[ad_1]

A Russian hacking group tracked as TA473, aka “Winter Vivern”, has been actively exploiting vulnerabilities in unpatched Zimbra endpoints since February 2023 to steal emails from NATO officials, governments, military personnel and diplomats.
Two weeks ago, Sentinel Labs reported on a recent operation by “Winter Viven” using sites impersonating European cybercrime agencies to distribute malware pretending to be a virus scanner.
Today, point of proof released a new report on how the threat actor exploits CVE-2022-27926 on Zimbra Collaboration servers to access the communications of NATO-aligned organizations and individuals.
Target Zimbra
Winter Viven attacks begin with the threat actor scanning unpatched webmail platforms using the Acunetix tool’s vulnerability scanner.
Then the hackers send a phishing email from a compromised address, which is spoofed to appear as someone the target knows or is somehow relevant to their organization.
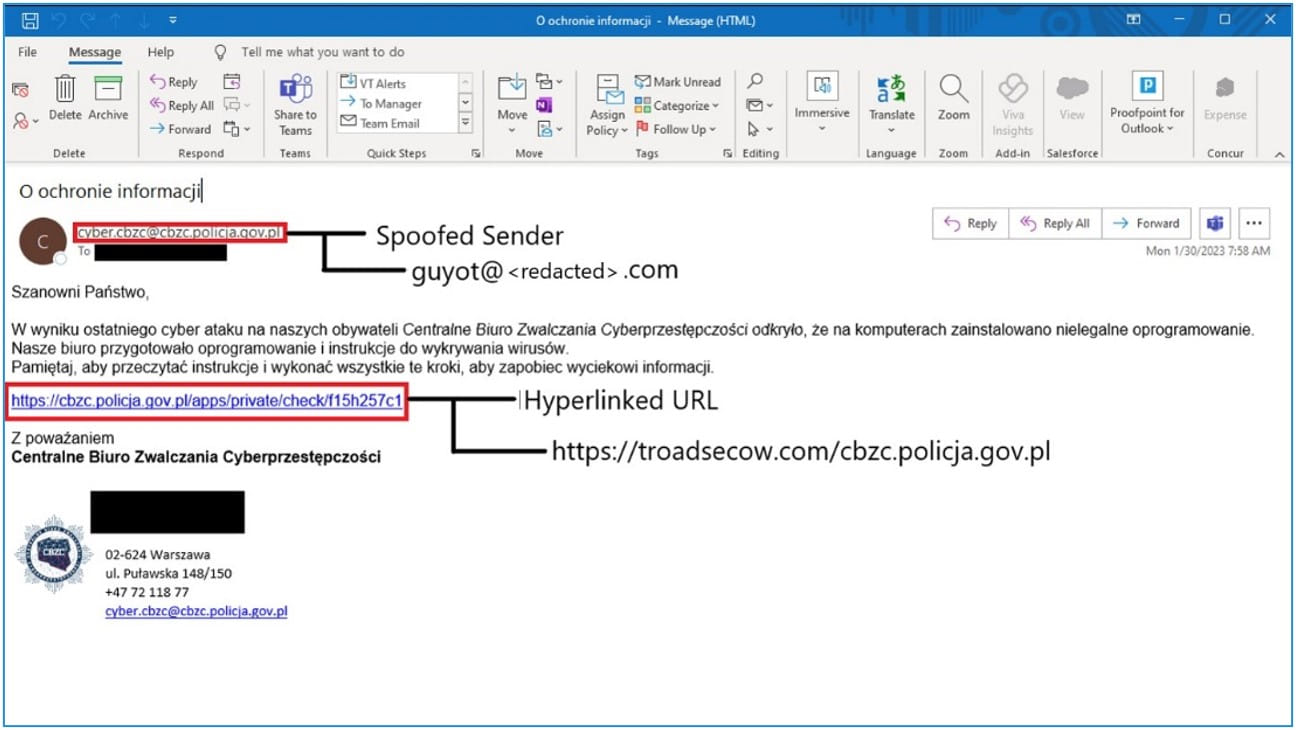
The emails contain a link that exploits CVE-2022-27926 in the target’s compromised Zimbra infrastructure to inject other JavaScript payloads into the webpage.
These payloads are then used to steal usernames, passwords, and cookie tokens received from the compromised Zimbra endpoint. This information gives hackers free access to the targets’ email accounts.
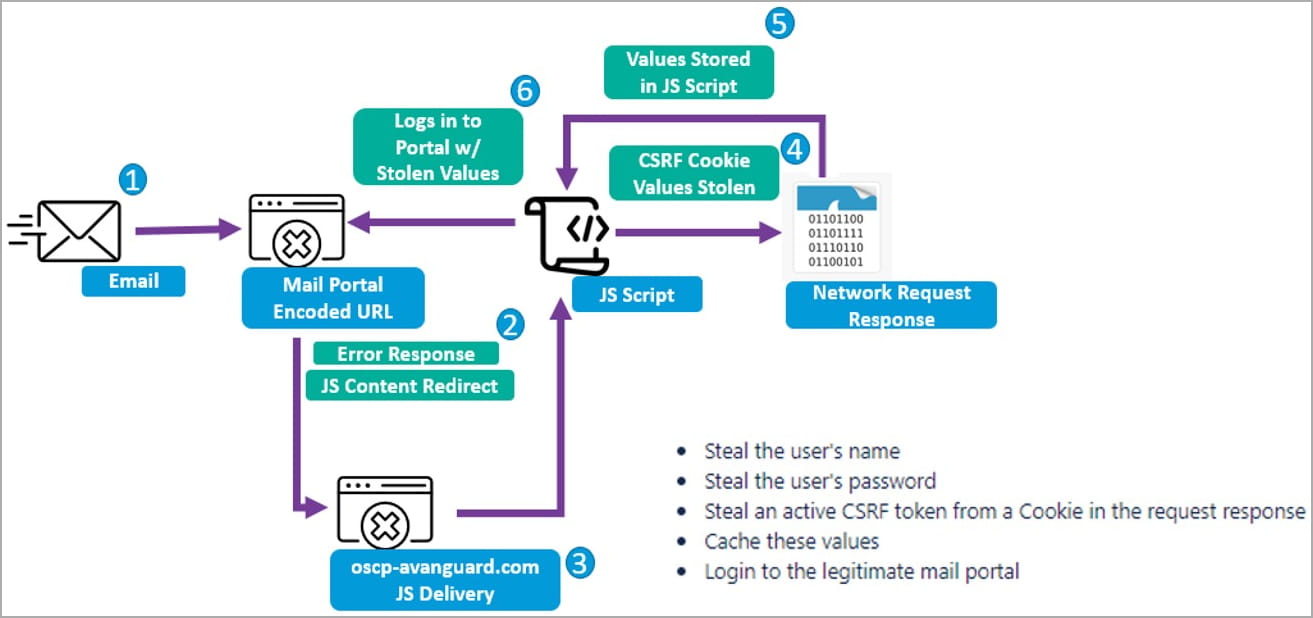
“These blocks of CSRF JavaScript code are executed by the server that hosts a vulnerable webmail instance,” Proofpoint explains in the report.
“Furthermore, this JavaScript replicates and relies on the emulation of the native webmail portal JavaScript to return key web request details that indicate the targets username, password, and CSRF token. .”
“In some cases, researchers observed that TA473 also specifically targeted RoundCube webmail request tokens.”
This detail demonstrates threat actors’ diligence in pre-attack reconnaissance, determining which portal their target is using before creating the phishing emails, and setting the landing page function.
Besides the three layers of base64 obfuscation applied on the malicious JavaScript to make analysis more complicated, “Winter Vivern” also included parts of the legitimate JavaScript that runs in a native webmail portal, intermingling with normal operations and decreasing the probability of detection.
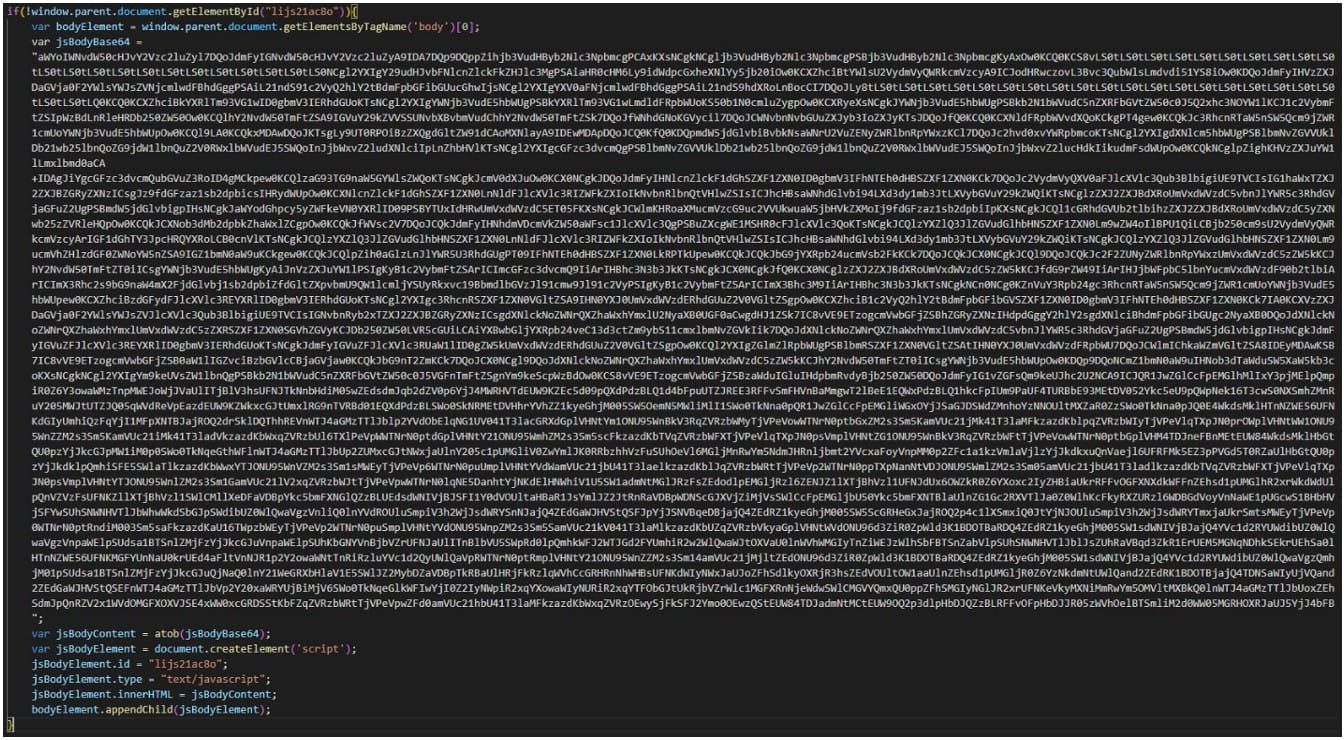
Finally, threat actors can access sensitive information on compromised webmails or maintain their grip to monitor communications over a period of time. Additionally, hackers can use the hacked accounts to conduct side phishing attacks and further infiltrate target organizations.
While the researchers say “Winter Viven” isn’t particularly sophisticated, they follow an effective operational approach that works even against high-profile targets that fail to apply patches quickly enough.
In this case, CVE-2022-27926 has been fixed in Zimbra Collaboration 9.0.0 P24, released in April 2022.
Considering that the first attacks were observed in February 2023, the time to apply the security update is measured at at least ten months.
[ad_2]
Source link
