[ad_1]

Microsoft has shared guidance to help organizations verify whether hackers have targeted or compromised machines with the BlackLotus UEFI Starter Kit by exploiting the CVE-2022-21894 vulnerability.
Organizations and individuals can also use guidance from Microsoft to recover from an attack and prevent hackers using BlackLotus from achieving persistence and evading detection.
BlackLotus has been available since Last year on hacking forums, promoted as malware that evades antivirus detection, resists removal attempts, and can disable various security features (e.g. Defender, HVCI, BitLocker). The price for a license was $5,000, with rebuilds available for $200.
The malware’s capabilities were confirmed in early March by researchers from cybersecurity firm ESET, who noted that the malware worked exactly as advertised.
Location of signs of infection by BlackLotus
Malware for the Unified Extensible Firmware Interface (UEFI) is particularly difficult to detect because these threats run before the operating system, being able to deploy payloads early in the boot process to disable protection mechanisms. security.
Malware for the Unified Extensible Firmware Interface (UEFI) is particularly difficult to detect because this type of threat executes before the operating system boots, allowing it to deploy payloads early in the boot process. startup to disable security mechanisms.
By analyzing compromised devices with BlackLotus, the Microsoft Incident Response team has identified several points in the process of installing and running the malware that allow its detection.
The researchers note that defenders can look for the following artifacts to determine a BlackLotus UEFI bootkit infection:
- Recently created and locked bootloader files
- Presence of an intermediate directory used during the installation of BlackLotus in the EPS file system:/
- Modifying the Registry Key for Hypervisor Protected Code Integrity (HVCI)
- Network logs
- Boot configuration logs
Boot partition artifacts
Since BlackLotus needs to write malicious bootloader files to the EFI system partition, also known as ESP, it will lock them down to prevent them from being deleted or modified.
Recently modified and locked files in the ESP location, especially if they match BlackLotus bootloader known filenames “should be considered highly suspicious.” It is advisable to remove devices from the network and examine them for evidence of activity related to BlackLotus.
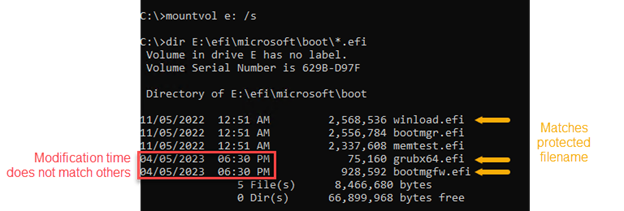
Microsoft recommends using the mounting flight command-line utility to mount the boot partition and check the creation date of files with mismatched creation times.
source: Microsoft
You can mount the ESP partition using the following command in a Command prompt with administrator privileges:
mountvol[available drive letter] /sFor example, if drive letter G: is free, you can run this command:
mountvol g: /sIf the modified time does not seem suspicious, threat hunters can try to calculate the hash of the bootloader file. On a compromised device, the output should be a file access error because BlackLotus locks them to prevent tampering.
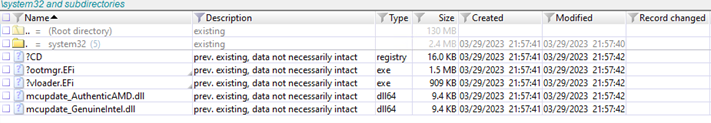
Another tell-tale of BlackLotus is the presence of the “/system32/” directory on the ESP, which is where the files needed to install the UEFI malware are stored.
Microsoft says successful installation of BlackLotus results in deletion of files inside”ESP:/system32/” but the directory remains. Forensic analysts can use it to search for deleted files.
source: Microsoft
Registry, logs and network indices
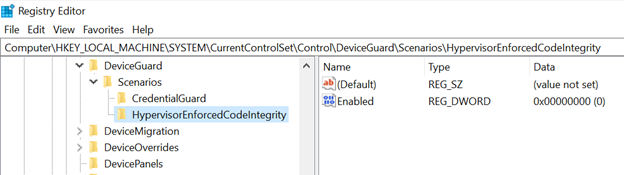
One of the features of BlackLotus is to disable Hypervisor Protected Code Integrity (HVCI), which allows it to load unsigned kernel code.
This is achieved by setting to 0 (zero) the Enabled value of the HVCI registry keylike in the picture below.
source: Microsoft
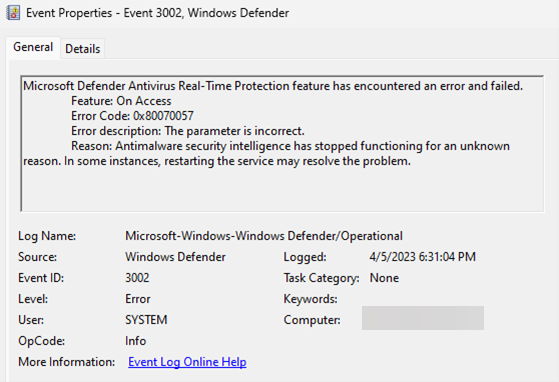
A second security feature that BlackLotus disables is Microsoft Defender Antivirus, the default security agent on the Windows operating system.
This action may leave traces in the Windows event logs in the form of an entry under the Microsoft-Windows-Windows Defender/Operational Register.
source:Microsoft
Disabling Defender may also generate Event ID 7023 in the System Event Log due to the unexpected termination of the service.
Microsoft investigators advise threat hunters to examine network logs for outbound connections from winlogon.exe on port 80, which may indicate that BlackLotus is trying to communicate with its command and control (C2) server.
“This is the result of BlackLotus injected HTTP download function connecting to C2 server or performing network configuration discovery” – Microsoft
Additional evidence of BlackLotus compromise may be present in boot configuration logs – Measured start logs, which provide details about the Windows startup process.
When the bootkit becomes active, two boot drivers become available, namely grubx64.efi And winload.efi. By comparing logs for each system reboot, analysts can find components that were added or removed each time the machine started.
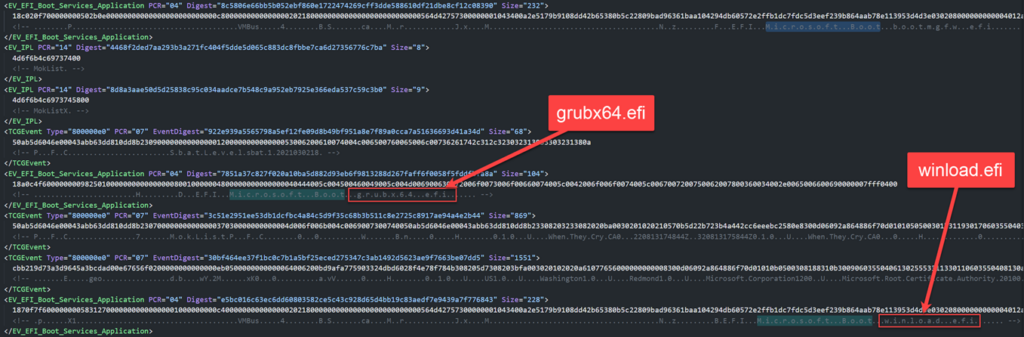
source: Microsoft
Microsoft warns that access to MeasuredBoot log files is possible using a forensic image or raw NTFS reader tool.
Data can be read after decoding and converting to XML or JSON file format. Microsoft provides a example scenario based on open-source TCGLogTools to analyze and extract logs
Below is an example of the BlackLotus drivers that the sample script showed on an infected machine:
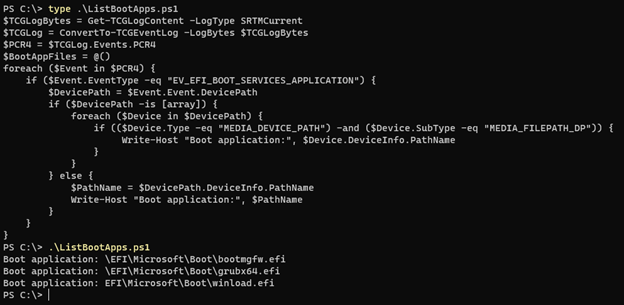
source: Microsoft
Prevent BlackLotus from being compromised
Cleaning up a machine after a BlackLotus infection requires removing it from the network and reinstalling it with a clean OS and EFI partition, or restoring from a clean backup with an EFI partition.
While post-infection artifacts are telling in determining the type of malware being used, defenders can prevent compromise by detecting an intrusion before the adversary can deploy the UEFI malware.
However, launching a UEFI bootkit requires privileged access to the target machine, remotely or physically, which means that a top-level threat and initial access vector precede persistent infection.
To ward off infection via BlackLotus or other malware exploiting CVE-2022-21894, Microsoft recommends that organizations practice the principle of least privilege and credential hygiene.
“Avoid the use of domain-wide administrator-level service accounts. Restricting local administrative privileges can help limit the installation of Remote Access Trojans (RATs) and other unwanted applications” -Microsoft
By implementing multiple layers of security controls, called defense-in-depth strategies, organizations can reduce the risk of an adversary gaining administrative access or privilege in the environment.
This can essentially stop a BlackLotus attack in its early stages before the threat actor can compromise a user’s or service account’s credentials to move laterally through the network and elevate their privileges.
[ad_2]
Source link
