[ad_1]

Ransomware is a type of malicious software that restricts access to computer systems and the data stored on them until a ransom payment is made. In recent cyberattacks, ransomware functionality has expanded to include data exfiltration, distributed denial of service (DDoS) attacks, and anti-analysis techniques.
Additionally, the Ransomware as a Service (RaaS) model has been widely adopted by the threat actors behind these attacks. Ransomware as a service is a business model that helps ransomware developers and operators sell or rent ransomware capabilities to threat actors.
Common Ransomware Behaviors
- Based on the attack pattern, ransomware can encrypt critical data without interfering with other computer system functions. This type of malware can deny access to an entire web application or specific files on the computer system. This may prevent companies from accessing or using their data or performing operational functions. Examples include Lockbit 3.0, Black Basta and Pandora ransomware.
- Typical behavior of some ransomware is their ability to prevent victims from accessing essential device functions. Ransomware victims are usually prevented from interacting further with their operating system, leaving them only access to facilitate the payment of the ransom. Examples include Petya, GoldenEye, and KeRanger ransomware.
- Ransomware uses the dual extortion tactics of encrypting files and exfiltrating data with the aim of publishing them if the ransom is not paid.
- After successful ransomware attacks, threat actors usually leave ransom messages demanding ransom payments in cryptocurrencies like Bitcoin and Monero. This ensures that the anonymity of the attacker is preserved.
Ransomware Attack Vector
Ransomware is spread using different techniques, but the most common way to infect computer systems is through user-initiated actions. These actions include clicking on a malicious link in phishing emails or visiting a compromised website. Threat actors also exploit system misconfigurations such as insecure remote desktop connections available over the internet and weak password/access management to launch ransomware attacks.
There are other forms of infections that exploit malicious advertisements and unwanted downloads. These forms of infection are distributed without the need for the user to interact with the malware.
Impact of ransomware attacks on organizations
Ransomware attacks can have significant impacts on organizations and their ability to perform critical tasks in different ways. Some ways this can impact organizations are highlighted below:
- Exposure of sensitive data: Most ransomware operators use data exfiltration techniques to force organizations to make ransom payments after carrying out a successful attack. They usually threaten to release the stolen data on the dark web if the ransom is not paid.
- Prolonged average recovery time: Ransomware attacks typically cause organizations to lose access to critical systems and applications for an extended period of time. Most businesses experience downtime that lasts for days, which is a significant disruption to operations and productivity.
- Damage to brand reputation: Most organizations experience damage to their reputation and brand value due to cybersecurity-related attacks, including ransomware.
- Financial loss: The ransom paid by organizations that have suffered major ransomware attacks is usually expensive. These organizations may also bear an additional financial burden from regulatory agencies after a security incident.
How Wazuh protects endpoints from ransomware attacks
Wazuh is a security solution that provides unified SIEM and XDR protection across multiple platforms. The article Wazuh – The free and open source XDR platform highlights how organizations can leverage the open nature of Wazuh to use it freely and customize it to suit their security needs. It protects workloads in virtualized, on-premises, cloud-based, and containerized environments.
Wazuh offers several features that organizations can implement to detect and defend against security threats. This section highlights several Wazuh features that provide protection against ransomware attacks.
Vulnerability detection
Vulnerability scanning is a process of identifying weaknesses in the operating system and software installed on a device. In a blog post recently published by Wazuh on Detection of Lockbit 3.0 ransomwarenote that one of the ransomware attack vectors exploits unpatched server vulnerabilities.
The Wazuh Vulnerability detector The module performs software audits to detect endpoint vulnerabilities. Wazuh creates a global vulnerability database from publicly available CVE repositories. Next, Wazuh correlates application inventory data collected from endpoints with the vulnerability database to detect vulnerable components.
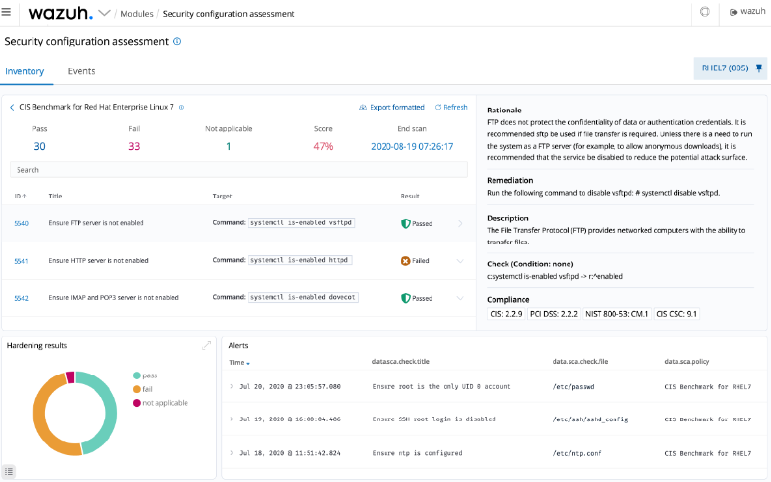
Security Configuration Assessment (SCA)
Security configuration assessment is a process used to identify system misconfigurations that could expose a system to attack. This includes periodic configuration checks and implementing security best practices by adopting standards such as CIS (Center of Internet Security).
Wazuh Security Configuration Assessment The module provides the ability to perform regular scans on endpoints to ensure they are compliant with security best practices. These scans evaluate endpoint configuration using policy files that contain rules to test against the actual host configuration.
For example, the Wazuh SCA module checks configurations related to password usage and unwanted applications and services. It also audits the TCP/IP stack configuration on a monitored terminal. Our recent blog post on How to Perform a WordPress Security Assessment with Wazuh shows how to implement the Wazuh SCA module to compare WordPress configurations.
File integrity monitoring
File Integrity Monitoring (FIM) is the process of monitoring an endpoint file system for add, delete, and modify activities. It is important to monitor critical files and directories on a client workstation to ensure that the changes made are legitimate.
The Wazuh FIM The module detects changes to monitored files and directories and then generates an alert on the Wazuh dashboard. Changes are detected when there is a deviation in the stored cryptographic checksum and other attributes of monitored files and directories on the endpoint. File and directory monitoring is performed periodically or in near real time.
As demonstrated in this blog post, the Wazuh FIM module can be used to detect the presence of ransomware on an endpoint. Most ransomware attacks trigger their execution by transferring malicious files to specific directories, and the Wazuh FIM module can detect such activity.
Wazuh can be integrated with other security solutions like VirusTotal and YARA to scan files on endpoints and check whether they are harmless or malicious. The Wazuh active response module handles removal of detected ransomware files.
Figure 2 below shows an example of Wazuh integration with YARA to detect Lockbit 3.0 ransomware. The active response module deleted the ransomware file after it was detected.
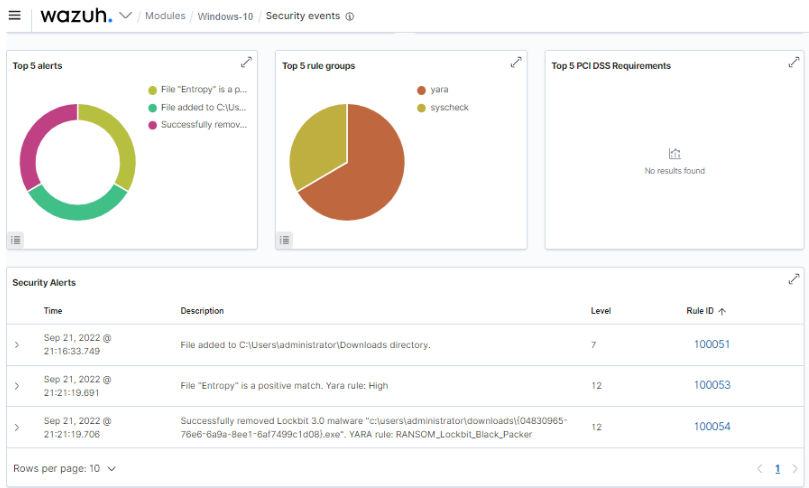
Detection with Wazuh
The initial phase of ransomware attacks involves the malware performing several actions on the infected endpoint.
These actions may include removing Volume Shadow Service, disabling Anti-Malware Service, clearing Windows Event Viewer logs, creating ransomware notes in multiple directories, and modifying the desktop background.
These behaviors can be captured by out-of-the-box Wazuh rules and decoders and alerted on the Wazuh dashboard in near real time. Custom detection rules can also be configured and mapped to their appropriate MITER ATT&CK tactics and techniques to detect these events.
Conclusion
Due to the ever-changing dynamics of ransomware attacks, organizations need to implement adequate security measures. The concept of RaaS has made it easier and more lucrative for threat actors to target organizations with ransomware. Organizations can effectively detect ransomware attacks by leveraging Wazuh’s various capabilities as discussed above.
Wazuh is a free and open source SIEM and XDR solution with over 10 million annual downloads and an ever-growing community. Wazuh integrates well with several third-party solutions and technologies.
For more information, see the Wazuh blog posts and Documentation. To deploy Wazuh and explore the different features it offers, see the Quick Installation Guide and Cloud Wazuh options.
Sponsored and written by Wazuh
[ad_2]
Source link
