[ad_1]

Security researchers and experts are warning of a critical vulnerability in the Windows Message Queuing (MSMQ) middleware service patched by Microsoft in this month’s Patch Tuesday and exposing hundreds of thousands of systems to attack.
MSMQ is available on all Windows operating systems as an optional component that provides applications with network communication capabilities with “guaranteed message delivery”, and it can be enabled via PowerShell or Control Panel.
The failure (CVE-2023-21554) allows unauthenticated attackers to achieve remote code execution on unpatched Windows servers using specially crafted malicious MSMQ packets in low-complexity attacks that do not require user interaction.
The list of affected Windows server and client versions includes all currently supported versions up to the latest versions, Windows 11 22H2 and Windows Server 2022.
Redmond also attached a “more likely exploitation” tag to CVE-2023-21554, given that it is “aware of past instances of this type of vulnerability being exploited”, making it “an attractive target for attackers”.
“As such, customers who have reviewed the security update and determined its applicability in their environment should address it with a higher priority,” Microsoft said. warns.
Security researchers Wayne Low of Fortinet’s FortiGuard Lab and Haifei Li of Check Point Research were credited with reporting the flaw to Microsoft.
More than 360,000 MSMQ servers exposed to attacks
Check Point Research also shared additional details regarding the potential impact of CVE-2023-21554, claiming to have found over 360,000 internet-exposed servers running the MSMQ service and potentially vulnerable to attack.
The number of unpatched systems is likely much higher, since Check Point Research’s estimate does not include devices running the MSMQ service that are not accessible over the Internet.
Even though this is an optional Windows component that is not enabled by default on most systems, being a middleware service used by other software, the service will usually be enabled in the background when running. installation of enterprise applications and will stay on even after uninstalling the apps.
For example, Check Point Research discovered that MSMQ will be automatically enabled during Exchange Server installations.
“CPR has found that when installing the official Microsoft Exchange Server, the setup wizard application enables the MSMQ service in the background if the user selects the option “Automatically install Windows Server roles and features required to install Exchange”, which is recommended by Microsoft”, the researchers said.
“The important point to remember is that if MSMQ is enabled on a server, the attacker could potentially exploit this vulnerability or any MSMQ vulnerability and take control of the server.”
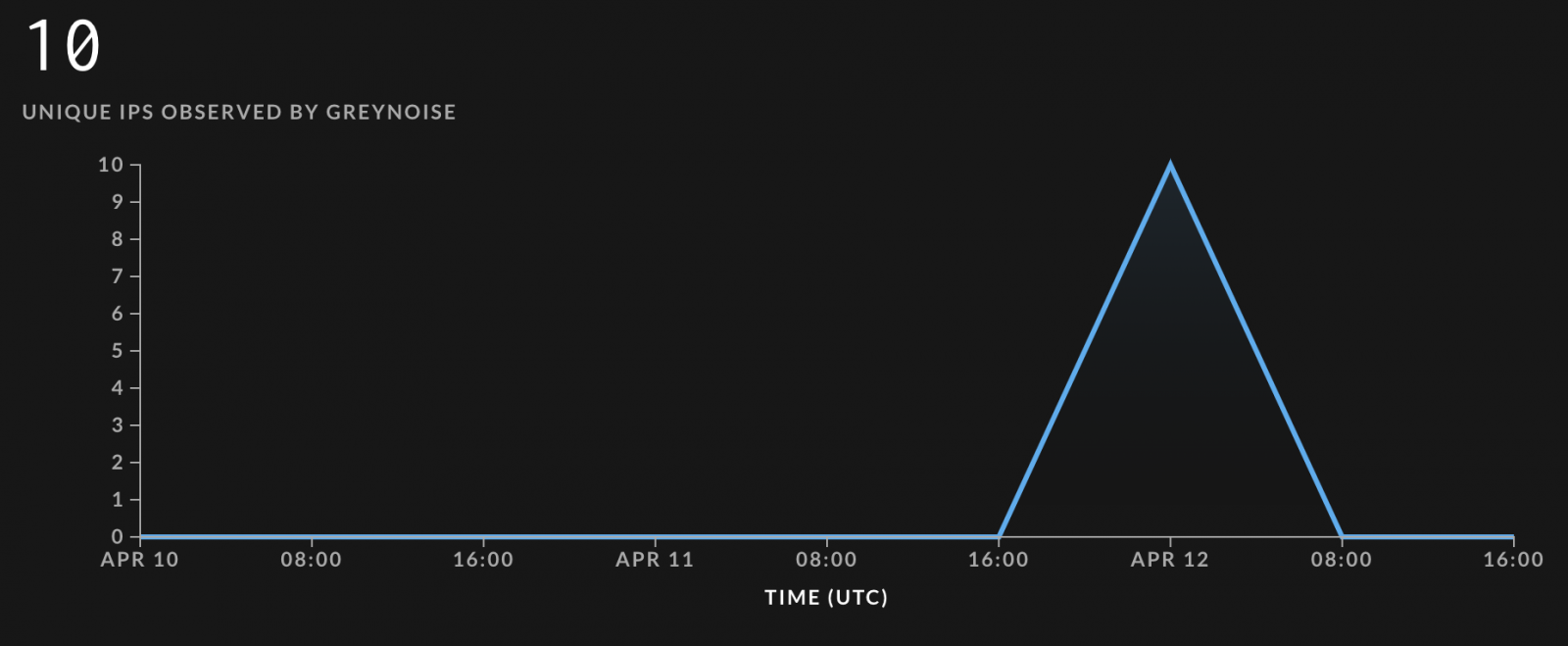
Since Tuesday, the cyberintelligence company GreyNoise has started tracking MSMQ login attemptsand it currently shows ten different IP addresses that have already started looking for servers exposed to the Internet.
While Microsoft has already fixed this bug and 96 other security flaws as part of the April patch on Tuesday, it also advised administrators who cannot immediately deploy the patch to disable the Windows MSMQ service (if possible) to remove the attack vector.
“You can check if a service named Message Queuing is running and if TCP port 1801 is listening on the machine”, Microsoft said.
Organizations that cannot immediately disable MSMQ or deploy Microsoft’s fix can also block 1801/TCP connections from untrusted sources using firewall rules.
[ad_2]
Source link