reset function does not validate a password reset key and directly changes the given user’s password.”
The consequences of this flaw are significant and include unauthorized access to private information, defacing or removal of websites, distribution of malware to visitors, and brand repercussions such as loss of trust and issues. legal compliance.
While remote attackers do not need to authenticate to exploit the CVE-2023-32243 flaw, they must know a username on the system they are targeting for the malicious password reset.
(Un)conditional password reset
As PatchStack explains in its report, the attacker should set a random value in the POST entries ‘page_id’ and ‘widget_id’ so that the plugin does not produce an error message that could arouse the suspicion of the administrator of the site.
The attacker must also provide the correct nonce value on the ‘eael-resetpassword-nonce’ to validate the password reset request and set a new password on the ‘eael-pass1’ and ‘eael-pass2’ parameters .
“At this point, the question may be how we can get our hands on the essential element or nonce value,” says PatchStack.
“It turns out that this nonce value is present in the main page of the WordPress site since it will be set in the $this->localize_objects variable by the load_commnon_asset function:”
Assuming a valid username has been set on the ‘rp_login’ parameter, the code will replace the targeted user’s password with the new password provided by the attacker, essentially giving them control of the account.
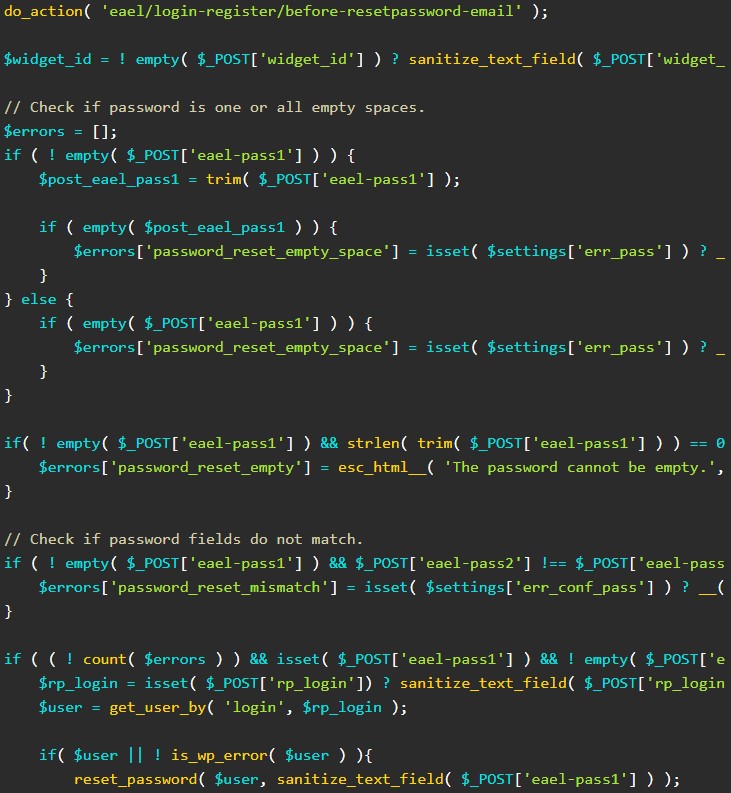
Fixing this problem was simple, the security company comments, because the plugin vendor had to add a function that checks whether a password reset key is present and legitimate in reset requests.
The fix was released with Essential Addons for Elementor version 5.7.2, which was made available today. It is recommended that all users of the plugin upgrade to the latest version as soon as possible.
[ad_2]
Source link
