[ad_1]

Google’s Threat Analysis Group (TAG) monitors and disrupts Russian state-sponsored cyberattacks targeting Ukraine’s critical infrastructure in 2023.
Google reports that from January to March 2023, Ukraine received about 60% of phishing attacks from Russia, making it the biggest target.
In most cases, the campaign’s goals include intelligence gathering, operational disruptions and the leaking of sensitive data through Telegram channels dedicated to causing damage to information in Ukraine.
Threat groups active in Ukraine
Google’s TAG lists three Russian and Belarusian threat actors that had notable activity in the first quarter of the year against Ukrainian targets.
The first is Sandworm, followed by Google as “FrozenBarents”, which has focused its attacks on the energy sector across Europe since November 2022, with one case highlighted involving the Caspian Pipeline Consortium (CPC ).
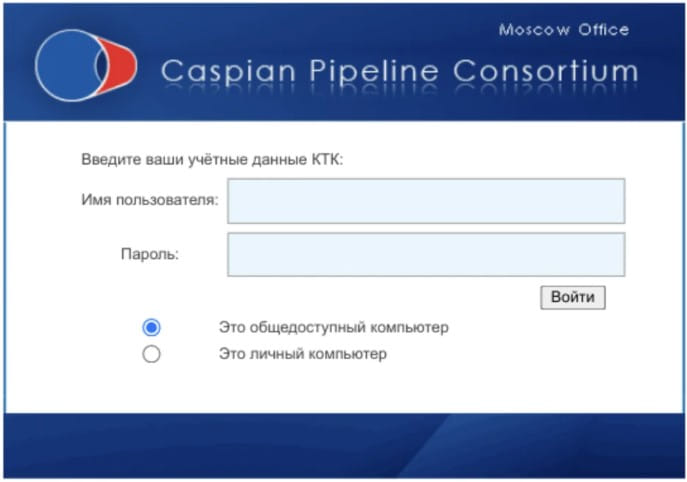
Sandworm has recently launched several phishing campaigns using spoofed “Ukroboronprom” websites against Ukrainian defense industry workers, users of the Ukr.net platform or even Ukrainian Telegram channels.

The threat group also creates several online personas to spread false information on YouTube and Telegram, often leaking parts of the data they steal through phishing or network intrusions.
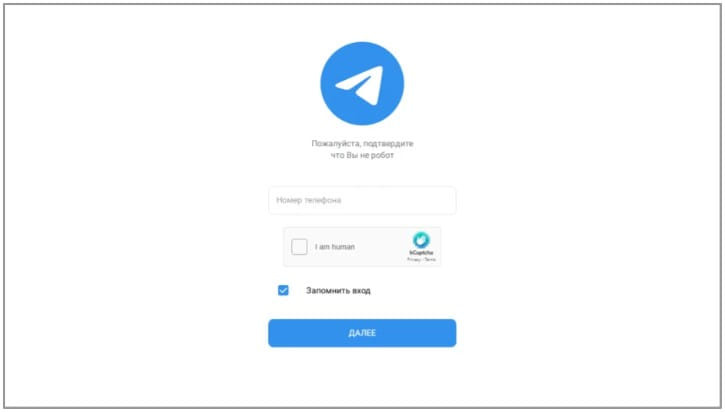
Another very active Russian threat actor is APT28, tracked by Google as “FrozenLake”.
Between February and March 2023, APT28 sent several large waves of phishing emails targeting Ukrainians. Hackers also used thoughtful cross-site scripting (XSS) on Ukrainian government websites to redirect visitors to phishing pages.

This week, a joint announcement from Britain’s NCSC, FBI, NSA and CISA warned that APT28 is hacking cisco routers to install custom malware.
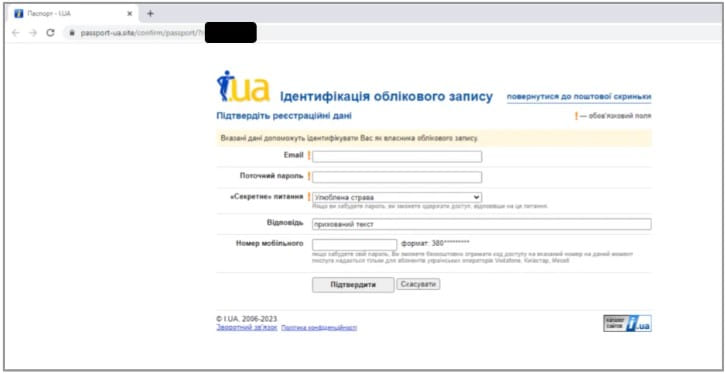
The third threat actor highlighted in Google’s report is “Pushcha”, which is believed to be based in Belarus, a country politically aligned with the Kremlin.
Pushcha recently launched campaigns targeting Ukrainian webmail providers such as “i.ua” and “meta.ua”, attempting to steal user credentials by creating fake sites.
State-sponsored disinformation
Google’s report also highlights instances of misinformation on its platforms, such as YouTube and Blogger.
“In the first quarter of 2023, TAG observed a coordinated OI campaign of Internet Research Agency (IRA)-affiliated actors creating content on Google products such as YouTube, including comments and upvotes on videos of each,” the report read. Google TAG report.
The IRA (Glavset) is a Russian company linked to the owner of the Wagner Group, Y. Prigozhin, which engages in online propaganda and influence operations on behalf of Russian political interests.
Google reports that it has observed and blocked IRA-linked accounts creating content on YouTube Shorts to promote specific “news-like” narratives about the war in Ukraine to Russian audiences.
All websites linked to the mentioned campaigns have been added to Google’s “Safe Browsing” block list, while targeted Gmail and Workspace users have received alerts informing them of the malicious communications.
[ad_2]
Source link
