[ad_1]

A serious privacy flaw named “acropalypse” has also been found to affect the Windows snipping tool, allowing users to partially grab content that has been edited from an image.
Last week, security researchers David Buchanan and Simon Aarons discovered that a bug in google pixel markup tool caused the original image data to be retained even if it was edited or cropped.
This flaw poses a significant privacy concern because if a user shares an image, such as a credit card with a redacted number or revealing photos with the face removed, it may be possible to partially recover the original photo.
To illustrate this bug, the researchers launched an online platform acropalypse screenshot recovery utility which would attempt to recover altered images created on Google Pixel.
Windows 11 Snipping Tool is also affected
Today, software engineer Chris Blume confirmed that the “acropalypse” privacy flaw also affects Windows 11’s Snipping Tool.
When opening a file in windows 11 snipping tool and overwriting an existing file, instead of truncating the unused data, it leaves the unused data behind allowing it to be recovered partially.
Vulnerability expert Will Dormann also confirmed the Windows 11 Snipping Tool flaw, and with Dormann’s help, BleepingComputer also confirmed the issue.
To test this, we opened an existing PNG file in Windows 11’s snipping tool, cropped it (can also edit or mark it), then saved the changes back to the original file. The original and cropped images are shown below.
Source: BleepingComputer
While the cropped image now contains much less data than the original, the file sizes for the original image file (office-screenshot-original.png) and the cropped image file (office-screenshot.png) are the same, as shown below.
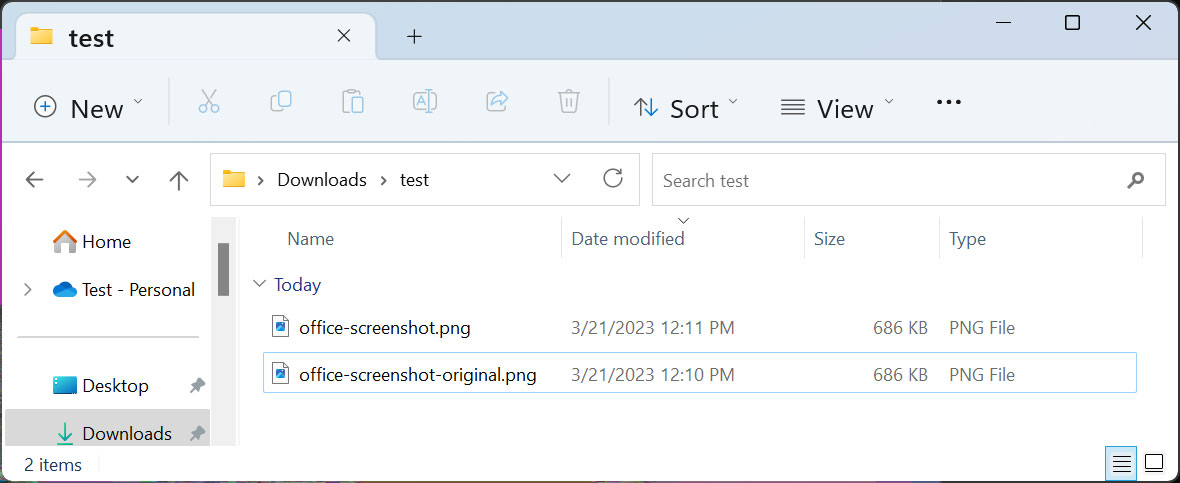
Source: BleepingComputer
THE PNG File Specification requires that a PNG image file always end with an ‘IEND’ data block, all data added after being ignored by image editors and viewers.
For example, here is the original screenshot I took from Microsoft’s site. As you can see, the file ends with an IEND and contains no data after it.
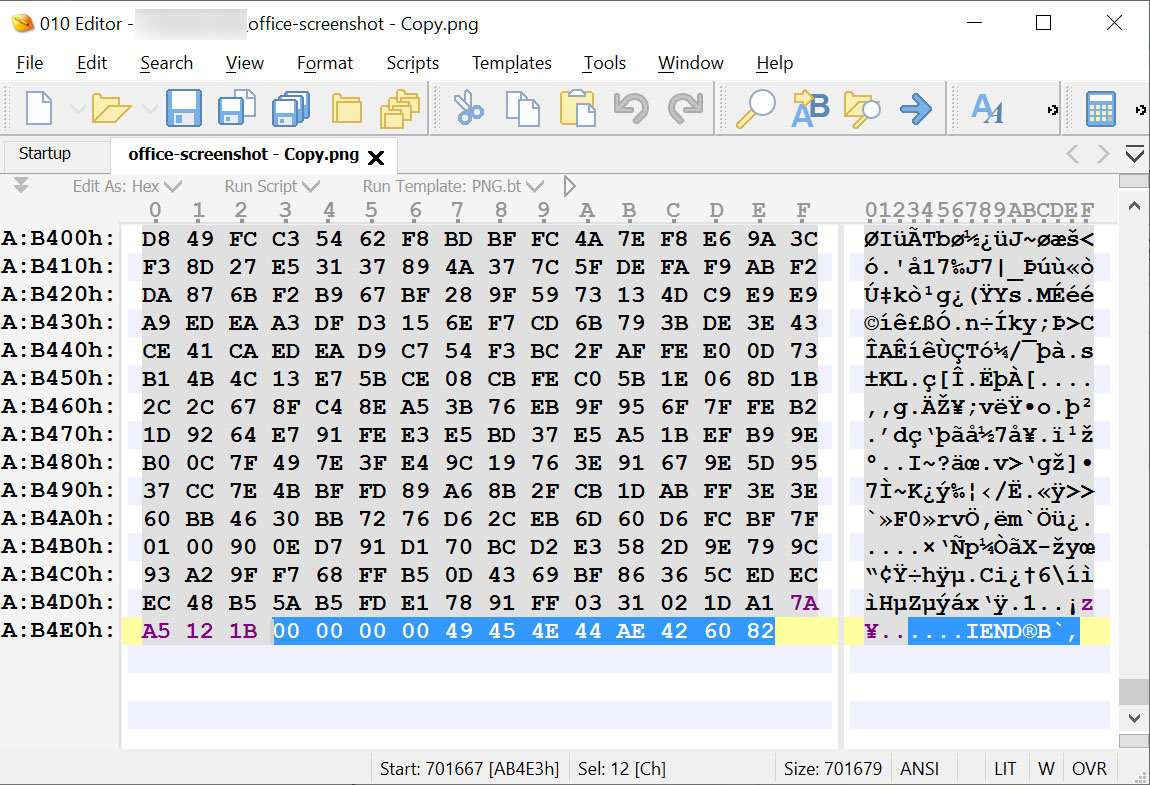
Source: BleepingComputer
However, using Windows 11’s snipping tool to overwrite the original image with the cropped version, the program did not properly truncate the unused data, and it remains after the IEND data block.
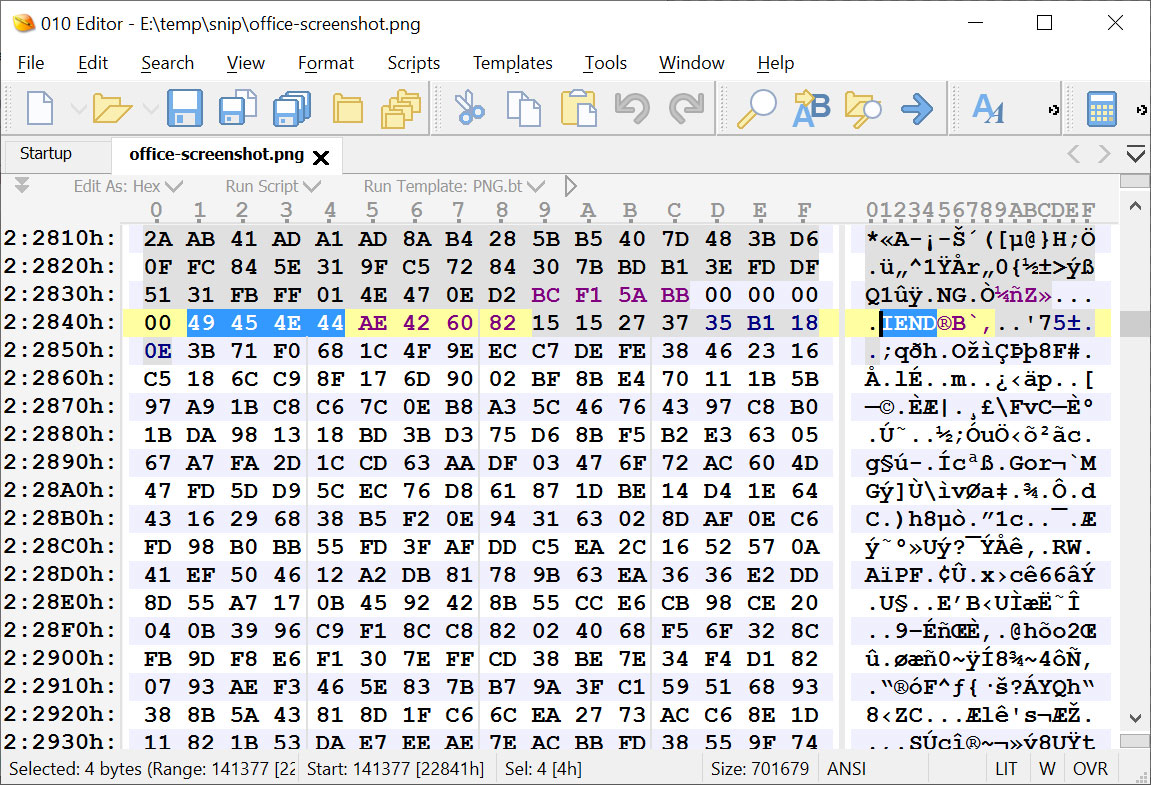
Source: BleepingComputer
Opening the file in an image viewer just shows the cropped image, because everything after the first IEND is ignored.
However, this untruncated data can be used to partially recreate the original image, potentially revealing sensitive parts.
While the researcher is online acropalypse screenshot recovery app does not currently work with Windows files, Buchanan has shared a Python script with BleepingComputer that can be used to recover Windows files.
Using this script, BleepingComputer managed to grab part of the image as shown below.

Source: BleepingComputer
It was not a full recovery of the original image, and you might be wondering why this is a privacy risk.
Imagine taking a screenshot of a sensitive spreadsheet, confidential documents, or even a nude photo, and deleting sensitive information or parts of the image.
Even if you can’t fully recover the original image, someone might recover sensitive information that you don’t want made public.
It should also be noted that not all PNG files, such as optimized PNGs, are affected by this flaw.
“Your original PNG was saved with a single zlib block (common for ‘optimized’ PNGs), but the actual screenshots are saved with multiple zlib blocks (which is what my exploit requires),” Buchanan explained to BleepingComputer.
BleepingComputer also found that if you open an untruncated PNG file in an image editor, such as Photoshop, and save it to another file, the unused data at the end will be deleted, making it more retrievable. .
Finally, Windows 11’s snipping tool also performs the same behavior with JPG files, leaving the data untruncated if overwritten. However, Buchanan told BleepingComputer that his exploit does not currently work on JPGs, but might be possible.
BleepingComputer contacted Microsoft about the flaw and whether it will be fixed, but a response was not immediately available.
[ad_2]
Source link