[ad_1]

A suspected North Korean hacking group is targeting security researchers and media organizations in the United States and Europe with fake job postings that lead to the deployment of three new custom malware families.
Attackers use social engineering to convince their targets to engage on WhatsApp, where they drop the “PlankWalk” malware payload, a C++ backdoor that helps them gain a foothold in the company’s corporate environment. target.
According Beggarfollowing the particular campaign since June 2022, the observed activity overlaps”Operation Dream Jobattributed to the North Korean cluster known as the “Lazarus Group”.
However, Mandiant observed enough differences in the tools, infrastructure, and TTPs (tactics, techniques, and procedures) used to attribute this campaign to a separate group they track as “UNC2970.”
Additionally, the attackers use previously unknown malware named “TOUCHMOVE”, “SIDESHOW” and “TOUCHSHIFT”, which have not been assigned to any known threat group.
Mandiant says the particular group has previously targeted tech companies, media groups and defense industry entities. Her latest campaign shows that she has evolved her targeting range and adapted her abilities.
Phishing to get a foothold
Hackers begin their attack by approaching targets on LinkedIn, posing as recruiters. Eventually, they moved on to WhatsApp to continue the “recruitment” process, sharing a Word document embedded with malicious macros.
Mandiant says that in some cases, these Word documents are styled to match the job descriptions they promote to targets. For example, one of the decoys shared by Mandiant impersonates The New York Times, as seen below.
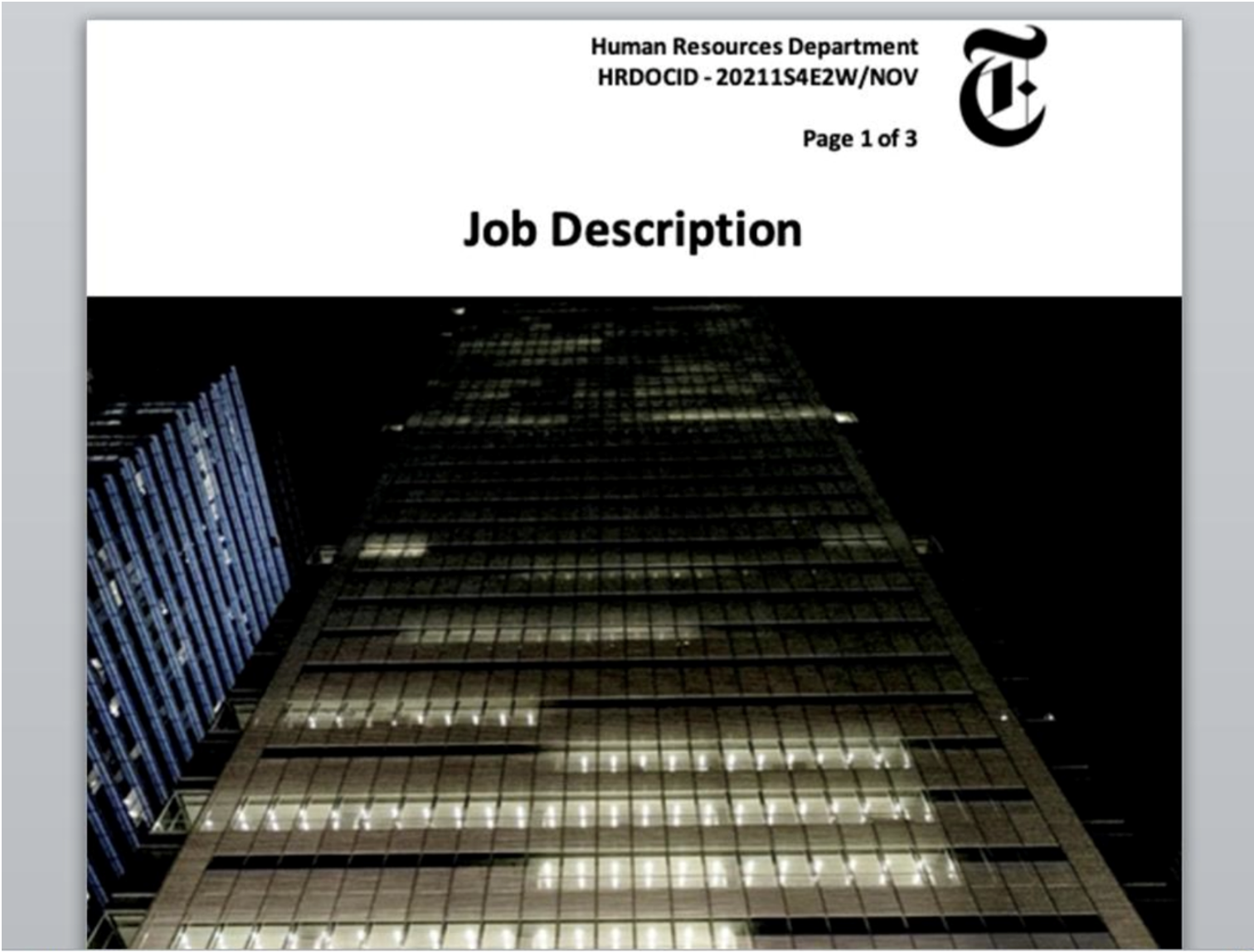
Word document macros perform remote template injection to retrieve a trojanized version of TightVNC from compromised WordPress sites that serve as the attacker’s command-and-control servers.
Mandiant tracks this custom version of TightVNC as “LidShift”. At runtime, it uses reflective DLL injection to load an encrypted DLL (trojanized Notepad++ plugin) into system memory.
The loaded file is a malware downloader named “LidShot”, which performs system enumeration and deploys the final foothold payload to the hacked device, “PlankWalk”.
Disguising yourself as Windows files
During the post-exploitation phase, North Korean hackers use a new custom malware dropper named “TouchShift”, which disguises itself as a legitimate Windows binary (mscoree.dll or netplwix.dll).
TouchShift then loads another screenshot utility called “TouchShot”, a keylogger named “TouchKey”, a tunneler named “HookShot”, a new loader named “TouchMove”, and a new backdoor named “SideShow”.
Most interesting of the bunch is the new SideShow custom backdoor, which supports a total of 49 commands. These commands allow an attacker to execute arbitrary code on the compromised device, modify the registry, manipulate firewall settings, add new scheduled tasks, and run additional payloads.
In some cases where targeted organizations were not using VPN, threat actors were observed abusing Microsoft Intune to deploy “CloudBurst” malware using PowerShell scripts.
This tool also disguises itself as a legitimate Windows file, more specifically, “mscoree.dll”, and its role is to perform system enumeration.
Disabling EDR tools through day zero
A second gear released by Mandiant today focuses on the “bring your own vulnerable driver” (BYOVD) tactic followed by UNC2970 in the latest campaign.
After reviewing logs from compromised systems, Mandiant analysts found suspicious drivers and a strange DLL file (“_SB_SMBUS_SDK.dll”).
Upon further investigation, researchers discovered that these files were created by another file named “Share.DAT”, a memory dropper tracked as “LightShift”.
The dropper loads an obfuscated payload called “LightShow”, which exploits the vulnerable driver to perform arbitrary read and write operations on kernel memory.
The role of the payload is to patch kernel routines used by EDR (Endpoint Detection and Response) software, helping intruders evade detection.
Notably, the driver used in this campaign was an ASUS driver (“Driver7.sys”) which was not known to be vulnerable at the time of Mandiant’s discovery, so North Korean hackers were exploiting a zero-day flaw. .
Beggar reported the issue to ASUS in October 2022, the vulnerability was given the identifier CVE-2022-42455, and the vendor patched it via an update released seven days later.
North Korean hackers previously targeted security researchers involved in developing vulnerabilities and exploits by creating fake online social media personas who posed as vulnerability researchers.
These people would then contact other security researchers about possible collaboration in researching the vulnerabilities.
After contacting a researcher, the hackers sent malicious Visual Studio projects And MHTML files that exploited Internet Explorer zero-day.
Both of these decoys were used to deploy malware to the devices of targeted researchers in order to gain remote access to computers.
[ad_2]
Source link
