[ad_1]

Newer versions of the Prilex point-of-sale malware can block secure, NFC-enabled contactless credit card transactions, forcing consumers to insert credit cards which are then stolen by the malware.
On a payment terminal, contactless transactions use NFC (Near Field Communication) chips embedded in credit cards and mobile devices to make proximity payments via credit cards, smartphones or even connected watches.
They are very convenient and their popularity has exploded since the COVID-19 pandemic, with over $34.55 billion in contactless transactions registered in 2021.
However, the use of NFC chips in credit cards has made it harder for point-of-sale (PoS) malware to steal credit card information, leading threat actors to develop new methods to steal your payment information.
Kaspersky, closely tracking the Prilex PoS malware, reports seeing at least three new variants in the wild, with version numbers 06.03.8070, 06.03.8072 and 06.03.8080, first released in November 2022.
These new variants introduce a new feature that prevents payment terminals from accepting contactless transactions, requiring customers to insert their cards.
Additionally, in September 2022, Kaspersky reported that Prilex added EMV cryptogram generation to evade transaction fraud detection and to perform “ghost transactions” even when the card is protected by CHIP and PIN technology.
Block and Steal
When the new Prilex feature is activated, it blocks contactless transactions and displays a “Contactless error, insert your card” error on the payment terminal.
This forces the victim to complete the transaction by inserting a credit card, which makes it easier to enter the card information through the payment terminal.

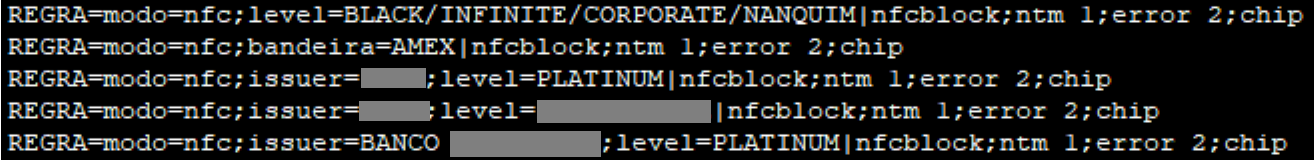
The malware uses a rule-based file to determine whether to block a transaction based on whether or not it detects NFC usage.
Prilex operators block NFC transactions because these generate a unique ID or card number that is only valid for a single transaction, so if this data is stolen, it would not be useful for scammers.
Once the credit card data is captured, Prilex operators use techniques seen in previous versions, such as cryptogram manipulation and “GHOST transaction” attacks.
Another cool new feature first seen on the latest Prilex variants is the ability to filter out unwanted cards and only capture data from specific vendors and tiers.
“These [filtering] rules can block NFC and capture card data only if the card is Black/Infinite, Corporate or another level with a high transaction limit, which is much more attractive than standard credit cards with a low balance/limit”, explains Kaspersky in the report.
Beneficiaries have limited means to protect themselves against PoS malware like Prilex, as there is no way to know if a payment terminal might be infected.
Standard security measures include avoiding paying on terminals with visible signs of tampering, avoiding using public WiFi to access financial accounts without a VPN, or not validating transaction details before and after. its completion.
Additionally, it is essential to regularly monitor financial statements to identify any potentially fraudulent transactions or charges that should be reported to the card issuer immediately.
[ad_2]
Source link
