[ad_1]

Hackers add malicious functionality to self-extracting WinRAR archives that contain harmless decoy files, allowing them to plant backdoors without triggering the security agent on the target system.
Self-extracting (SFX) archives created with compression software like WinRAR or 7-Zip are essentially executables that contain archived data with an integrated decompression stub (the code to decompress the data). Access to these files can be password protected to prevent unauthorized access.
The purpose of SFX files is to simplify the distribution of archived data to users who do not have a utility to extract the package.
source: crowdstrike
Researchers from cybersecurity firm CrowdStrike spotted the SFX abuse during a recent incident response investigation.
SFX attacks in the wild
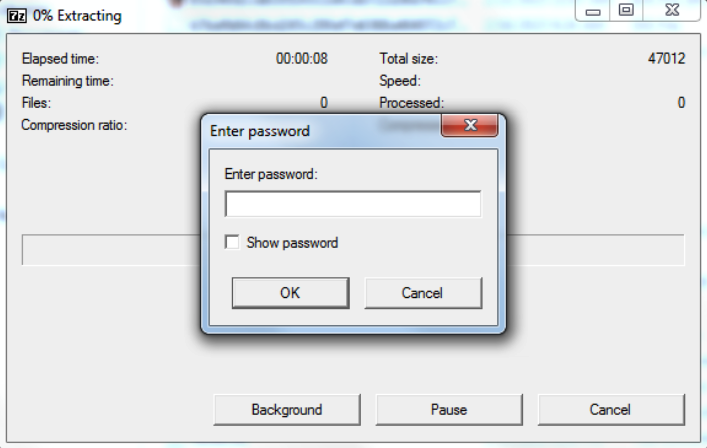
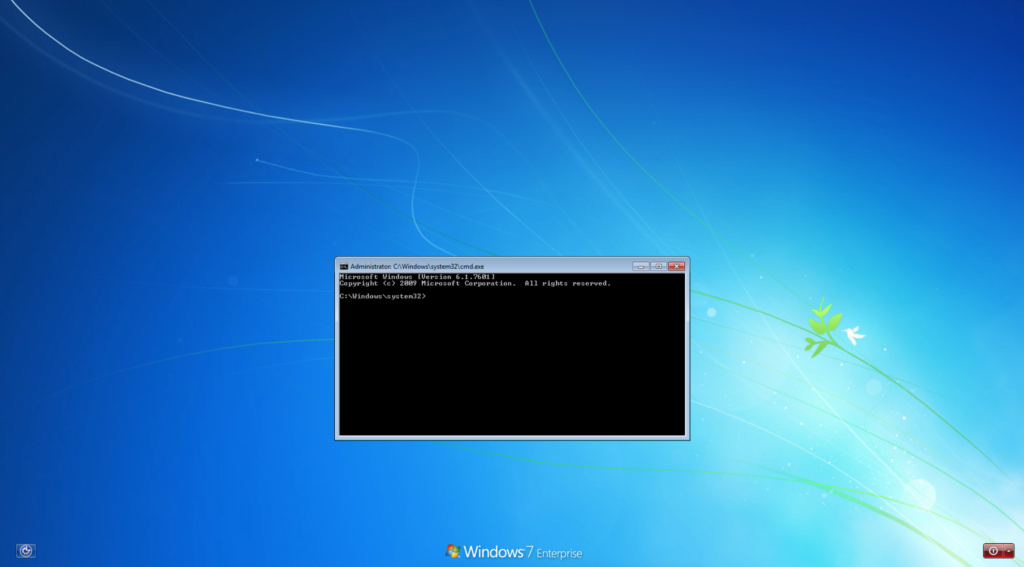
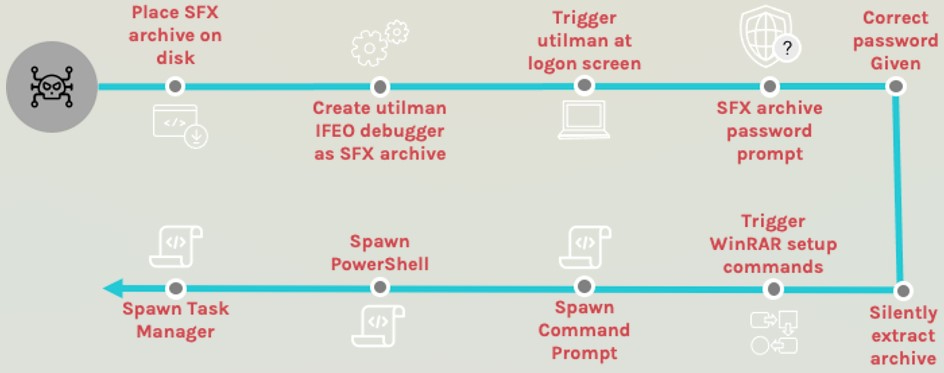
Crowdstrike’s analysis discovered an adversary who used stolen credentials to abuse ‘utilman.exe’ and configured it to launch a password-protected SFX file that had been planted on the system before.
Utilman is an accessibility application that can be run before user login, often abused by hackers to bypass system authentication.
source: crowdstrike
The SFX file triggered by utilman.exe is password protected and contains an empty text file that serves as a decoy.
The real function of SFX file is to abuse WinRAR configuration options to run PowerShell, Windows Command Prompt (cmd.exe) and Task Manager with system privileges.
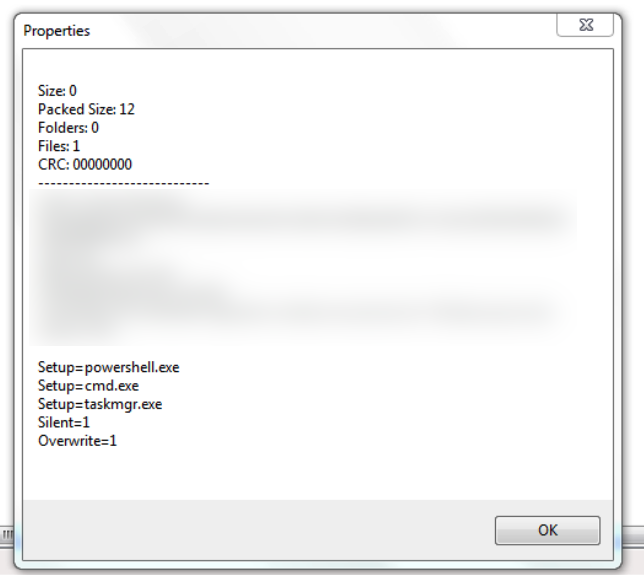
Upon closer examination of the technique used, CrowdStrike’s Jai Minton discovered that the attacker had added several commands to be executed after the target extracted the archived text file.
Although there is no malware in the archive, the threat actor added commands in the setup menu to create an SFX archive that would open a backdoor to the system.
source: crowdstrike
As seen in the image above, the comments show that the attacker has customized the SFX archive so that no dialogs or windows are displayed during the extraction process. The threat actor also added instructions to run PowerShell, Command Prompt, and Task Manager.
WinRAR offers a set of advanced SFX options that allow adding a list of executables to run automatically before or after the process, as well as overwriting existing files in the destination folder if entries with the same name exist.
“Because this SFX archive could be run from the login screen, the adversary effectively had a persistent backdoor accessible to run PowerShell, Windows Command Prompt and Task Manager with NT AUTHORITY privileges \SYSTEM, as long as the correct password was provided,” explains Crowdstrike.
“This type of attack is likely to go undetected by traditional antivirus software which looks for malware inside an archive (which is often also password protected) rather than the behavior of a SFX archive decompressor stub,” the researchers add.
source: crowdstrike
Crowdstrike claims that malicious SFX files are unlikely to be detected by traditional AV solutions. In our tests, Windows Defender reacted when we created a custom SFX archive to run PowerShell after extraction.
Microsoft security agent detected the resulting executable as a malicious script tracked as Wacatac and quarantined it. However, we only recorded this reaction once and were unable to reproduce it.
Researchers advise users to pay close attention to SFX archives and use appropriate software to verify the contents of the archive and look for potential scripts or commands programmed to run during extraction.
[ad_2]
Source link
