[ad_1]

A new phishing campaign is targeting organizations in Eastern European countries with Remcos RAT malware using an old Windows User Account Control bypass discovered over two years ago.
The use of fake trusted directories to bypass Windows User Account Control stands out in the attack as it has been known since 2020, but remains effective today.
Remcos’ latest campaign was observed and analyzed by SentinelOne researchers, who documented their findings in a report released today.
It starts with a fake invoice
Phishing campaign emails are sent from top-level domains that match the recipient’s country and are usually disguised as invoices, tender documents, and other financial documents.
The emails don’t contain much text other than what’s needed to draw the recipient’s attention to the attachment, a tar.lz archive containing the DBatLoader executable.
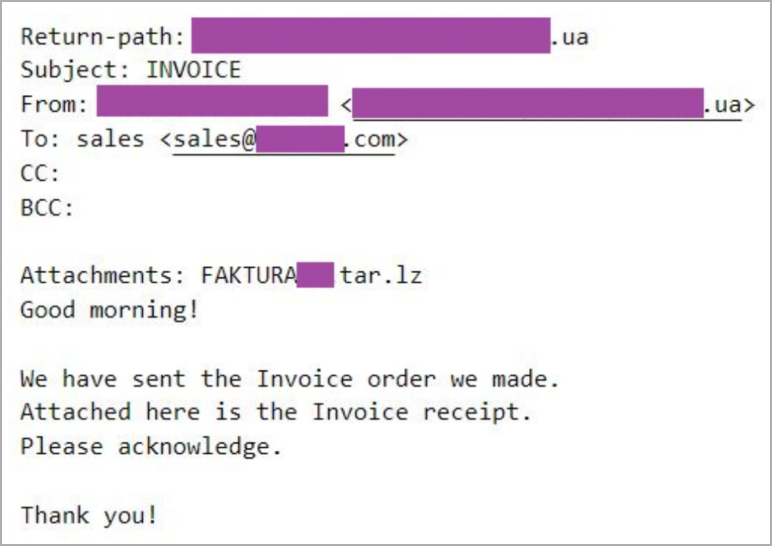
Such an unusual choice of file format reduces the chances of victims successfully opening the attachment, but also helps to evade detection from antivirus software and email security tools.
The malware loader’s first stage payload is disguised as a Microsoft Office, LibreOffice or PDF document using dual extensions and application icons to trick the victim into opening it.
When launching the malware loader, a second stage payload is fetched from a public cloud service, such as Microsoft OneDrive or Google Drive.
Sentinel One reports that in one case, the cloud service was abused for hosting DBatLoader for over a month, although it is unclear whether the threat actors used their own account or a compromised account with a clean history.
Abuse of fake “trusted” records
Before loading Remcos RAT, DBatLoader creates and runs a Windows batch script to abuse a Windows UAC workaround documented in 2020.
The method, first demonstrated on Windows 10 by security researcher Daniel Gebert, involves using a combination of DLL hijacking and fake trusted directories to bypass UAC and execute malicious code without prompting the user.
Windows UAC is a protection mechanism introduced by Microsoft in Windows Vista, asking users to confirm the execution of high-risk applications.
Some folders, such as C:\Windows\System32\, are trusted by Windows, allowing executables to auto-elevate without displaying a UAC prompt.
A fake directory is a imitation directory with a space at the end. For example, “C:\Windows\System32” is a legitimate folder and is considered a trusted location in Windows. A dummy directory would look like “C:\Windows\System32”, with an extra space after C:\Windows\.
The problem is that some Windows programs, like File Explorer, treat “C:\Windows” and “C:\Windows” as the same folder, thus tricking the operating system into thinking that C:\Windows\System32 is a trusted folder and should auto-elevate its files without a UAC prompt.
The script used by DBatLoader, in this case, creates fake trusted directories in the same way, creating a “C:\Windows\System32” folder and copying legitimate executables (“easinvoker.exe”) and malicious DLLs (“netutils.dll”) to this one.
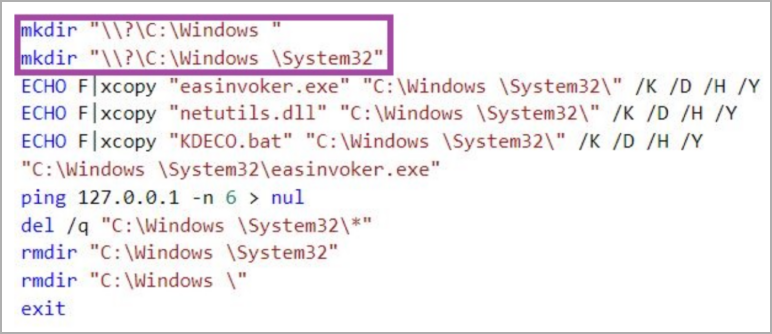
“easinvoker.exe is susceptible to DLL hijacking allowing malicious netutils.dll to execute in its context,” explains Sentinel 1
“easinvoker.exe is a self-elevating executable, which means that Windows automatically elevates this process without issuing a UAC prompt if it is in a trusted directory – the fake directory %SystemRoot%\System32 ensures that this criteria is met completed.”
The malware loader adds the malicious script (“KDECO.bat”) hiding in the DLL to Microsoft’s Defender exclusion list, then establishes persistence for Remcos by creating a new registry key.
Finally, Remcos is run by process injection, configured with keylogging and screen capture capabilities.
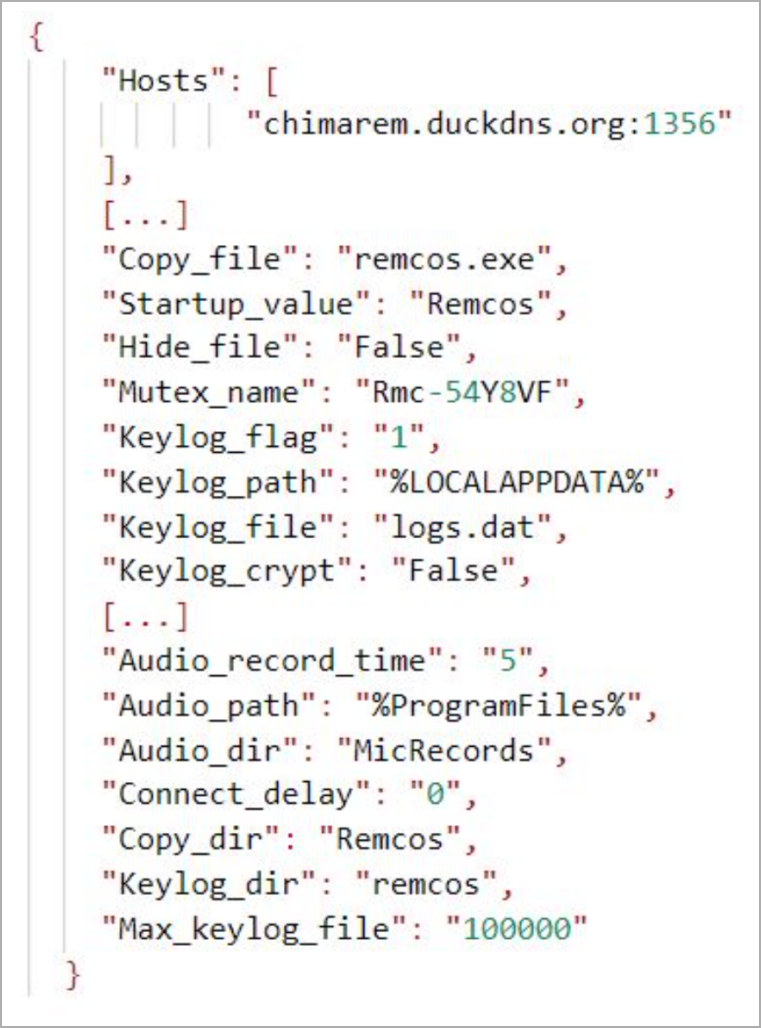
Sentinel One suggests system administrators set Windows UAC to “Always Notify”, although this may be too annoying and noisy.
Administrators should also watch for suspicious file creations or process executions in trusted file system paths with trailing spaces, especially folders containing the string “\Windows”.
[ad_2]
Source link
