[ad_1]

The Russian hacking group known as ‘Nodaria’ (UAC-0056) is using new information-stealing malware called ‘Graphiron’ to steal data from Ukrainian organizations.
The Go-based malware can harvest a wide range of information, including account credentials, system, and application data. The malware also captures screenshots and exfiltrates files from compromised machines.
Symantec’s Threat Research team discovered that Nodaria used Graphiron in attacks from at least October 2022 until mid-January 2023.
Steal sensitive information
Graphiron consists of a downloader and a secondary information-stealing payload.
Once launched, the downloader will check for various security software and malware scanners, and if none are detected, will download the information-stealing component.
Some of the processes the downloader checks include BurpSuite, Charles, Fiddler, rpcapd, smsniff, Wireshark, x96dbg, ollydbg, and idag.
The malware uses names such as OfficeTemplate.exe and MicrosoftOfficeDashboard.exe to impersonate a Microsoft Office component on the hacked system.
His abilities include the following:
- Read MachineGuid
- Get the IP address from https://checkip.amazonaws.com
- Retrieve hostname, system information and user information
- Steal data from Firefox and Thunderbird
- Steal MobaXTerm’s private keys.
- Stealing SSH Known Hosts
- Stealing data from PuTTY
- Steal stored passwords
- Take screenshots
- Create a directory
- List a directory
- Run a shell command
- Steal an arbitrary file
The malware uses the following PowerShell code to steal passwords from Windows Vault, the system’s built-in password manager, where saved credentials are stored in AES-256 encrypted form.
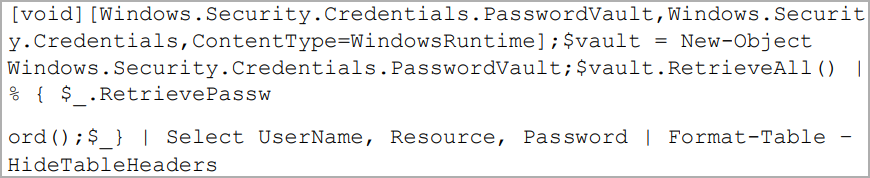
Graphiron uses AES encryption with hard-coded keys to communicate with the C2 server via port 443, a remarkable similarity to older Nodaria tools like GraphSteal and GrimPlant.
Nodaria targets Ukraine
Nodaria is the same threat actor that deployed fake ransomware named ‘WhisperGate‘ on Ukrainian networks in January 2022, carrying out destructive data erasure attacks.
Typically, Russian hackers deliver their payloads to targets via spear-phishing emails, with the ongoing war providing plenty of opportunities for effective bait.
Graphiron is the latest addition to Nodaria’s arsenal, combining the functionality of the group’s older custom tools into a single payload while providing obfuscation.
This is a sign that Nodaria will continue to target Ukrainian organizations, attempting to collect valuable information from high-profile targets.
[ad_2]
Source link
