[ad_1]

The Cybersecurity and Infrastructure Security Agency (CISA) has warned federal agencies to patch a Zimbra Collaboration (ZCS) cross-site scripting flaw exploited by Russian hackers to steal emails during attacks targeting NATO countries.
The vulnerability (CVE-2022-27926) was abused by a Russian hacking group followed like Winter Viven and TA473 in attacks on several NATO-aligned governments‘ webmail portals to access the mailboxes of civil servants, governments, military personnel and diplomats.
Winter Viven attacks begin with hackers using the Acunetix tool’s vulnerability scanner to find vulnerable ZCS servers and send users phishing emails that spoof senders that recipients are familiar with.
Each email redirected targets to servers controlled by attackers who exploit bug CVE-2022-27926 or attempt to trick recipients into handing over their credentials.
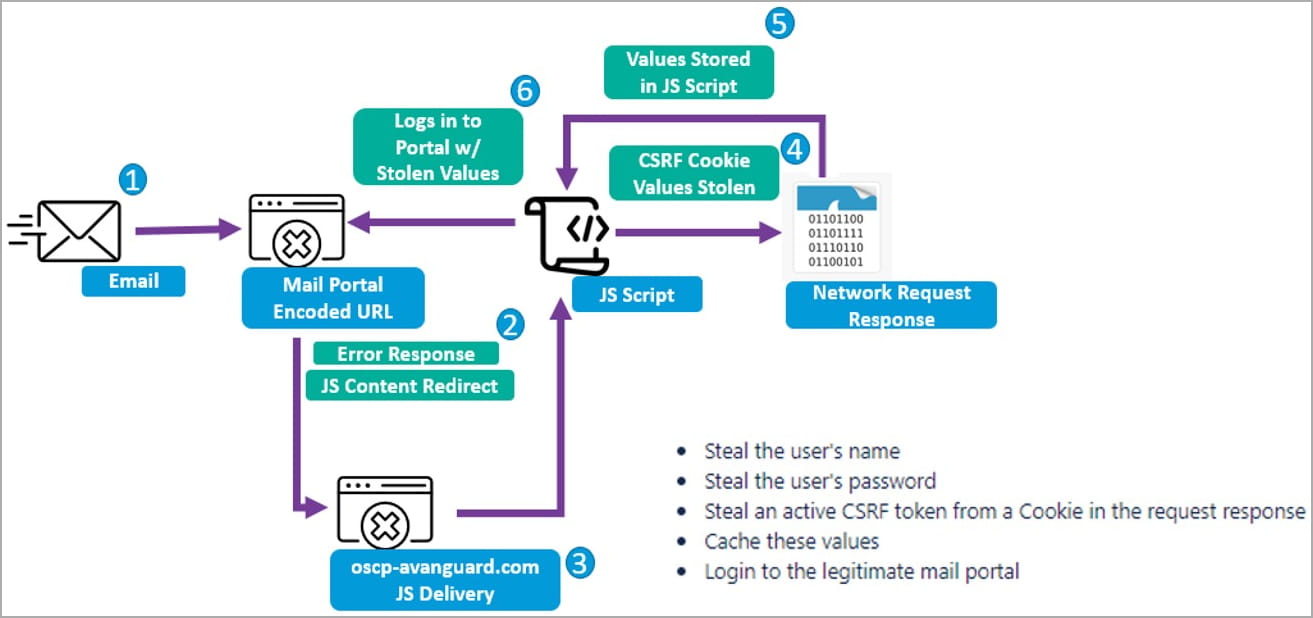
When targeted by an exploit, the URLs also contain a JavaScript snippet that will download a second-stage payload to launch a Cross-Site Request Forgery (CSRF) attack to steal CSRF credentials and tokens Zimbra users.
In subsequent stages, threat actors used the stolen credentials to obtain sensitive information from hacked webmail accounts or maintain persistence to track exchanged emails over time.
Hackers can also leverage compromised accounts to launch more phishing attacks and expand their infiltration of targeted organizations.
Federal agencies ordered to patch until April 24
The vulnerability was added today to CISA Catalog of known exploited vulnerabilities (KEV)a list of security vulnerabilities known to be actively exploited in the wild.
According to a binding operational directive (BOD 22-01) issued by the US Cyber Security Agency in November 2021, Federal Civilian Executive Agencies (FCEBs) must patch vulnerable systems in their networks against bugs added to the KEV list.
CISA has given FCEB agencies three weeks, until April 24, to secure their networks against attacks that would target the CVE-2022-27926 flaw.
While BOD 22-01 only applies to FCEB agencies, CISA strongly encouraged all organizations to address these bugs as a matter of priority in order to block further exploit attempts.
“These types of vulnerabilities are frequent attack vectors for malicious cyber actors and pose significant risks to the federal enterprise,” CISA said. warned Today.
On Thursday, CISA also ordered federal agencies to patch security vulnerabilities exploited as zero days in recent attacks to deploy commercial spyware on Android and iOS mobile devicesas recently revealed by Google’s Threat Analysis Group (TAG).
[ad_2]
Source link
