[ad_1]

A new Android malware campaign spreading the latest version of GravityRAT has been running since August 2022, infecting mobile devices with a trojanized chat app named “BingeChat”, which attempts to steal data from victims’ devices.
According ESET Researcher Lukas Stefankowho analyzed a sample after receiving advice from MalwareHunterTeamOne of the notable new additions spotted in the latest version of GravityRAT is stealing WhatsApp backup files.
WhatsApp backups are created to help users transfer their message history, media files and data to new devices, so that they may contain sensitive data such as text, videos, photos, documents, etc., all in unencrypted form.
GravityRAT has been active since at least 2015 but started targeting Android for the first time in 2020. Its operators, “SpaceCobra”, use the spyware exclusively and in narrow targeting operations.
Current Android Campaign
The spyware is marketed as “BingeChat”, supposedly an end-to-end encrypted chat application with a simple interface but advanced features.
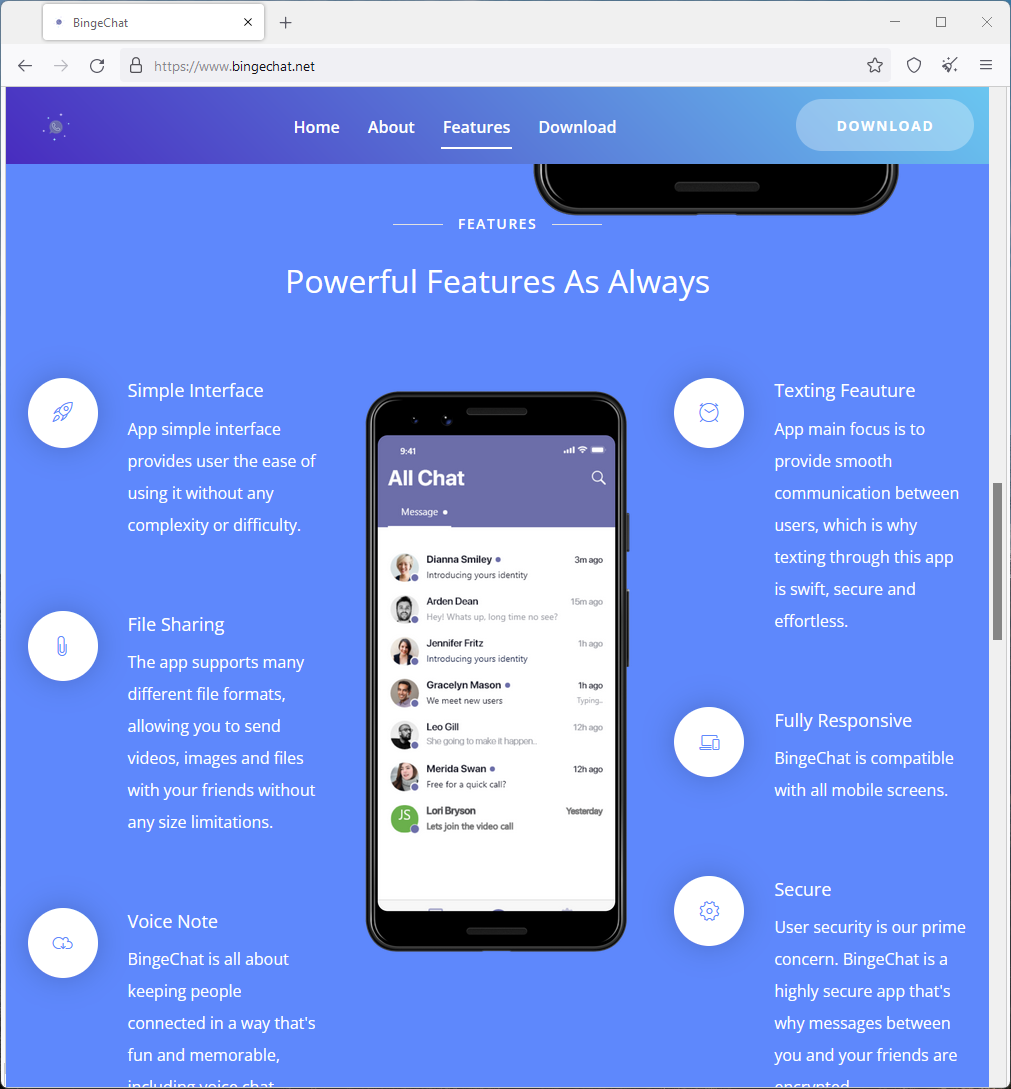
ESET says the app is delivered via “bingechat[.]net” and possibly other domains or distribution channels, but the download is invitation-based, which requires visitors to enter valid credentials or create a new account.
While the registrations are currently closed, this method only allows them to distribute the rogue apps to the targeted people. It is also more difficult for researchers to access a copy for analysis.
Promoting malicious Android APKs to targets is a tactic GravityRAT Operators re-employed in 2021using a chat application called “SoSafe” and, before that, another called “Travel Mate Pro”.
Stefanko discovered that the app is a Trojan version of OMEMO IMa legitimate open-source instant messaging application for Android.
Digging further, the ESET analyst discovered that SpaceCobra used OMEMO IM as the basis for another fake application named “Chatico”, which was distributed to targets in the summer of 2022 via the now offline “chatico. co”.[.]United Kingdom.”
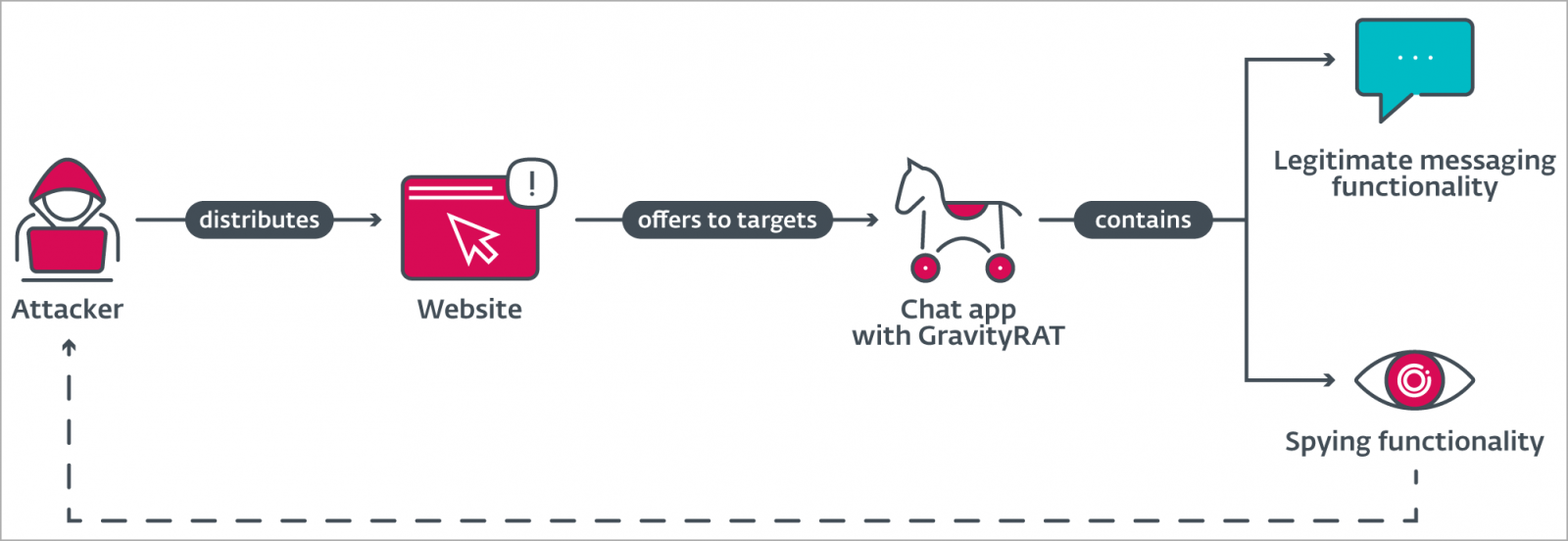
GravityRAT Abilities
BingeChat asks for risky permissions when installed on the target’s device, including access to contacts, location, phone, SMS, storage, call logs, camera, and microphone.
These are standard permissions for instant messaging apps, so they are unlikely to arouse suspicion or appear abnormal to the victim.
Before the user registers in BingeChat, the app sends call logs, contact lists, SMS messages, device location and basic device information to the server. command and control (C2) of the threat actor.
Also, media and document files jpg, jpeg, log, png, png, jpg, jpeg, txt, pdf, xml, doc, xls, xlsx, ppt, pptx, docx, opus, crypt14, crypt12, crypt13, crypt18 and crypt32 types, are also stolen.
The encrypted file extensions correspond to the previously mentioned WhatsApp Messenger backups.
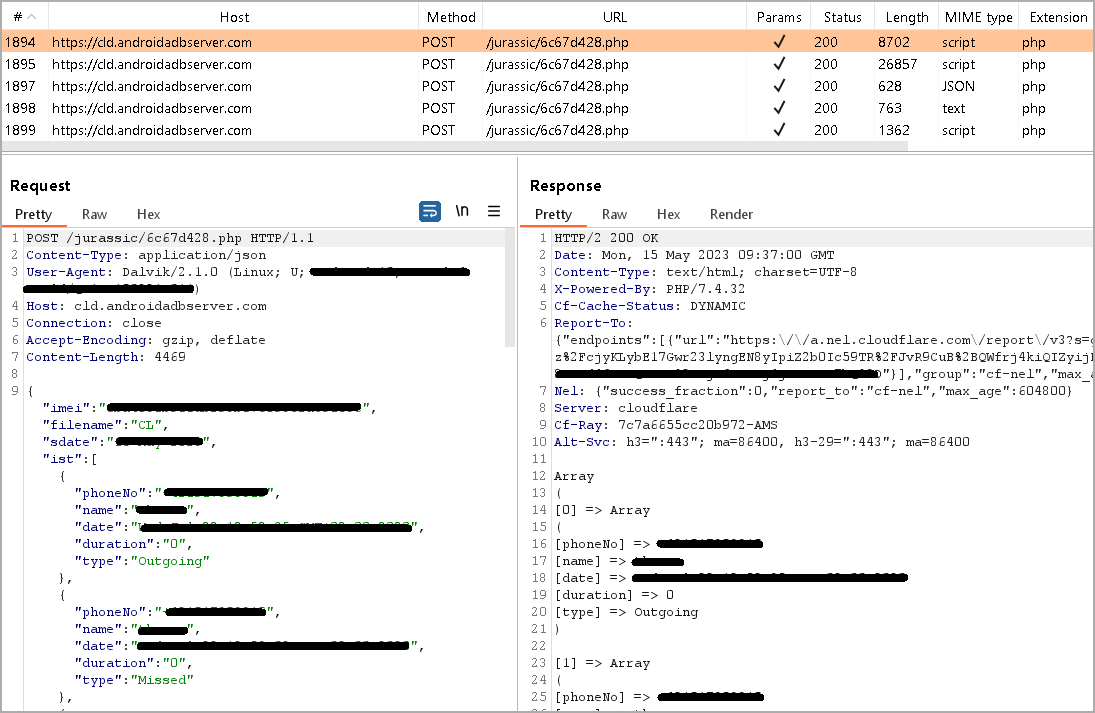
Another notable new feature of GravityRAT is its ability to receive three commands from the C2, namely “delete all files” (of a specified extension), “delete all contacts”, and “delete all call logs”.
While SpaceCobra’s campaigns are highly targeted and generally focus on India, all Android users should avoid downloading APKs outside of Google Play and be careful with risky permission requests during installation. of an app.
[ad_2]
Source link
