[ad_1]

Analysis of nearly 20 million information-stealing malware logs sold on the dark web and Telegram channels revealed that they have achieved significant infiltration in business environments.
Information stealers are malicious software that steal data stored in applications such as web browsers, email clients, instant messengers, cryptocurrency wallets, FTP clients, and game services. The stolen information is collected in archives called “logs”, which are then uploaded to the threat actor for use in attacks or sold in cybercrime marketplaces.
The most prominent infostealer families are Redline, Raccoon, Titan, Aurora and Vidar, offered to cybercriminals on a subscription model, allowing them to run malware campaigns that steal data from infected devices.
While info thieves mainly target careless internet users who download software, such as cracks, warez, game cheats and fake software from dubious sources, they have also been found to have a massive impact on corporate environments.
This is because employees use personal devices for work or access personal data from work computers, leading to many infections of information thieves who steal work credentials and authentication cookies.
Specifically, as cybersecurity firm Flare explains in a new report shared with BleepingComputer, there are approximately 375,000 logs containing access to line-of-business applications such as Salesforce, Hubspot, Quickbooks, AWS, GCP, Okta, and DocuSign.
Specifically, Flare found the following in the flight logs reviewed:
- 179,000 AWS console credentials
- 2,300 Google Cloud IDs
- 64,500 DocuSign credentials
- 15,500 QuickBooks credentials
- 23,000 Salesforce IDs
- 66,000 CRM IDs
In addition to the above, there are approximately 48,000 logs that include access to “okta.com”, an enterprise-grade identity management service used by organizations for cloud and on-premises user authentication.
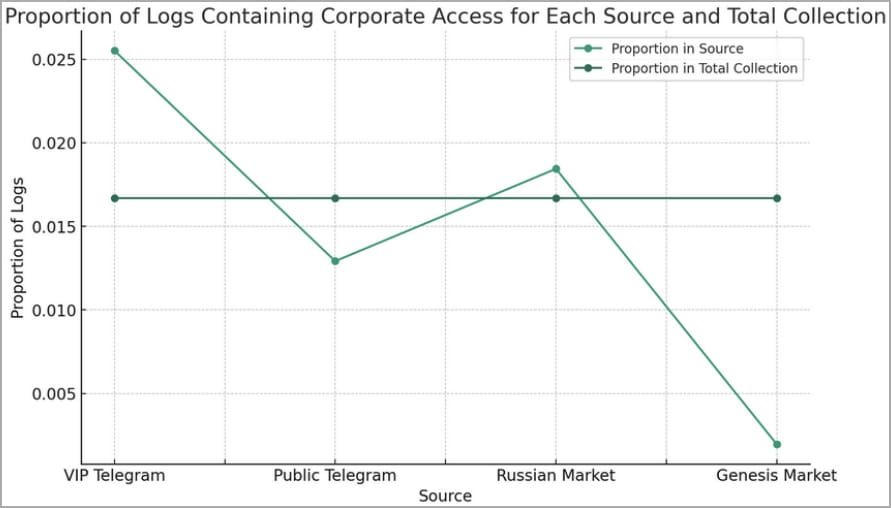
Most of these newspapers (74%) were published on Telegram channels, while 25% were seen in Russian-speaking markets, such as the “Russian market”.
“Logs containing corporate access were overrepresented on the Russian Market and VIP Telegram channels, indicating that the methods used by attackers to harvest logs may, accidentally or intentionally, further target businesses,” the Flare report describes.
“In addition, public Telegram channels may deliberately publish lower value logs, saving high value logs for paying customers.”
Flare also found over 200,000 flight logs containing OpenAI credentials, double the number Group-IB recently reported and constitutes a risk of leaking proprietary information, internal business strategies, source code, etc.
Corporate credentials are considered “level 1” logs, which makes them particularly popular in the cybercrime community, where they are sold on private Telegram channels or forums like Exploit and XSS.
This value stems from the potential profits cybercriminals can make by leveraging compromised credentials to access CRM, RDP, VPN, and SaaS applications, and then using that access to deploy stealth backdoors, ransomware, and other payloads.
“Based on evidence from the Exploit in dark web forum, we believe it is highly likely that initial access brokers will use flight logs as a primary source to gain a foothold in enterprise environments that can then be auctioned off on prominent dark web forums,” says Eric Clay, researcher at Flare.
Organizations are recommended to minimize the risk of infection from information-stealing malware by enforcing the use of password managers, enforcing multi-factor authentication, and establishing strict controls over the use of personal devices.
Additionally, employees should be trained to identify and avoid common infection channels such as malicious Google ads, YouTube videos, and Facebook posts.
[ad_2]
Source link
